Research Article: 2021 Vol: 24 Issue: 6S
Before-after investigation on bank information security drill: Severity, susceptibility and fear
Cai Zhi Meng, Anyang Normal University, Management and Science University
Siti Khalidah Mohd Yusoff, Management and Science University
Brian Sheng-Xian Teo*, Management and Science University
Keywords
Extended Parallel Processing Model, Before-after Test, Information Security Drill, Information Security Awareness, Information Security Training
Citation Information
Meng, C.Z., Yusoff, S.K.M., & Xian, B.S. (2021). Before-after investigation on bank information security drill: Severity, susceptibility and fear. Journal of Management Information and Decision Sciences, 24(S6), 1-13.
Abstract
The application of various APPS leads to threats to bank information security, so there is an urgent need for an effective method to improve the information security awareness of bank employees. The purpose of this before-after investigation is to emphasize the importance of information security drill by comparing the same factors affecting bank Employees’ information security awareness based on extended parallel processing model (EPPM). Drawing on a before-after research design, this article examines the links of perceived severity, fear, perceived susceptibility, self-efficiency, response efficacy and bank employees’ information security awareness. Research results indicate that experience with infection of malwares can enhance bank employees’ defensive behavior, which proves information security drill is useful for information security education among bank employees. In the before-test, the relationships between perceived severity and response efficacy, perceived susceptibility and response efficacy, perceived severity and self-efficacy, fear and awareness are not significant. But in the after-test, not only all relationships are supported, but also all the t-values have increased. It indicate that information security drill can improve the risk-resisting ability and the banks can combine information security drill with vocational education, knowledge popularization, staff training, daily demonstration and advertising to reduce the financial and competing cost related with financial fraud and hacker attacks. It proves that drill can test the bank's existing information security rules, improve the tacit understanding of various departments, and achieve the best results with less consumption.
Introduction
One of the more critical aspects in financial industry is to ensure that the bank employees can understand the importance of protecting financial privacy when more mobile devices are applied in their daily financial work. More and more APPs for work, entertainment, finance, shopping, social interaction, learning, music production, etc. have become a part of many people's lives. Those APPs from the third parties have been installed in phones, tablets and personal computers, which may provide opportunities for all kinds of malware to steal users’ financial privacy. Although most bank employees have showed their concerns about the violation of financial privacy, the careless behavior or lack of awareness of financial privacy prevention often lead to the theft of financial privacy on mobile devices (Barth, 2019). Thus, the acts on financial privacy protection have become a popular research focus especially in financial privacy protection aspect since more and more financial frauds come into stage in recent years. Studies about financial privacy protection are carried out enormously in varieties of fields, including development of information software, hardware encryption and artificial intelligence recognition technology (Chen, 2019; Hajek, 2017; Zhi, 2019; Joon, 2019). However, in spite of all these efforts, methods or technologies’ development will be no use unless the bank employees’ information security awareness’s development is well implemented. Information security drills are the rehearsal activities of bank employees to perform their respective responsibilities and tasks when actual emergencies occur under the conditions of pre-virtual events. Simply, it is a coping exercise that simulates the occurrence of emergencies. Previous researches have proved that drills can effectively reduce casualties and property losses when emergencies occur, and quickly restore normal conditions from various disasters (Rahouti, 2020; Steve, 2020). This research is designed to compare the results of before-after information security drills in order to find what factors will improve bank employees’ information security awareness (ISA here-after). Plenty of previous researches have applied comparative method to different research fields, including international education, individual and institutional competitiveness, cultural difference and business strategy (Spiteri, 2018; Hamilton, 2017; Gromada, 2019; Warwick, 2013). Before-after test method is also applied to this research because a before-after evaluation can repeat the experiment under the same conditions and observe the degree of its influence on the experimental results, and by this way, we can avoid the accidental results, draw accurate and scientific conclusions. The before-after test is widely used in the field of scientific researches, such as road safety and traffic problems (Elvik, 2017; Zheng, 2019). Therefore, the purpose of this before-after investigation is to emphasize the importance of information security drill by comparing the same factors affecting bank Employees’ information security awareness based on extended parallel processing model (EPPM here-after). In this regard, it is intended to measure how perceived severity, fear, perceived susceptibility, self-efficiency and response efficacy’s role in bank employees’ information security awareness.
Literature Review
Varieties of previous researches and approaches have been applied into the field of protecting financial privacy and crisis management. Quite a lot of measures have been applied to information security protection. For example, banks reduce dependence on other’s technology and try to use their own software and hardware products as much as possible. Banks try to improve the security verification of the two important links of login and payment. Additionally, banks introduce electronic authentication technology and other measures to improve the information security of data during transmission. However, establishing a complete internal crisis management system to improve the risk awareness is more important than hardware capability improvement. Extensive previous researches prove that enhancing employees’ crisis management ability is an effective way to deal with emergencies (Melissa, 2017; Kubiak, 2019; Waele, 2020). Therefore, enhancing the professional quality of employees has reached consensus in various industries (Miller, 2005; Lucio, 2005; Lefebvre, 2009 Han, 2011; Kramera, 2018). At the technical level, some previous researches develop methods by integrating diverse data to look for fraud information in financial statement or announcement of listed companies (Chen, 2019), whereas some other previous researches focus on financial institutions’ internal fraud detection by measuring the probability of fraud (Joon, 2019). Based on rapid development of artificial intelligence technology, more and more researchers have applied face recognition and data mining technology in protecting financial privacy (Hajek, 2017). Barth, et al., (2019) prove that knowledge and other related factors are positively affected on mobile devices users’ online privacy behavior. As financial technology has become more popular in financial industry and social network is connecting everything from small communities to global ones (Jia, 2019), new Privacy security agreement protocols are proposed to filter out applet malware to prevent mobile devices from being infected by malware (Li, 2019). Since most of the bank employees are high performers, concerns of loss of financial privacy may lead to overload pressure, which in turn bring job dissatisfaction to them. Based on above discussion, only limited existing literatures have given detailed investigation on how to improve bank employees’ information security awareness by drill. Specially, it remains blanket in research of comparing the before and after test results to investigate bank employees’ crisis management ability in drill.
Extended Parallel Processing Model (EPPM) and Hypotheses
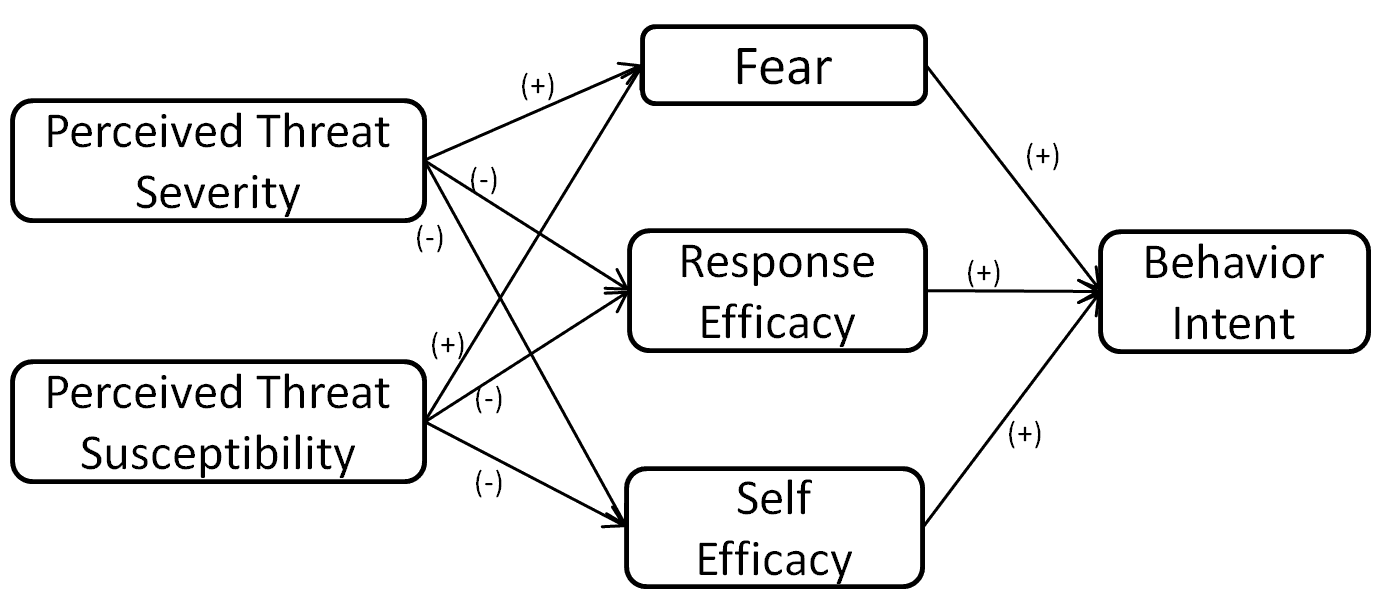
According to Protection Motivation Theory (PMT), the relationship between fear and action is not linear. PMT believes that when people take protective actions, there are also two sets of considerations, which are called threat appraisal and coping appraisal (Redmond, 2015). In the threat assessment, people will consider two specific questions: How severe is the threat (perceived threat severity)? How likely is I to suffer such a threat (perceived threat vulnerability)? In response assessments, people will consider two other specific questions: how effective is the solution recommended to me (perceived response efficacy)? Do I have the ability to act according to recommendations (perceived self-efficacy)?
Like PMT, the extended parallel process model (EPPM) also agrees that when faced with information about fear, people will pay attention to threat assessment and response assessment. However, EPPM has taken another step forward. It believes that the appeal of fear will also activate the other two parallel psychological processes. On the one hand, people may want to control the threat brought by fear, that is, threat control processes; on the other hand, people may want to control their perception of threats, that is, fear control processes. The two key conclusions of EPPM are: when the perceived threat is high and the effectiveness perception is high, the threat control process will be activated; when the perceived threat is high and the effectiveness perception is low, the fear control process will be activated. Extended Parallel Processing Model was designed to predict how individuals react to make multiple appraisals in a fear appeal situation. The first appraisal of EPPM is about the relative threat of a message, indicating that if messages are deemed to be threatening, individuals may then make a secondary appraisal. Thus, in secondary appraisal, individuals assess their ability to manage the presented threat.
EPPM theory is one of the most popular theories in explaining perception of efficacy and threat as key concepts to suggest the perception of efficacy and threat to affect results by interacting. Threat aspect consists of severity and susceptibility, whereas efficacy aspect consists of self-efficiency and response effectiveness. Specially, although logic behind the relations indicates that the critical point may occur at a proper time during exposure to some specific situations, the predictions or explanations about the same constructs may vary according to different people or events.
When bank employees perceive high threats, it means that bank employees are aware of the serious harm caused by information security. When their efficiency perception is high, it means that bank employees really think they have the ability to prevent information security disasters. At this time, they often make attempts to prevent disasters, that is, threat control. However, if the perceived threat is high and the effectiveness perception is low, although bank employees are aware of the serious harm caused by information security disasters, they do not consider themselves capable of controlling disasters. They will feel fear and despair. EPPM's inspiration to us is that information security training for bank employees should not only bring fear to them, but need to tell them that information security training is useful, and you can be trained to deal with and prevent information security risks in the future. Figure 1 shows the detailed construct information of EPPM theory. According to Protection Motivation Theory (PMT), the relationship between fear and action is not linear. PMT believes that when people take protective actions, there are also two sets of considerations, which are called threat appraisal and coping appraisal (Redmond, 2015). In the threat assessment, people will consider two specific questions: How severe is the threat (perceived threat severity)? How likely is I to suffer such a threat (perceived threat vulnerability)? In response assessments, people will consider two other specific questions: how effective is the solution recommended to me (perceived response efficacy)? Do I have the ability to act according to recommendations (perceived self-efficacy)?
Like PMT, the extended parallel process model (EPPM) also agrees that when faced with information about fear, people will pay attention to threat assessment and response assessment. However, EPPM has taken another step forward. It believes that the appeal of fear will also activate the other two parallel psychological processes. On the one hand, people may want to control the threat brought by fear, that is, threat control processes; on the other hand, people may want to control their perception of threats, that is, fear control processes. The two key conclusions of EPPM are: when the perceived threat is high and the effectiveness perception is high, the threat control process will be activated; when the perceived threat is high and the effectiveness perception is low, the fear control process will be activated. Extended Parallel Processing Model was designed to predict how individuals react to make multiple appraisals in a fear appeal situation. The first appraisal of EPPM is about the relative threat of a message, indicating that if messages are deemed to be threatening, individuals may then make a secondary appraisal. Thus, in secondary appraisal, individuals assess their ability to manage the presented threat.
EPPM theory is one of the most popular theories in explaining perception of efficacy and threat as key concepts to suggest the perception of efficacy and threat to affect results by interacting. Threat aspect consists of severity and susceptibility, whereas efficacy aspect consists of self-efficiency and response effectiveness. Specially, although logic behind the relations indicates that the critical point may occur at a proper time during exposure to some specific situations, the predictions or explanations about the same constructs may vary according to different people or events.
When bank employees perceive high threats, it means that bank employees are aware of the serious harm caused by information security. When their efficiency perception is high, it means that bank employees really think they have the ability to prevent information security disasters. At this time, they often make attempts to prevent disasters, that is, threat control. However, if the perceived threat is high and the effectiveness perception is low, although bank employees are aware of the serious harm caused by information security disasters, they do not consider themselves capable of controlling disasters. They will feel fear and despair. EPPM's inspiration to us is that information security training for bank employees should not only bring fear to them, but need to tell them that information security training is useful, and you can be trained to deal with and prevent information security risks in the future. Figure 1 shows the detailed construct information of EPPM theory.
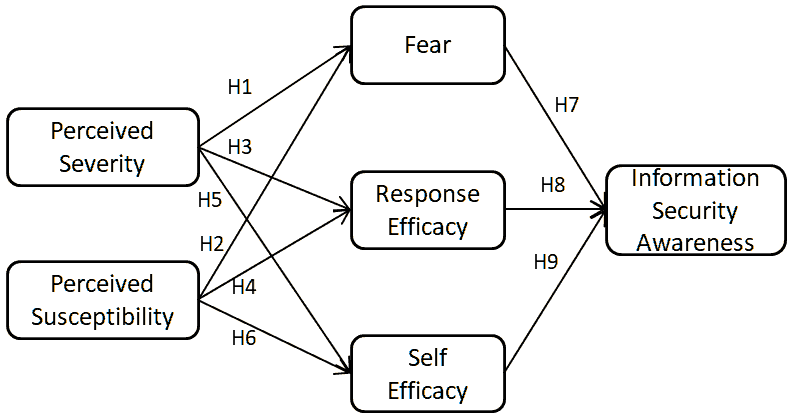
EPPM theory has already been applied into variety of research field. Drawing on EPPM theory, Shi & Smith (2015) prove that repeated exposure to certain fear appeal messages may lead to high infection probability. Redmond, et al., (2015) indicate that EPPM theory can help to why education and counseling are necessary for pregnancy healthcare. EPPM theory has been applied in varieties of research fields such as hearing protection (Kotowski, 2011; Smith, 2008), HIV prevention (Murray, 2001) teen pregnancy (Witte, 1997) and alcohol usage reduction (Moscato, 2001; Wolburg, 2001; Zisserson, 2007). In this research, the EPPM theory is adapted to environment of bank employees’ financial privacy protection awareness. EPPM indicates that the combination of perceived efficacy and perceived risk can lead to risk reduction behavior, whereas fears without positive efficacy instructions can cause maladaptive fear control instead of protective danger control. Therefore, EPPM is useful in financial data protection campaigns when theft of financial data poses a real or perceived threat to the whole financial systems. Safety training or education for financial practitioners using EMMP theory may offer actionable and realistic instructions about how to deal with risk and help bank employees develop useful and realistic solutions because quite a few of the bank employees have no idea about how to prevent malware attack in daily works and can’t estimate the possible serious consequences. Thus, financial privacy protection awareness is such an important research objective among financial practitioners that it is necessary to summarize the EPPM characteristics to investigate how financial practitioners’ behavioral change in a before-after test. Through a thorough analysis of EMMP for information security awareness (ISA), the optimized research model is shown in figure 2.
Since most of the constructs of EPPM remain in the optimized research model, the hypotheses are thus as follows.
In EPPM theory, perceived severity indicates beliefs related to the consequences of a particular event (Roberto, 2000) or to the importance or severity of the threat (Witte, 1998; Witte, 1996). It indicates the idea that bank employees hold toward to the importance or significance of the theft of financial data. When the bank employees’ perception of severity of theft of financial data increases, they may feel helpless in dealing with current dilemmas, and then they feel more fear. It will be a burden to financial practitioners. Specially, variations in perceived of information security threats could cause financial practitioners reassess the reaction to protect their financial data and make them become less efficient in response to malware and fight against malware with less self-efficacy. Therefore:
H1: Perceived severity positively affects fear.
H3: Perceived severity negatively affects response efficacy.
H5: Perceived severity negatively affects self-efficacy.
Perceived susceptibility refers to the belief in the risk of being threatened (Witte, 1998; Witte, 1996). Similar to perceived severity, perceived susceptibility indicates financial practitioners’ probability to encounter the malware. As financial practitioners’ perception of susceptibility increases and malware may become a burden to bank employees, they fear more in dealing with malware, and then, they may feel helpless to protect their financial data, become less efficient in response to malware and hardly find solutions to fight against it with self-efficacy. Therefore:
H2: Perceived susceptibility positively affects fear.
H4: Perceived susceptibility negatively affects response efficacy.
H6: Perceived susceptibility negatively affects self-efficacy.
Fear represents an internal negative emotional response, including the psychological and physical aspects caused by serious experience about threats (Witte, 1998; Witte, 1996). Fear has been proved in different previous researches about the positive or negative relationships with behaviors (Lorenc, 2012; Omer, 2018; Shin, 2017). The fear that financial practitioners perceive in dealing with malware may include different items, such as fear of economic loss, social level loss, performance failure and privacy loss. In order to conquer the fear, the bank employees may decide to learn more technics, reading more rules and seek useful tools to be more awareness in dealing with malware. Therefore:
H7: Fear positively affects ISA.
Self-efficacy indicates people's belief in their ability to respond to recommendations to avoid threats (Gore, 2005). Response efficacy represents a belief in the effectiveness of the proposed response in preventing or avoiding threats (McMahan, 1998; Roberto, 2000). Plenty of previous studies have proved the relationship between self-efficacy, response efficacy and behaviors in different fields including road safety (Tay, 2001), cyber security (Lawson, 2016) and health examination (Huang, 2016). Although some bank employees know how to use tools, software, rules and strategies in dealing with malware, they could probably feel confused or apprehensive about their own ability in using them due to the lack of high response efficacy and self-efficacy. Those who are self-efficacy and responsive may show a more positive view and are eager to seek more benefits to increase awareness of malware. Therefore:
H8: Response efficacy positively affects ISA.
H9: Self efficacy positively affects ISA.
Method of Research
This study aims to conduct empirical studies to ensure that bank employees' ability to perceive and respond to malware threats is an effective way to protect their financial information. The research was conducted on 163 bank employees who are in private banking department or personal financial business department, which means they visit customers frequently and deal with a lot of financial information every day in their own notebooks, tablets and desktops. In addition, the subjects of the experiment are to recruit and conduct applications to obtain clear data.
All the bank employees were volunteered for this experiment, and all laptops were provided by researchers. All bank employees who join the training courses should agree to a disclaimer, which is 1) I volunteered to attend the training course and fill in an anonymous questionnaire. 2) I openly and voluntarily accept information security drill in the training course. 3) All information is authorized to be disclosed. 4) There is no conflict of any interest. The training course and drill is approved by the relevant authorities.
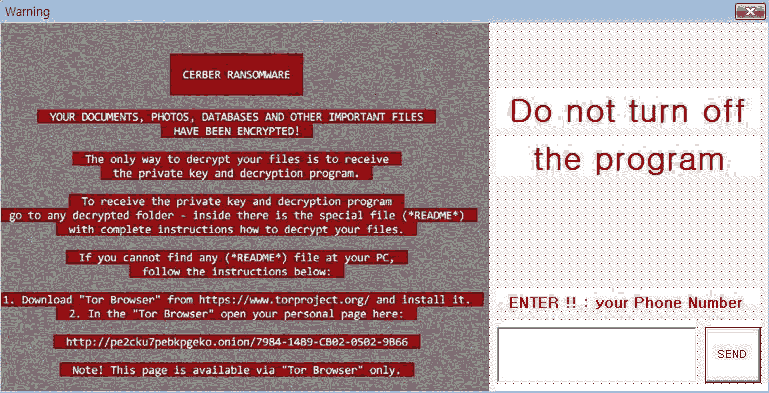
At first, they received three hours of information security training, and then were given a questionnaire about the adoption of financial security awareness to fill in. Secondly, they were asked to take a test about financial knowledge in one hour. They were told that the top twenty with the highest score can be rewarded our movie coupons. Thirdly, when they finished the test and click to submit, a window appeared to tell them that the laptops had been infected with a malware and all files had been encrypted. Fourthly, when they felt surprised by what had happened, the researchers came over to calm them down and told them this was part of the information security drill. Finally, they were invited to fill in the same questionnaire again. Anyway, all participants received four movie coupons as reward. This design is intent to verify the difference about how bank employees’ awareness after a real experience of financial security threatening. Figure 3 shows the warning information window (infectious warning window).
Measurement and Data analysis
The perceived severity factor is measured by three items. (“I believe that loss of financial privacy is extremely harmful.” “I believe that loss of financial privacy has serious negative consequences.” “I believe that loss of financial privacy is severe.”). We use 7-likert scale to test the items. 1 means strongly disagreement and 7 means strongly agreement.
The perceived susceptibility construct is measured by three items. (“I am at risk of loss of financial privacy.” “It is possible that I will get loss of financial privacy” “It is likely that I will get loss of financial privacy”). We use 7-likert scale to test the items. 1 means strongly disagreement and 7 means strongly agreement.
The fear construct is measured by three items. (“In my opinion, loss of financial privacy is very dangerous.” “The consequences of loss of financial privacy are serious.” “Loss of financial privacy will ruin my career and reputation”). We use 7-likert scale to test the items. 1 means strongly disagreement and 7 means strongly agreement.
The self-efficacy construct is measured by three items. (“I have the time to find ways to stop loss of financial privacy.” “I can easily find ways to avert loss of financial privacy.” “I am able to find ways to prevent loss of financial privacy”). We use 7-likert scale to test the items. 1 means strongly disagreement and 7 means strongly agreement.
The response efficacy construct is measured by three items. (“Learning privacy protection skills is an effective way to protect myself from loss of financial privacy.” “Learning privacy protection skills works to protect myself from loss of financial privacy.” “Complying with related financial privacy protection rules is an effective way to avoid loss of financial privacy.”). We use 7-likert scale to test the items. 1 means strongly disagreement and 7 means strongly agreement.
The information security awareness construct is measured by three items. (“I plan to take good care of financial privacy in my financial work.” “I intend to tell other people about the importance of protecting financial privacy.” “I would like to participate in financial privacy prevention training.”). We use 7-likert scale to test the items. 1 means strongly disagreement and 7 means strongly agreement.
Descriptive statistics
Of these 163 participants, 106 were men (65.0%) and 57 were women (35.0%). The majority of respondents were aged between 30 and 40 (42.3%). Table 1 shows the respondents of demographics. It is necessary to compare the constructs of before/after tests’ mean and standard deviation to find out the gaps between the same construct, because the gap shows the different responses to the same questionnaire in before/after tests. Table 2 shows the comparison of before/after mean and standard deviation.
| Table 1 Demographic Analysis |
|||
|---|---|---|---|
| Category | Subject | N | % |
| Gender | Male | 106 | 65.0% |
| Female | 57 | 35.0% | |
| Education Level | High School | 0 | 0% |
| Bachelor | 98 | 60.1% | |
| Master | 53 | 32.5% | |
| PHD | 12 | 7.4% | |
| Age | 23-30 | 52 | 31.9% |
| 30-40 | 69 | 42.3% | |
| 40-50 | 23 | 13.6% | |
| More than 50 | 19 | 12.2% | |
| Term of Financial Working Experience |
Less Than3 years | 31 | 19.0% |
| 3-6years | 87 | 53.4% | |
| 6-9 years | 35 | 21.5% | |
| More than 9 years | 10 | 6.1% | |
| Table 2 Comparison Of Before/After Mean & Standard Deviation |
|||||
|---|---|---|---|---|---|
| Construct | Before | After | Gap | ||
| Mean | SD | Mean | SD | ||
| Perceived Severity | 4.204 | 1.260 | 5.387 | 1.160 | 1.183 |
| Perceived Susceptibility | 3.983 | 1.183 | 4.885 | 1.244 | 0.902 |
| Fear | 5.212 | 1.387 | 5.674 | 1.050 | 0.462 |
| Self-efficiency | 3.610 | 1.460 | 3.862 | 1.540 | 0.252 |
| Response Efficacy | 3.608 | 1.235 | 4.724 | 1.355 | 1.116 |
| ISA | 4.605 | 1.464 | 5.330 | 1.160 | 0.725 |
Measurement Model and Results
Table 3 lists the alpha values for Cronbach, all of which exceed the recommended threshold of 0.7 to demonstrate its reliability. The composite reliability is also higher than the recommended threshold of 0.7 to prove its convergence (Sun, 2019). AVE is higher than the recommended threshold of 0.5 to prove its convergence effectiveness (Sun, 2020). The before-test results are in bracket whereas the after-test results are without blanket.
| Table 3 Convergent Validity, Composite Reliabilities Testing Results |
||||
|---|---|---|---|---|
| Construct | Item | Standardized Loading |
Composite Reliability (CR) |
AVE |
| Perceived Severity (PS) |
PS1 | 0.813(0.794) | 0.952 (0.912) |
0.809 (0.785) |
| PS2 | 0.920(0.841) | |||
| PS3 | 0.808(0.751) | |||
| Perceived | ||||