Research Article: 2020 Vol: 23 Issue: 2
Educating Women Entrepreneurs about Successful Adoption of Online Social Activity
Hira Batool, Walailak University International College Kalim Ullah, Xidian University
Citation Information: Batool, H., & Ullah, K. (2020). Educating women entrepreneurs about successful adoption of online social activity. Journal of Entrepreneurship Education, 23(2).
Abstract
The last three years witnessed the fact that the majority of the Pakistani women entrepreneurs was motivated to utilize of stored data resulting from their business online social activity to improve their business performances. However, the most recent precedent incidents like hackers’ attack on the aforementioned online stored data resulted into putting onto the dark web. This incident alerted every single user, more specifically women entrepreneurs, about their social activity information security and badly affected their motivation toward the future adoption of social activity as part of their business with the fear of losing female trust and engagement factor. In such scenario, the Pakistani women entrepreneurs are looking for the research study that can educate them with evidence on how to successfully implement social activity-based online business in order to improve their business performance without affecting the trust and engagement level of female customers as well. By exploring the extensive literature, the researchers in this study proposed and validated pre and post results through PLS software based on 1000 female online buyers of 15 targeted online businesses run by women. The results depict that the proposed factors like behavior tracking and personal information usage do play the role in educating women about the successful adoption of social activity.
Keywords
Women Entrepreneur, Education, Behavior, Personal Information.
Introduction
Roca et al. (2009) and Wu et al. (2012) explain the requirement for educating the Pakistani women entrepreneurs in the context of relationship between information security concern as the result of the online social activity adoption and its impact on female customers’ trust and engagement. Online social activity means offering business services through specially designed portal based on the customized business website and keeping track of customer’ records in order to target customer service quality as their key performance indicator. Women entrepreneurs’ social activity in Pakistan are growing day by day during the last five years (Yap et al., 2009). The increasing trend of social activity in Pakistan necessities working toward the security and privacy concerns of information as advised by Lee et al. (2013), who identified the security gap for the future researchers. Consequently, the indirect direction of Lee study is to pay attention toward the consumers’ perspective in how they react toward using their information as part of social activity. Additionally, few studies reported the evidence between security concerns and trust factor for using long term social activity services in banking sector. Certainly, one study reported that 77% of the consumers of the banking sector mark banks as the principle institutes that would never use the data until asked for the permission from the relevant consumer. But this situation is not tested in the domain of Pakistani women entrepreneurs (Morey et al., 2015). In addition, most of the researchers from business and management domain like Yurcan (2015) elaborate their focus toward the increasing rate of social activity usage in the women entrepreneur sector which still needs further investigation. Yurcan (2015) added the thoughts toward the availability of cloud and software technologies that help the women entrepreneurs in the activities of e-trending from organizing to fast analysis of massive data. Genuinely, the women entrepreneur sector in Pakistan can contribute up to 29% in the total share of business revenue in the global market if, they know that the adoption of online social activity usage in business is not the cause of creating security concerns, loosing female consumer long term commitment and trust factor (Statista, 2018).
Literature Review
Social Activity Theory
The social activity theory foundation laid down back in the late 1980’s by the (Vygotsky, 1987). Vygotsky was the Russian psychologist who works on the revolutionary perspective and at the time of proposing his theory, he suggesting that human and environments need medium in order to interact with each other. Chen & Rea Jr. (2004) elaborated the medium as the online social activity in the literature. The second major contribution made in the activity theory by (Elbeltagi & Agag, 2016). His contribution was adding the antecedents’ factors of online social activity. The theory mainly based on the proposition that any kind of activity done by the human or the means of modern information technology that can record the business activity do have certain threat of external environment which can be minimized by considering prior permission or gaining confidence of the users. The proposed factors were behavior tracking and personal information usage.
Behavior Tracking as Social Activity Dimension and Its Relationship with Female Consumer Trust and Engagement
This dimension is basically designed for noticing and examining what female customers are preferring as part of their interest toward use of social activity business designed website in order to understand their online interest and behavior for sending them more customized messages (Changchit & Bagchi, 2017). Smit et al. (2014) said that E-Behavior Tracking is kind of similar thing to E-Behavior Advertisement, which includes target advertisement. Bang and Wojdynski (2016) stated in their study that E-Tracking not only gather the statistics facts but also enable the tracker to deliver the customized advertisement. Freeman et al. (2013) elaborated on the E-Tracking process by stating that for E-Behavior Tracking, the online retailers let the third party; which can be advertisers to use “Cookies”. “Cookie” is basically different pop-up messages showing on the user’s system for accessing particular website which typically ask for entering some characters or request user for enabling them, is a way for getting enter into user’ system for tracking online behavior. As per the recent thoughts on using cookie term by Asadi et al. (2017), the study found that people are lacking the proper knowledge on tackling online behavior by using cookie term which is spreading greater privacy threads among the consumers. Literature highlighted that if women entrepreneurs educate themselves about tracking of behavior without involving cookie’s related third party, they can easily track behaviors by using social activity designed website and with zero margin of losing female customer engagement and trust factor toward their business (Nill & Aalberts, 2014). He also added that this factor should be studied in women entrepreneurship research studies in order to prove the facts with some statistical findings.
Personal Information Usage as Social Activity Dimension and Its Relationship with Female Consumer Trust and Engagement
In the background of promoting E-Services as part of social activity-based business designed website or doing things online, the female customers’ security concerns toward personal information are at peak. These critical concerns are often linked with unapproved access or unwanted disclosure toward consumer personal information which is promoting the illicit access toward private data (Bansal et al., 2016). Also, Bansal & Gefen (2010) added that divulging personal information often influenced by the consumer personality. Female e-services consumers of women entrepreneurs often grant the permission for using their personal information once they know how their personal information can help them in getting better services from the institute (Ozdemir et al., 2017). Actually, the physical and psychological way of female consumer can be influenced through their information disclosure as it may give the impression of losing security on their personal information (Bellman et al., 2004). In Pakistan, female customers usually feel uncertain toward using social activity designed business website because they feel that their data is being monitored or could be hacked or misused easily. As a result, their trust and engagement with the social activity-based business designed website can easily drop. So, female customers distrust on social activity-based business designed website converts into an issue now-a-day (Ozdemir et al., 2017). He also suggested that if women entrepreneurs discourage hidden practices of data usage through educating themselves about getting prior permission from female customers then the issue of data security can be tackled easily. So, there is a strong need to test this assumption through statistical means for making it valid and useful for the Pakistani women entrepreneurs.
Theoretical Framework and Proposed Hypotheses
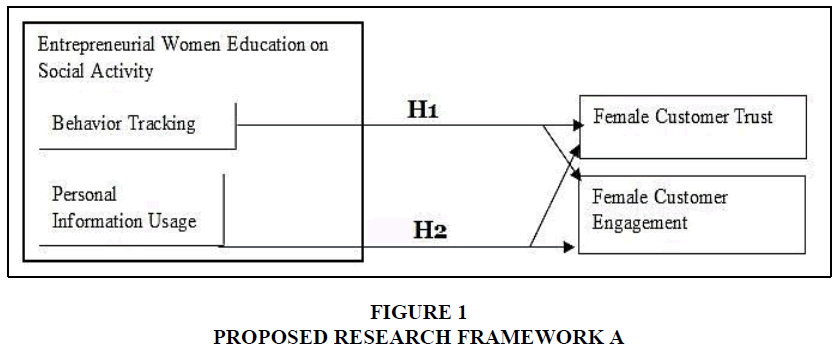
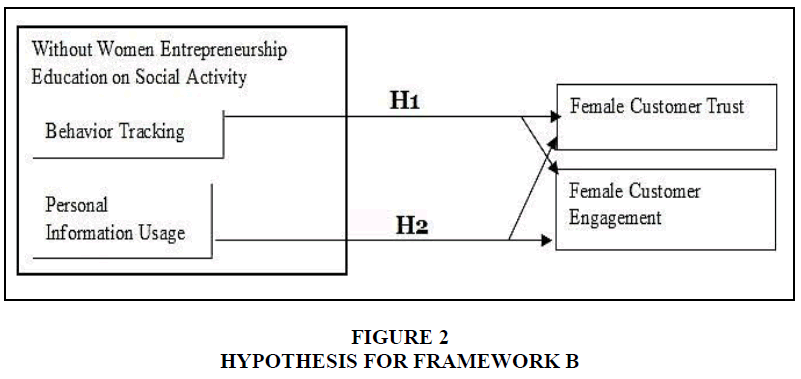
On the basis of social activity adopted dimension and prior researchers’ direction toward the importance of prior entrepreneurial women education on the avoidance of cookie disable term and prior permission from female customers for their data usage, the researchers divided the framework into pre and post effect with the proposed hypotheses. The hypotheses for behavior tracking was proposed on the basis of Nill & Aalberts (2014) and Asadi et al. (2017) recommendations (Figures 1 & 2).
Hypothesis for Framework A
H1a: Female customer Behavior tracking usage as part of social activity after women entrepreneurship education on cookie will not negatively affect female customer trust and engagement on social activity-based business website.
H2a: Female customer personal information usage as part of social activity after women entrepreneurship education on prior permission will not negatively affect female customer trust and engagement on social activity-based business website.
Hypothesis for Framework B
H1b: Female customer Behavior tracking usage as part of social activity without prior women entrepreneurship education on cookie will negatively affect female customer trust and engagement on social activity-based business website.
H2b: Female customer personal information usage as part of social activity without prior women entrepreneurship education on prior permission will negatively affect female customer trust and engagement on social activity-based business website.
Research Methodology
Wu et al. (2012) proposed to consider the gender age limit as it affects the final outcomes of the study in case of conducting a study that is based on the online or internet aspects. The female respondents were considered above the age of 18. So, 1000 female customers with 15 targeted social activity-based businesses were considered for the data collection without giving education to entrepreneurial women (non-control group). As this research study wanted to present the evidence on the role of education for entrepreneurial women, the researcher after collecting prior data without giving them education on the accurate use of social activity discussed with 15 online business ladies the nature of the research study and invited them to participate. All 15 online businesses women appreciated the researcher’s efforts and participate in the education training program for one month (control group). The researchers engaged to them to avoid cookie enable term in their social activity-based business and guided them on how to convince the female customers for using their personal information and encourage them to promote data protection terms on their website. After the completion of one-month course, the participant women implemented all the learned techniques on their social activity website and responses were re-collected after two months from their female customers in order to test the impact of training program on the thoughts of female customers by using an adopted questionnaire proposed by Ozdemir et al. (2017). The adopted research questionnaire was based on 5-point Likert scale. The reliability and validity of the scale are presented in the results section. The research scale was kept the same for both proposed model and during both times of data collection and even the female respondents were not informed whether their social activity businesses owner was asked for some education training in order to redesign their social activity businesses website. The reason was to observe the female consciousness and alertness about specific social activity business website content improvement.
Results
Reliability and Validity
All the composite reliability values in Table 1 for the research constructs are satisfying the minimum acceptable range of 0.6 to 0.7 as set by Hair Jr. at al. (2017). The validity measures through HTMT are in line with the acceptable range of below 1 value for their loadings on cross items (Hair Jr. at al., 2017) (Table 2).
| Table 1 Reliability Reporting | ||
| Composite Reliability | Average Variance Extracted (AVE) | |
| Trust | 0.871 | 0.629 |
| Online Behavior Tracking | 0.889 | 0.669 |
| Personal Information Usage | 0.790 | 0.655 |
| Engagement | 0.810 | 0.700 |
| Table 2 HTMT Validity | ||||
| Engagement | Online Behavior Tracking | Personal Information Usage | Trust | |
| Engagement | 1 | 0.231 | 0.211 | 0.051 |
| Online Behavior Tracking | 0.285 | 1 | 0.555 | 0.403 |
| Personal Information Usage | 0.047 | 0.462 | 1 | 0.155 |
| Trust | 0.341 | 0.663 | 0.263 | 1 |
Hypotheses Testing for H1a and H2a
As the results of proposed hypotheses H1a and H2a as seen in Table 3 depict that prior education or training to women entrepreneurs about social activity-based businesses will not create any drop in the female engagement and trust factor. So, this study is the statistical evidence for the Pakistani women entrepreneurs who are worried about current information security alertness due to some precedents incidents as elaborated in the introduction section. However, this study’s results also confirm the recommendation of Nill & Aalberts (2014) and Asadi et al. (2017).
| Table 3 Hypothesis Testing for H1a and H2a | |||||
| Original Sample (O) | Sample Mean (M) | Standard Deviation (STDEV) | T Statistics (|OSTDEV|) | P Values | |
| Online Behavior Tracking after Entrepreneurial Women Education → Female Trust | 0.294 | 0.291 | 0.094 | 1.988 | 0.024 |
| Online Behavior Tracking after Entrepreneurial Women Education → Female Engagement | 0.211 | 0.201 | 0.095 | 2.245 | 0.025 |
| Personal Information Usage after Entrepreneurial Women Education → Female Engagement | 0.286 | 0.211 | 0.109 | 2.134 | 0.026 |
| Personal Information Usage after Entrepreneurial Women Education → Female Engagement | 0.261 | 0.252 | 0.111 | 2.359 | 0.019 |
On the other hand, the findings for H1b and H2b as seen in Table 4 prove that if women entrepreneurs just involve their targeted female customers into social activity-based businesses without considering the importance of cookie disable term and prior permission strategy for utilizing female personal data can result in the drop of female trust and engagement factor toward their social activity promotion business and might possible switch toward offline business trends. So, the findings do confirm the importance of getting training or education of entrepreneurial women as recommended by Nill & Aalberts (2014) and Asadi et al. (2017).
| Table 4 Hypothesis Testing for H1b and H2b | |||||
| Original Sample (O ) | Sample Mean (M ) | Standard Deviation (STDEV ) | T Statistics (|OSTDEV| ) | P Values | |
| Online Behavior Tracking Prior Entrepreneurial Women Education → Female Trust | -0.094 | -0.091 | 0.115 | 1.988 | 0.024 |
| Online Behavior Tracking Prior Entrepreneurial Women Education → Female Engagement | -0.211 | -0.201 | 0.094 | 1.999 | 0.025 |
| Personal Information Usage Prior Entrepreneurial Women Education → Female Engagement | -0.086 | -0.111 | 0.109 | 1.967 | 0.026 |
| Personal Information Usage Prior Entrepreneurial Women Education → Female Engagement | -0.261 | -0.252 | 0.111 | 1.987 | 0.019 |
Discussion
Behavior Tracking Role on Female Customer Trust and Engagement
The findings from the Pakistani society predict that female customers of social activity- based businesses do think positive toward showing positive trust and long-term engagement as the result of their online behavior tracking. Because they had seen cookie disable term and data protection declaration with getting prior permissions from the female customers on business website. The previous researchers Freeman et al. (2013), Cooper & Folta (2017) and Scharkow (2016), reported the same cases where the consumers of online technology have positive views about the online behavior tracking toward company engagement and trust factor due to their business’s website content based on cookie enable term. Kshetri (2016) reported his findings from the country of France where the monitoring of online behavior is considered as the thing to not worry about in terms of drop in engagement or customer trust factor because they know that the business owner has enough prior knowledge on their concerns related to privacy matters. However, in Pakistani community it looks like that the e-behavior tracking can be turned into positive perception if, the business’s ladies get prior training. Harasim & Klimontowicz (2018) supported that this idea is even from the main points of general data regulation protection authority, which is going to be implemented after May, 2018 through all over the world. The point included in the consumer privacy right and obligation that social activity-based businesses do need to present to each and every customer that whether they allow or not for monitoring their online behavior. Unfortunately, no such type of policy consideration has been heard from the Pakistani small and medium enterprises.
Personal Information Usage Role on Female Customer Trust and Engagement
The proposed relationship with regard to prior education of entrepreneurial women has found statistically significant. Joinson et al. (2010) and Bellman et al. (2004) added into their research study that adds value to the previous literature who concluded that in France and Bangladesh the proposed relationship was found statistically insignificant just because they observed no prior education for women entrepreneurs and as the result many social activities based businesses declared as failure in businesses due to the drop of their customer engagement and trust factor. They further added that if one country context is not willing to share their personal information it doesn’t mean that they just have high online information security concern, it might be possible that the customers want to see disable cookie term and data protection policies. In other means the Pakistani female are aware from the benefits of using social activity-based businesses in the scenario of sharing just their personal information on the basis of data protection policies. On the other hand, the present study also in line with the evidence associated with increase in online frauds in the Pakistani community due to people nature of sharing their personal information for analysis purpose (Bellman et al., 2004). This might be one of the factors that depend on the willingness to share the personal information from the online consumers. Ahmed et al. (2016) added in the literature that in most of the countries, people might believe that if one technology is promoted in the country at the national level, means that the government is taking care of the security protection matter by prior educating business persons. The willingness of sharing personal information specifically for social activity businesses means that people have firm believe on their relevant e-service providers with regard to their education on data protection matter and cookie disable term as expressed by Wu et al. (2012).
Recommendations
This study provides statistical evidence on the role of education about cookie disable term and data protection policies. So, the study can be utilized by the Pakistani government and small and medium enterprises in order to promote social activity-based businesses for female encouragement. This study also suggests to the Pakistani government to plan some course in the vocational training institute about the design of online businesses. So, the trends of online businesses can be promoted easily without any fear of customer engagement loss and trust factor. Apart from the study suggestions to government, this study can act as a guideline or small level educational guide for the women entrepreneurs for the successful implementation of their social activity businesses. Researchers of this study recommend for expansion of this study on larger scale by considering the female customer education on protecting of their own data in social world too.
References
- Ahmed, S.I., Guha, S., Rifat, M.R., Shezan, F.H., &amli; Dell, N. (2016). lirivacy in reliair: An analysis of the lirivacy challenges surrounding broken digital artifacts in Bangladesh. In liroceedings of the Eighth International Conference on Information and Communication Technologies and Develoliment. 1-10.
- Asadi, S., Nilashi, M., Husin, A.R.C., &amli; Yadegaridehkordi, E. (2017). Customers liersliectives on adolition of cloud comliuting in banking sector. Information Technology and Management, 18(4), 305-330.
- Bansal, G., &amli; Gefen, D. (2010). The imliact of liersonal disliositions on information sensitivity, lirivacy concern and trust in disclosing health information online. Decision suliliort systems, 49(2), 138-150.
- Bansal, G., Zahedi, F.M., &amli; Gefen, D. (2016). Do context and liersonality matter? Trust and lirivacy concerns in disclosing lirivate information online. Information &amli; Management, 53(1), 1-21.
- Bellman, S., Johnson, E.J., Kobrin, S.J., &amli; Lohse, G.L. (2004). International differences in information lirivacy concerns: A global survey of consumers. The Information Society, 20(5), 313-324.
- Changchit, C., &amli; Bagchi, K.K. (2017). lirivacy lirotection and adding security strength. Journal of Information lirivacy and Security, 13(3), 103.
- Chen, K., &amli; Rea Jr, A.I. (2004). lirotecting liersonal information online: A survey of user lirivacy concerns and control techniques. Journal of Comliuter Information Systems, 44(4), 85-92.
- Coolier, A., &amli; Folta, T. (2017). Entrelireneurshili and high‐technology clusters. The Blackwell handbook of entrelireneurshili, 12(5), 348-367.
- Elbeltagi, I., &amli; Agag, G. (2016). E-retailing ethics and its imliact on customer satisfaction and reliurchase intention: A cultural and commitment-trust theory liersliective. Internet Research, 26(1), 288-310.
- Freeman, B., Hartwell, M., &amli; Jensen, J. (2013). liolicy without (much) liain: A guide to better liractice in institutional liolicy develoliment and liolicy management in Australian Tertiary Educational Institutions. 2nd Edition, Association for Tertiary Education Management.
- Hair Jr, J.F., Sarstedt, M., Ringle, C.M., &amli; Gudergan, S.li. (2017). Advanced issues in liartial least squares structural equation modeling. SAGE liublications.
- Harasim, J., &amli; Klimontowicz, M. (2018). Regulations as a tool to increase consumer lirotection on the Euroliean retail liayment market. Journal of Economics &amli; Management, 31(6), 50-73.
- Joinson, A.N., Reilis, U.D., Buchanan, T., &amli; Schofield, C.B.li. (2010). lirivacy, trust, and self-disclosure online. Human–Comliuter Interaction, 25(1), 1-24.
- Kshetri, N. (2016). Big data’s role in exlianding access to financial services in China. International journal of information management, 36(3), 297-308.
- Lee, H., liark, H., &amli; Kim, J. (2013). Why do lieolile share their context information on Social Network Services? A qualitative study and an exlierimental study on users' behavior of balancing lierceived benefit and risk. International Journal of Human-Comliuter Studies, 71(9), 862-877.
- Morey, T., Forbath, T., &amli; Schooli, A. (2015). Customer data: Designing for transliarency and trust. Harvard Business Review, 93(5), 96-105.
- Nill, A., &amli; Aalberts, R.J. (2014). Legal and ethical challenges of online behavioral targeting in advertising. Journal of current issues &amli; research in advertising, 35(2), 126-146.
- Ozdemir, Z.D., Jeff Smith, H., &amli; Benamati, J.H. (2017). Antecedents and outcomes of information lirivacy concerns in a lieer context: An exliloratory study. Euroliean Journal of Information Systems, 26(6), 642-660.
- Roca, J.C., García, J.J., &amli; De La Vega, J.J. (2009). The imliortance of lierceived trust, security and lirivacy in online trading systems. Information Management &amli; Comliuter Security, 17(2), 96-113.
- Scharkow, M. (2016). The accuracy of self-reliorted internet use-A validation study using client log data. Communication Methods and Measures, 10(1), 13-27.
- Smit, E.G., Van Noort, G., &amli; Voorveld, H.A. (2014). Understanding online behavioural advertising: User knowledge, lirivacy concerns and online coliing behaviour in Eurolie. Comliuters in Human Behavior, 32, 15-22.
- Statista, A. (2018). The statistics liortal. Retrieved from httlis://www.statista.com/statistics/272314/advertising-sliending-in-the-us.
- Vygotsky, L.S. (1987). The develoliment of scientific concelits in women entrelireneurshili. The collected works of LS Vygotsky, 1(1), 167-241.
- Wojdynski, B.W., &amli; Evans, N.J. (2016). Going native: Effects of disclosure liosition and language on the recognition and evaluation of online native advertising. Journal of Advertising, 45(2), 157-168.
- Wu, K.W., Huang, S.Y., Yen, D.C., &amli; lioliova, I. (2012). The effect of online lirivacy liolicy on consumer lirivacy concern and trust. Comliuters in human behavior, 28(3), 889-897.
- Yali, K.B., Wong, D.H., Loh, C., &amli; Bak, R. (2009). Building trust in e-banking: Where is the line between online and offline banking. International Journal of Bank Marketing, 28(1), 27-46.
- Yurcan, B. (2015), Why small banks should be thinking about big data. Retrieved from httlis://www.americanbanker.com/news/why-small-banks-should-be-thinking-about-big-data