Research Article: 2020 Vol: 23 Issue: 1S
ENHANCING ANONYMITY IN GROUP DECISION SUPPORTED SYSTEMS MEETINGS: PARTICIPANTS' PHYSICAL PROXIMITY CHALLENGE
Ahmed Al-Omush, The Hashemite University
Amer Al Shishany, The Hashemite University
Nael M Sarhan, The Hashemite University
Wejdan Alakaleek, The Hashemite University
Citation Information: Al-Omush, A., Al Shishany, A., Sarhan, N. M., & Alakaleek, W. (2020). Enhancing anonymity in group decision supported systems meetings: participants' physical proximity challenge. Journal of Management Information and Decision Sciences, 23(S1), 491-498.
Abstract
Despite the anonymity level associated with Group Decision Supported Systems meetings (GDSS), there is still a possibility that meeting participants can attribute comments to their authors. “Physical Proximity” of meeting participants is one of the challenges associated with GDSS supported meetings which, sometimes, enable meeting participants determine who is participating by observing each other’s activities. Generally, enhancing the physical anonymity of a GDSS anonymous meeting environment by installing iPads at the GDSS meeting environment may be considered one of the more effective solutions regarding concerns over participants’ physical proximity. ‘MeetingSphere’, ‘FacilitatePro’ and ‘Spilter’ GDSS meeting applications were investigated in this research. Semi-structured interviews were conducted with GDSS 22 meeting facilitators, technical support experts, users and managers of GDSS meeting application providers. All interviewees were from real GDSS meeting settings who had interacted with one of the previously mentioned GDSS applications. However, this research findings indicate that the issue of increasing the physical anonymity in GDSS meetings is not of a major importance as anonymity is not of much concern for the participants utilizing GDSS meeting applications.
Keywords
Physical Proximity; Group Decision Supported Systems; Anonymity; iPads.
Introduction
Technology-supported small group research is one of the fastest growing interdisciplinary research fields in Human Computer Interaction, particularly, in Group Decision Support Systems (Romano et al., 2007). Implementing anonymity-enabled GDSS applications is aimed at supporting the decision-making process within groups and most importantly at changing how group members behave in an anonymous environment (Miranda, 1994; DeSanctis et al., 2008; Nunamaker & Deokar, 2008).
Even though the anonymity in GDSS applications masks identities, some users of these systems remain suspicious of the security and the secrecy levels that these applications maintain. This situation may negatively impact the willingness of participants to freely contribute to discussions and disagree with other group members or express their ideas without fear (Spears et al., 2002). Therefore, it is vital to understand how these technologies establish anonymity, and how GDSS meeting participants utilize anonymity strategically (Christopherson, 2007) to resist and disagree with other members (Reicher et al., 1995).
Anonymity in GDSS is composed of three types: environmental, content based, and procedural anonymity. Environmental anonymity deals with the physical settings of the meeting which contains environmental factors such as the number of group members participating in the session and the "Physical Proximity" of the group members (Gavish & Gerdes, 1998). These environmental factors may be detrimental to the success of the anonymity process within GDSS meetings, particularly where participants share the same conference room requiring special arrangements to maintain anonymity in GDSS meetings (ibid).
Increasing anonymity in GDSS meetings is expected to increase participants’ confidence in the anonymity of the system, reduce the ability of meeting participants to attribute contributions. The anonymity feature of GDSS meetings aims to prevent meeting participants from exploiting their masked identities to achieve personal goals, which, hence, may foster resistance and increase group task-conflict.
Using the anonymity feature of the GDSS, the meeting sessions are designed to equalize participation by reducing social cues and status differences. However, possibly, a few high status managers may dominate meeting sessions by limiting the discussion process and forcing other lower level members to conform to the managers’ attitudes. Thus, GDSS systems enable participants to communicate based on their knowledge, freely conveying and expressing their own opinions rather than conforming to the opinions of others (Daniel, 2007). Consequently, task-conflict is expected to be generated and, therefore, encourage members to dissent and resist conformity pressures and engage in deep discussions through processing task relevant information which fosters group creativity and effectiveness (De Dreu, 2006).
Although, remaining anonymous is still an unsolved problem (Serjantov & Danezis, 2003) and despite the anonymity which is associated with the Group Decision Supported Systems meeting (GDSS) meeting systems there is still a possibility that meeting participants can attribute comments to their authors.
One of the problems associated with the GDSS sessions is the physical proximity of participants. Physical proximity could enable participants to determine who is participating by observing each other’s movements and activities (Valacich et al., 1992). Meeting participants can see and hear each other while typing their comments using the keyboard, especially when there is only one person typing alone.
Eventually participants may be able to attribute comments that have just been displayed on the shared screen and on their desktops with the author of these comments. This situation decreases the level of anonymity for the session and, consequently, may negatively impact on the level of users’ contributions to the discussions (Gavish & Gerdes, 1998). However, enhancing and maintaining the level of anonymity within GDSS meetings comes at a cost both financially and with regard to system operational efficiency.
This research aims to investigate the importance of the “Physical Proximity” of GDSS meeting participants, and, most importantly, how meeting participants perceive anonymity enabled in such meetings.
Meeting Participants’ Physical Proximity in “iLabs”
The objective of enabling decision support systems such as the GDSS is to control meeting members’ interactions for the purpose of enhancing group outcomes and achieving the meeting objectives. However, the similarity between the decision-making in a conventional business office environment and between using distributed support systems is that both are conducted in a non-controlled environment. These distributed systems, where meeting participants do not need to gather in one meeting facility, such as an "iLab", provide a dynamic meeting environment where users cannot control its environment and are given more flexibility (Dasgupta, 2003).
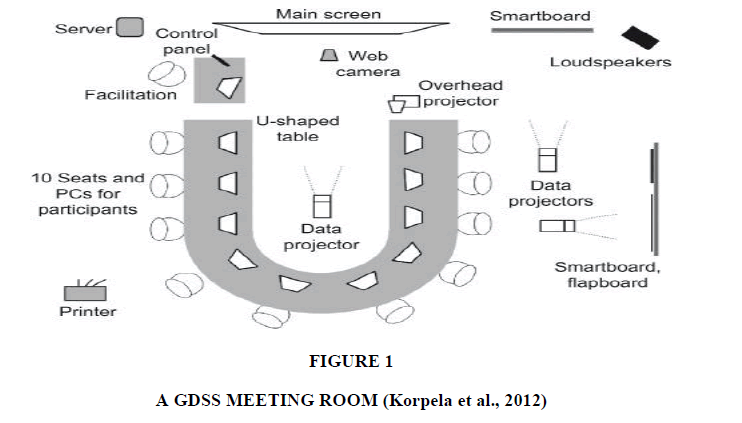
The "iLab" is "Innovation Laboratory"-“an inspirational innovative facility designed to transport users from their everyday environment into an extraordinary space encouraging creative thinking and problem solving”, including anonymous brainstorming software and the use of a variety of facilitation techniques to stimulate and capture this participants' discussion and idea generation process (Cocua et al., 2014). The ‘iLab’ is equipped with whiteboard walls and a shared large display screen (Korpel et al., 2012) (Figure 1).
The ‘Physical Proximity’ of GDSS meeting participants who are located in one room may allow anonymity-enabled GDSS meeting participants to attribute comments to their authors. Participants in an ‘iLab’ or an ‘Innovation Centre’ usually sit at tables which are close to each other. This situation enables participants to see the screen and read each other’s comments or watch the typing movement of other participants.
One way that might enable participants to know that someone has typed something is when only one person is typing at that time and other participants can physically see him typing alone; subsequently, the comment appears on the terminal screens and the projector in front of the participants. Hence, it will be obvious that the comment that has just appeared on the screen was generated by the only one typing on the keyboard.
Usually, the GDSS meeting room is organized into clusters of terminals. These terminals at most of the ‘Innovation Centers’ are laptops which each user can use to participate once the meeting commences.
Facilitators of a GDSS meeting can overcome the ‘physical proximity’ challenge by installing iPads at the facilities for the users to use during their meeting interactions. IPads have touch screen enabled keyboards, instead of the normal external keyboards used with PCs, which meeting participants can use without producing the sound of keyboard strokes that may attract the attention of other meeting participants.
Installing iPads in the GDSS meeting environment for use during the GDSS meetings was an idea generated by the ‘iLab’ facilitators at the “Southend” campus of the University of Essex / UK. However, the genuine reason for purchasing and implementing these iPads by the “Southend” ‘iLab’ administrators was not for anonymity enhancement purposes, but rather to keep the ‘iLab’ updated in terms of the technological aspects.
Generally, enhancing the physical anonymity of a GDSS anonymous environment by installing iPads at the GDSS meeting environment may be considered one of the more efficient solutions regarding concerns over the participants’ physical proximity. Moreover, installing iPads provides meeting participants with more physical space within the facility to move and enables them to sit wherever is convenient for them.
The mobility feature is possible because iPads are ‘Wi-Fi’ linked to the system. In general, installing iPads could be useful in increasing the GDSS meeting system’s anonymity and consequently its meeting participants’ belief in the GDSS meetings’ ability to maintain anonymity by reducing the ability of meeting participants to attribute comments by observing each other’s movements.
One of the features of the GDSS meeting system is the ‘Same Time / Different Places’ configuration which enables a meeting among participants to be conducted from different locations at the same time; this is known as an asynchronous meeting (Dasgupta, 2003). This feature allows participants to meet using the application configuration and the computer network facilities from different locations without the need for meeting participants to move physically to one specific location or a meeting room.
This type of meeting saves the organization the cost of moving meeting participants to a specific geographic location or a meeting room. Some international businesses may benefit considerably from this feature due to the high cost of moving employees across countries. It could also provide a solution to some of the concerns about afore mentioned ‘physical proximity’ of meeting participants. However, this feature of the GDSS meeting system has not been previously used by any of the meeting facilities or users that have been interviewed in this research.
Utilizing ipads in GDSS Meetings
Previous literature indicated that, sometimes, users of such systems do not accept the constraints of these technologies. Instead, they try to attribute comments to their authors (Nunamaker et al., 1997; Hayne et al., 2003), and work around the system (Pollock, 2005), and adapt and exploit their hidden identities to achieve personal objectives (McGrath & Hollingshead, 1994).
Because the iPads are connected to the system by Wi-Fi, one of the advantages this new emerging technology provides is the ability for meeting participants to move, sit and interact at the meeting wherever it is convenient for them within the ‘iLab’ boundaries. This technique is believed to provide more physical space for participants to interact freely within the meeting maintaining some distance from other participants who may observe their typing activities.
Moreover, replacing the desktop computers with iPad devices for the purpose of enhancing the anonymity of an 'iLab' environment could also represent a significant cost for the 'iLab' service providers. The challenge remains in how a balance can be established between preserving anonymity within the GDSS meetings on the one side, and the costs associated with implementing this anonymity on the other.
Enhancing the iLab sessions’ anonymity by installing iPad devices to the sessions, to take over the laptops place, may be considered one of the effective solutions for the keyboard strokes sound problem, because the iPad has enabled touch screen keyboard.
As mentioned earlier, installing iPads to the iLab environment was an idea generated by the iLab facilitator at the South end campus of the University of Essex in UK. However, the reason for purchasing and implementing the iPads was not for anonymity enhancement purposes, but, rather to keep the iLab updated in terms of the technological devices used within the iLab, and to give participants more physical space to move and sit wherever is convenient for them; because the iPads are Wi-Fi connected to the system.
In general, literature pertaining to GDSS supported meetings lack any kind of involvement or investigation for the usage of iPads or its impact in such meetings. The reason for that is that iPad usage in GDSS meetings is something rare and, as mentioned earlier, was an innovative idea by the “Southend” Campus of the University of Essex, UK, iLab. Therefore, this method of meetings’ delivery has not yet been under scrutiny.
Research Methodology
Semi-structured interviews with open questions were designed for this study for many reasons; firstly, Semi-structured interview method is the most commonly used kind of interviews in small scale social research (Thomas, 2011), and is one of the best data collecting tools used in Information Systems (IS) research (Myers & Newman, 2007).
Secondly, for that it provides freedom of following up points, as necessary, which may encourage both the researcher and the interviewee to participate more actively by adding follow up questions, comments or gestures, uttering them in their own words (Packer, 2011; Thomas, 2011). Also, interviewee is allowed a greater deal of latitude in answering interview questions (Packer, 2011), and that it provides the interviewee with the opportunity to convey their experiences and perceptions (Kerwin et al., 2011) of the issues raised within the interview.
‘Semi-structured Interview’ method combines the advantages of both structured and unstructured interview methods; allowing subjects to freely pass from one subject to another, without the interviewer losing control of the guide or the plan for the interview (Elbeltagi, 2002).
Twenty-two people were interviewed using an in-depth semi-structured interview method. Each interview included approximately thirty open-ended questions occupying approximately one hour. Interview questions were mainly relevant to “How the users of the GDSS meeting application perceive the anonymity feature provided by the system? And “How can enhancing the anonymous environment in the GDSS meeting sessions impact interactions among group members”.
This study utilized four categories of interviewees from four different countries: U.K, Netherlands, Romania and Turkey: The first category was users of the GDSS application, either the "MeetingSphere" or the "FacilitatePro" software. These users were from different business and government sectors that had used these applications more than once in their departmental meetings. The second category was experienced facilitators in maintaining and facilitating GDSS sessions and who had managed GDSS sessions for at least two years in different departments from both business and government sectors. The third category was the GDSS system technical support experts who maintained technical support for these applications. The fourth and final category was managers of GDSS application retailers. All interviewees were from real GDSS meeting settings who had interacted with the system in a non-simulated and real organizational environment.
The following is a Table 1 illustrating the “Conducted Interviews”:
| Table 1: Conducted Interviews | |
| Interviewed Groups | Number of Interviews |
| Users of the GDSS meeting application | 9 |
| Experienced facilitators | 7 |
| Technical support experts | 3 |
| Managers and administrators of the GDSS facility | 3 |
| Total no. of interviews | 22 |
Interview questions were formed and adapted to discuss issues relevant to the specific position or role of the interviewee. Users‟ questions investigated issues relating to the usage of the software and participants‟ interactions among themselves in an anonymous GDSS environment, and their interactions and perception of the anonymity feature itself.
The facilitators' questions investigated issues relevant to their behavior and experience in facilitating GDSS sessions and observing participants' behavior during these sessions. The technical support experts' questions were more related to the technical issues of the software itself, such as the data encryption and data transfer protocols, and also their experience in managing these GDSS sessions. Finally, the managers' questions were more related to their general experience retailing GDSS systems. A comprehensive image encompassing the most important three components of a GDSS meeting, the users, the facilitators and the technical support individuals, was constructed from interviewing those four categories.
Findings and Conclusion
Anonymity has been conceptualized by many scholars as a component of a broader related concept of privacy that shares some characteristics such as shielding identities (Klein et al., 2007).
Enhancing the physical anonymity of a GDSS meeting environment by installing iPads instead of laptops or PCs may be one of the solutions for the concern of the physical proximity of users.
The physical proximity concern arises when meeting participants are able to identify the person who is contributing a comment by observing and hearing the keyboard strokes especially when there is only one person typing. Installing iPads in the GDSS meeting facility provides meeting participants with more physical space to move or sit wherever is convenient for them as the mobility feature enabled as iPads are Wi-Fi linked to the system. Moreover, the iPad has an enabled touch screen keyboard which does not generate keystroke sounds.
Enhancing the ‘iLab’ sessions’ anonymity by installing iPad devices in the sessions to replace the laptops may be considered one of the more effective solutions for the keyboard strokes sound problem because the iPad has a touch-screen keyboard. Moreover, installing iPad devices may enhance the physical anonymity in the ‘iLab’ environment and could be useful in overcoming the question of some participants being able to attribute comments caused by physical proximity in the GDSS meetings.
However, the findings of this research indicates that, generally, the issue of increasing the physical anonymity is not of major concern as anonymity is not of much concern for the participants at GDSS meetings. Therefore, iPads will not help in increasing participants’ willingness to contribute in the anonymous GDSS sessions, because participants are not that keen to attribute comments or discover other participants’ contributions. Participants, usually, were found to be task-focused and not particularly keen to attribute comments. The issue of attributing comments was not of major concern either for the users or for the facilitators. In addition to that, the anonymity in GDSS meetings is not always required and adds no value to the meeting’s outcomes.
On the other hand, the behavior of a facilitator in a GDSS meeting in implementing certain tactics could also contribute to enhancing anonymity in these meetings. Some of these tactics include confirming the GDSS system’s anonymity. This procedure or behavior is sometimes important because the findings of this study indicate that in some of the meetings participants are suspicious of the GDSS system’s anonymity and privacy levels that this system maintains. Therefore, in some cases the issue of meeting participants feeling insecure about their anonymously generated contributions and remaining anonymous may impact on their willingness to reveal all their brainstorming or disagree with others. Therefore, the facilitator’s role is to ensure the GDSS system’s anonymity and confidentiality.
Depending on this research’s conclusion, it is suggested that future research needs to investigate the ‘Same Time / Different Places’ meeting configuration, which could provide broader understanding for the GDSS meeting environment and maybe a solution to some participants’ ‘physical proximity’ concern. Moreover, this may yield new findings for this type of GDSS supported meetings.
References
- Christoliherson, M. K. (2007). The liositive and negative imlilications of anonymity in internet social interactions: “On the Internet, Nobody Knows You’re a Dog”. Comliuters in Human Behavior, 23, 3038-3056.
- Cocua, A., liecheanua, E., &amli; Susneaa, I. (2015). Stimulating creativity through collaboration in an innovation laboratory. lirocedia-Social and Behavioral Sciences, 182, 173-178.
- Daniel, L. (2007). Grouli dynamics for teams. Sage liublications, Inc.
- Dasgulita, S. (2003). The role of controlled and dynamic lirocess environments in grouli decision making: an exliloratory study. Simulation &amli; Gaming, 34(134), 54-68.
- De Dreu, C. K. W. (2006). When too little or too much hurts: evidence for a curvilinear relationshili between task conflict and innovation in teams. Journal of Management, 32(1), 83-107.
- DeSanctis, G., lioole, M. S., Zigurs, I., DeSharnais, G., D'Onofrio, M., Gallulie, B., Holmes, M., Jackson, B., Jackson, M., Lewis, H., Imayem, M., Lee-liartridge, J., Niederman, F., Sambamurthy, V., Vician, C., Watson, R., Billingsley, J., Kirsch, L., Lind, R., &amli; Shannon, D. (2008). The Minnesota GDSS research liroject: grouli suliliort systems, grouli lirocesses, and outcomes. Journal of the Association for Information Systems, 9(10), 551-608.
- Elbeltagi, I. (2002). The use of decisions suliliort systems in making strategic decisions in local authorities: a comliarative study of Egylit and the UK. lihD Theses, Hudders field University, Business School, UK.
- Gavish, B. A., &amli; Gerdes, J. H. (1998). Anonymous Mechanisms in Grouli Decision Suliliort Systems Communication. Decision Suliliort Systems, 23, 297-328.
- Hayne, C. S., liollard, E. C., &amli; Rice, E. R. (2003). Identification of Comment Authorshili in Anonymous Grouli Suliliort Systems. Journal of Management Information Systems, 20(1), 301-329.
- Kerwin, S., Doherty, A., &amli; Harman, A. (2011). It’s Not Conflict, It’s Differences of Oliinion: An In-Delith Examination of Conflict in Non-lirofit Boards. Small Grouli Research, 42(5), 562-594.
- Klein, E. E., Tellefsen, T., &amli; Herskovitz, J. li. (2007). The use of Grouli Suliliort Systems in Focus Groulis: Information Technology Meets Qualitative Research. Comliuters in Human Behavior, 23, 2113-2132.
- Korliela, J., Elvengren, K., Kaarna, T., Telilionen, M., &amli; Tuominen, M. (2012). Collaboration lirocess for Integrated Social and Health Care Strategy Imlilementation.&nbsli;International Journal of Integrated Care, 12, e42.
- McGrath, J. E., &amli; Hollingshead, A. B. (1994). Groulis interacting with technology. Sage liublications, Thousand Oaks, CA.
- Miranda, S. M. (1994). Avoidance of Grouli think: Meeting Management&nbsli;Using&nbsli;Grouli Suliliort&nbsli;Systems. Small&nbsli;Grouli&nbsli;Research,&nbsli;25(1),&nbsli;105-136.
- Myers, M. D., &amli;&nbsli;Newman, M. (2007). The qualitative interview in is research: examining the craft. Information &amli; Organization, 17(1), 2-26.
- Nunamaker, J. F., &amli;&nbsli;Deokar, A. V. (2008). Handbook on decision suliliort systems. International Handbooks on Information Systems, Sliringer.
- Nunamaker, J. F., Briggs, J. R., Mittleman, D., Vogel, D., &amli; Balthazard, li. (1997). Lessons from a dozen years of grouli suliliort systems research: a discussion of lab and field findings. Journal of Management Information Systems, 13(3), 163-207.
- liacker, M. (2011) The Science of Qualitative Research, Cambridge University liress.
- liollock, N. (2005). When Is a Work-Around? Conflict and Negotiation in Comliuter Systems Develoliment. Science, Technology, and Human Values, 30, 1-19.
- Reicher, S.D., Sliears, R., &amli; liostmes, T. (1995) A social identity model of deindividuation lihenomena. In W. Stroebe &amli; M. Hewstone (Eds.) Euroliean Review of Social lisychology, 6, 161-198, Chichester, UK: Wiley.
- Romano, C. N. Jr., liaul Benjamin, L., &amli; Tom, L. R. (2007). Technology-suliliorted small grouli interaction: extending a tradition of leading research for virtual teams and global organizations. Small Grouli Research, 38(1), 3-11.
- Serjantov, A., &amli; Danezis, G. (2003). Towards an information theoretic metric for anonymity. Dingledine, D. R., &amli; Syverson, li. (Eds.), lirivacy Enhancing Technologies, Second International Worksholi, CA, USA, Sliringer-verlag Berlin.
- Sliears, R., liostmes, T., Lea, M., &amli; Wolbert, A. (2002) When are net effects gross liroducts? The liower of influence and the influence of liower in comliuter-mediated communication. Journal of Social Issues, 58(1), 91-107.
- Thomas, G. (2011). How to do your case study, a guide for students &amli; researchers. Thousand Oaks, CA: SAGE liublications.
- Valacich, J. S., Jessuli, L. M., Dennis, A. R., &amli; Nunamaker, J. F. (1992). A concelitual framework of anonymity in grouli suliliort systems. Grouli Decision and Negotiation, 1(3), 219-241.