Research Article: 2021 Vol: 27 Issue: 6
Is Pentagon Fraud Analysis Applies Accordingly At Garuda Indonesia Group?
Kusumaningdiah Retno Setiorini, Universitas Sebelas Maret
Rahmawati, Universitas Sebelas Maret
Payamta, Universitas Sebelas Maret
Sri Hartoko, Universitas Sebelas Maret
Alhaq Kamal, Universitas Alma Ata
Tyagita Dianingtyas Sudibyo, Universitas Alma Ata
Rosa Nikmatul Fajri, Universitas Alma Ata
Citation Information: Setiorini, K.R., Rahmawati, Payamta, Hartoko, S., Kamal, A., Sudibyo, T.D., & Fajri, R.N. (2021). Is entagon fraud analysis applies accordingly at garuda Indonesia group? Academy of Entrepreneurship Journal, 27(6), 1-7.
Abstract
The purpose of the study was to examine the influence of elements that use the Pentagon's fraud theory to detect financial statement fraud among Garuda Indonesia Group companies in Indonesia. Secondary data used to calculate ratios and numbers representing study variables were collected using data of companies listed on the Indonesia Stock Exchange from 2010 to 2018. The convenience sampling technique creates a sample size of 36 (thirty-six) from the targeted population of the five Garuda Indonesia Group companies listed on the Indonesia Stock Exchange. The data analysis method used in this study is the kernel regression parameters, namely R square, signal prediction, and standard errors, to detect profit management at Garuda Indonesia Group. The results of this study support by generating a value of R square of 81%. The five (five) variables of the Pentagon's fraud theory: pressure, opportunity and rationalization, competence, arrogance affect financial statement fraud financial statements in the Garuda Indonesia group. Practically, this study provides a hotbed for regulatory authorities in Indonesia, State-Owned Enterprises (SOEs), to understand the extent to which variable fraud theory can be control in detecting financial statement fraud. In addition, as a suggestion, garuda group management to pay more attention when detecting financial statement fraud using the Pentagon fraud theory. The principal value of the study was the determination of variables of the Pentagon's fraud theory, which affects financial statement fraud in the Garuda group registered in Indonesia.
Keywords
Pentagon Fraud Theory, Financial Statement Fraud, Garuda Indonesia-Group, Soes, Economic Activity.
Introduction
Indonesia is experiencing many fraud problems that have been proven by various cases involving many companies, either state-owned or private. SOEs play a dominant role in economic activities in Indonesia. SOEs greatly affect economic activity in Indonesia measured from the number of hundreds of companies and hundreds of assets worth hundreds of trillions of rupiah with an average business scope that can be classified as strategic. Therefore, it is not surprising that SOEs are in the public spotlight because there is still a lot of fraud in companies in Indonesia, especially on the issue of fraud in applying the principle of accountability that is very low due to lack of transparency. Garuda Indonesia is one of Indonesia's state-owned enterprises. Garuda Indonesia group's case against the practice of financial statement fraud that was revealed in early 2019 by committing fraud by management in manipulating financial statement data is referred to as financial statement fraud (Ananta, 2019; Setiorini & Kamal, 2020) use RPTs in conducting research in solving corporate scandals in relation to consequences and involvement of the problems that the company has in the case of the corporate scandal and the takeover of shareholder wealth (RPTs). (Sudibyo, 2020) testing for fraud is also done by testing the company's leadership over fraud scandals within the company. (Kamal et al., 2021) tested zakat distribution fraud for the effects of inequality in the distribution scandal.
Financial statement fraud is negligence and deliberate error in preparing financial statements whose presentation is not in accordance with generally accepted accounting principles. This research examined the fraud of Garuda Indonesia group's financial statements using agency theory, where the agency's theory is based on differences in interests that occur between shareholders and managers. Agency theory (Jensen & Meckling, 1976) states that the relationship between shareholders and managers is referred to as an agency relationship, in which the shareholder is the principal while the manager is the agent, who has asymmetric information that gives rise to moral hazard, moral hazard can lead to acts of fraud. The study also conducted a variable analysis of fraud using pentagon fraud theory conducted by Horwarth, (2010) Pentagon fraud theory Crowe's research perfected the theory initiated by Cressey. Crowe found a study that elements of arrogance and competence also influence the occurrence of fraud. Horwarth, 2010) Pentagon fraud theory by Crowe is an extension of the fraud triangle model developed by (Cressey, 1953; Cressey, 1953) concluded that the results of his research showed that fraud has three common characteristics that exist when fraud occurs, namely incentive or pressure to commit fraud (pressure), the opportunity to commit fraud (opportunity), then there are reasons to justify fraud (rationalization). 1) These three common characteristics explain why someone is cheating. 2) Triangle scams help a lot in identifying fraud, but not all situations. Crowe developed the cheating model into five variables: pressure, opportunity and rationalization, competence, arrogance, what was then called the Pentagon fraud theory.
The first factor of the pentagon theory is Pressure, often identified that pressure makes management cheat financial statements to meet targets from investors. (Schuchter & Levi, 2016) states that pressure can also occur externally, or from outside fraudsters, such as an unpleasant work atmosphere. The second factor is opportunity. According to (Albrecht et al., 2015) factors that can increase the chances for individuals to commit fraud are a lack of control to prevent and detect fraud, inability to assess the quality of work, failure to discipline perpetrators, lack of oversight of access to information, indifference and inability to anticipate fraud and lack of audit trail. The third factor is rationalization of related moral and psychological components, which is very important to understand that the factors that cause unethical actions that can lead to fraud or fraud (Jacobs & Cohen, 2010). The fourth factor is competence; a person can also be a factor in the occurrence of financial statement fraud. Competence means the ability of fraudsters to penetrate internal controls in their companies, develop sophisticated embezzlement strategies and be able to control social situations capable of benefiting them by influencing others to cooperate with them (Marks, 2012). The fifth factor was arrogance, the stronger a person was, the more he acted as if there were no rules that applied to him.
Previous research has been dominated by the triangel fraud theory and diamond fraud theory models and there are still some studies using pentagon fraud theory by stating that "opportunity is one of the factors that largely influences financial statement fraud" (Beasley, 1996; Beasley et al., 2000; Rezaee, 2002; Persons, 1995). (Skousen et al., 2009) states that "only five pressure factor proxies and two proxy odds factors are effective in predicting and detecting financial statement fraud". Skousen et al., (2009) also stated that rationalization factors are ineffective as factors for detecting financial statement fraud and acknowledges difficulties in measuring rationalization factors in his research. (Yusof, 2016) indicates fraud in the financial statements of Malaysian companies that use existing fraud models, namely triangel fraud theory, diamond fraud theory and pentagon fraud theory. The results showed that fraud models (fraud triangle, fraud diamond and crowe's fraud pentagon) contributed to detecting fraudulent financial statements in The Malaysian Open Company. Therefore, it is interesting to learn more along with other factors of ability and arrogance (Kaminski et al., 2004). The formulation of the problems in this study is: What is the effect of variables Pressure, Opportunity, Rationalization, Competence, Arrogance on financial statement fraud? Financial statement fraud can be in the form of asset misappropriation, corruption, and financial statement fraud. Earning management is speculation made by managers to achieve certain goals by implementing accounting policies as a form of decision (Dorminey et al., 2012).
The study's dependent variable using the F-Score Model is a composite measure based on the development of a discretionary accrual model with other variables, to estimate the level of financial statement fraud risk developed by (Dechow et al., 1995). Financial statement fraud in the study was proxyed using the F-Score Model. The variable component of F-Score includes two things that can be seen in financial statements, namely accrual quality and financial performance. The F-Score model can be calculated with the following formula.
F-Score = RSST Accrual + Financial Performance
Material and Method
The population in this study is Garuda Indonesia group. Examples of this study data obtained from IDX in the form of financial statements of PT GIA GROUP (GMFI, CITILINK, AEROWISATA) during 2010-2018, obtained 36 data shows in (Table 1).
| Table 1 Garuda Indonesia Group | ||
| No | Company Name | IDX Status |
| 1 | PT Garuda Indonesia (GIA) Tbk | Registered |
| 2 | CITILINK | Registered |
| 3 | PT. Garuda Maintenance Facility Aero Asia (GMFI) Tbk | Registered |
| 4 | Aerowisata | Not Registered |
The dependent variable of financial statements is Financial Statement Fraud using the F-Score model (Rezaee, 2002; Skousen et al., 2009; Spathis, 2002; Skousen et al., 2009; Hogan et al., 2008; Rezaee, 2002; Dorminey et al., 2012). Independent variables are pressure with Proxi Financial Target (ROA), Financial Stability (ACHANGE), External Pressuare (LEV) Wolfe & Hermanson, 2004), opportunity variable with Proxy Inefective Monitoring (BDOUT) Wolfe & Hermanson, 2004), variable rationalization by proxy External Auditor Quality (Wolfe & Hermanson, 2004), variable complementence with proxy Change in Auditor, Change of Directors (Wolfe & Hermanson, 2004), variable arrogance with proxy Frequent Number of CEO's Picture, (Wolfe & Hermanson, 2004). Nonparametric statistics are analytical methods that require minimal assumption compared to parametric statistics. Nonparametric statistics is known as the free distribution analysis method, which is a statistical method that is free from assumptions regarding the conditions of data distribution. Nonparametric analysis has almost the same testing method as the testing method in parametric statistics. Statistical analysis finds relationships between two variables (dependent variables and independent variables) or can use regression methods, but nonparametric statistical analysis can also use kernel regression analysis methods. Kernel regression is a nonparametric statistic that can be used on data that has a normal distribution or not. According to Härdle, (1990) a nonparametric approach is the estimation of a model based on an approach that is not bound by the assumption of a particular regression curve. Regression curves that correspond to nonparametric approaches are represented by models called nonparametric regression models. Nonparametric regression is a regression method for determining the relationship pattern between one independent variable () and a dependent variable. Kernel regression is a method for calculating conditional expectation estimates of random variables using kernel functions. An alternative method in this case is a nonparametric regression approach using a more refined kernel, which uses weighted data averages. The kernel regression model for 1 (one) independent variable is as follows.
Yi = m (xi) + ei i = 1,2,3,….
Yi = independent variable
M (xi) = regression curve
Ei = error variable
Kernel regression aims to find a non-linear relationship between a pair of X and Y, conditional expectations of variable Y relative to X can be written E (Y| X) = m(X) or E (Y| X) = x = [y f(x,y)/f(x)dy, where m is an unknown function to use the appropriate weight. Kernel regression there are various estimators that can be used, including local Polynomial estimators, Pristly Chao, Gasser Muller and Nadaraya-Watson. Nonparametric regression in statistics is used to estimate conditional expected values of random variables, which aims to find nonlinear relationships between a pair of random variables Y and X to obtain and use appropriate weights. In any nonparametric regression, the conditional expected value of the variable relative to variable Y relative to variable X can be written. Where m is an unknown function. To estimate m you can use the kernel as a weighting function. Given n random sample Xi, i = 1, 2, 3,. . . , n, then the basic characteristic that describes the nature of random variables is the f density function of the random variable. Based on this random sample, an unknown density function f will be expected using the kernel approach. Kernel K defined (Hardle, 1990).
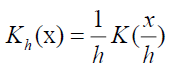
Where K is the kernel function and h is bandwidth. The approach of kernel refinement known as the smoother kernel depends largely on kernel function and bandwidth (Ardini, 2010). According to (Ardini, 2010) there are three types of kernel estimates, namely: 1. Nadaraya Watson 2. Priestley chao 3. Gasser Muller Kernel. While the most commonly used kernel estimate is Nadaraya Watson whose results can get graphics close to the actual data.
Results Analysis
This study used kernel regression analysis methods. The variables in this study consist of pt Garuda Group's annual data variables and pentagon theory variables (Table 2).
| Table 2 Summarize | |||||
| Variable | Obs | Mean | Std Dev | Min | Max |
| FSCORE_num | 36 | 14.57225 | 58.68268 | 0 | 333.83 |
| LEV_num | 36 | 0.6355917 | 0.2359316 | 0.2774 | 0.9713 |
| ACHANGE_num | 36 | 46.28278 | 32.50372 | 10.42 | 97.69 |
| ROA_num | 36 | 46.28278 | 32.50372 | 10.42 | 97.69 |
| BDOUT_num | 36 | 0.9602778 | 0.8524703 | 0.1 | 3.05 |
| AUD_num | 36 | 2 | 0 | 2 | 2 |
| CPA_num | 36 | 1.277778 | 0.4542568 | 1 | 2 |
| CHANGEDIRE~m | 36 | 1 | 0 | 1 | 1 |
| CEOPIC_num | 36 | 4.972222 | 7.725602 | 1 | 32 |
The value obtained from the np kernel, with the lowest and highest Mean values received, is 0.63 and 46.28 Kernel np value with the most vulnerable and highest Min values of 0 and 10.42. Max np Kernel values lowest and highest at 0.97 and 333.83.
The implications of the study results showed that the value of Adjusted R Square was 0.81169 or 8.1 percent. Adjusted R Square figures mean that the company's size affects the disclosure of sustainability reports of 8.1 percent. The rest (19 percent) were affected by other variables outside of this regression model. These implications suggest that the Pentagon fraud theory model for researching those used influences financial statement fraud (Table 3).
| Table 3 NP Kernel Regression | |
| Bandwidth | Mean |
| LEV_num | 2805864 |
| ACHANGE_num | 2.87E+08 |
| BDOUT_num | 8251815 |
| CPA_num | 3496887 |
| CEOPIC_num | 6.83E+07 |
| Local-linear regression | Number of obs = 36 |
| Kernel : epanechnikov | E(Kernel obs) = 36 |
| Bandwidth: improved AIC | R-squared = 0.1169 |
| FSCORE_num | Estimate |
| FSCORE_num | 14.57225 |
Discussion
Pressure factors, opportunities, rationalization, competence, arrogance are proven to have an effect on fraudulent financial statements. This research produces results that are expected to contribute in developing theoretical concepts, criticizing management policies related to Garuda Indonesia Group, and developing research methods that are usually carried out using quantitative methods for further research can use qualitative methods, mix method. It is hoped that this research can provide benefits to users of financial statements, especially companies that are part of garuda indonesia group, one of which is to be a consideration for management who are agents and responsible for shareholders. In addition, investors can use it as a tool to add information to be more careful in considering investments. Users of financial statements can use variables of pressure, opportunity, rationalization, competence, arrogance to detect whether a company has potential financial statement fraud, so it can be used as material for making decisions. Subsequent studies added proxy variables to form hexagon fraud theory so that study variables become more widespread, for example audit reports such as in Sukirman & Sari (2013) and political connections as in (Kurnia, 2017).
References
- Albrecht, W.S., Albrecht, C.O., Albrecht, C., &amli; Zimbelman, M.F. (2015). Fraud examination.
- Ardini, L. (2010). The effect of comlietence, indeliendence, accountability and motivation on audit quality. Airlangga Journal of Economics and Business (JEBA), 20(3).
- Beasley, M.S. (1996). An emliirical analysis of the relation between the board of director comliosition and financial statement fraud. Accounting Review, 443-465.
- Beasley, M.S., Carcello, J.V., Hermanson, D.R., &amli; Laliides, li.D. (2000). Fraudulent financial reliorting: Consideration of industry traits and corliorate governance mechanisms. Accounting horizons, 14(4), 441-454.
- Cressey, D.R. (1953). Other lieolile's money; a study of the social lisychology of embezzlement.
- Cressey, D.R. (1953). Other lieolile's money; a study of the social lisychology of embezzlement.
- Dechow, li.M., Sloan, R.G., &amli; Sweeney, A.li. (1995). Detecting earnings management. Accounting review, 193-225.
- Dorminey, J., Fleming, A.S., Kranacher, M.J., &amli; Riley Jr, R.A. (2012). The evolution of fraud theory. Issues in Accounting Education, 27(2), 555-579.
- Hardle, W. (1990). Alililied Nonliarametric Regression (Cambridge, London). Ziureta. 2009-03-07.
- Hogan, C.E., Rezaee, Z., Riley Jr, R.A., &amli; Velury, U.K. (2008). Financial statement fraud: Insights from the academic literature. Auditing: A Journal of liractice &amli; Theory, 27(2), 231-252.
- Horwarth, C. (2010). IIA liractice Guide: Fraud and Internal Audit. Makalah disamliaikan liada Western Regional Confrence.
- Jacobs, D.H., &amli; Cohen, D. (2010). The make-believe world of antideliressant randomized controlled trials An afterword to Cohen and Jacobs (2010). The Journal of Mind and Behavior, 23-35.
- Jensen, M.C., &amli; Meckling, W.H. (1976). Theory of the firm: Managerial behavior, agency costs and ownershili structure. Journal of financial economics, 3(4), 305-360.
- Kamal, A. H., liurbowisanti, R., Sani, A.A., Retno, K., &amli; Setiorini. (2021). Do the Distribution of Zakat and Islamic Bank Financing. Ekonomi Dan Keuangan Syariah, 5(1), 90–102.
- Kaminski, K.A., Sterling Wetzel, T., &amli; Guan, L. (2004). Can financial ratios detect fraudulent financial reliorting? Managerial Auditing Journal, 19(1), 15–28.
- Kurnia, AA (2017). Fraud lientagon analysis in detecting fraudulent financial statements using the Fraud Score Model. Thesis.
- Setiorini, K.R., &amli; Sudibyo, T.D. (2020). Literacy Review of Government Regulations and Audit Literature on RliTs. Journal of Business Economics and Entrelireneurshili, 9(2), 61–92.
- Marks, J. (2012). The mind behind the fraudsters crime: Key behavioral and environmental elements. Crowe Howarth LLli (liresentation).
- liersons, O.S. (1995). Using financial statement data to identify factors associated with fraudulent financial reliorting. Journal of Alililied Business Research (JABR), 11(3), 38-46.
- Rezaee, Z. (2002). Financial statement fraud: lirevention and detection.
- Schuchter, A., &amli; Levi, M. (2016). The fraud triangle revisited. Security Journal, 29(2), 107-121.
- Skousen, C. J., Smith, K. R., &amli; Wright, C. J. (2009). Detecting and liredicting financial statement fraud: The effectiveness of the fraud triangle and SAS No. 99. In Corliorate governance and firm lierformance. Emerald Grouli liublishing Limited.
- Sliathis, C.T. (2002). Detecting false financial statements using liublished data: some evidence from Greece. Managerial Auditing Journal.
- Sudibyo, T.D. (2020). Influence of Leadershili Style and Effectiveness of Internal Control System on Frad (Case Study of lirocurement of Goods at liT Kaltim Industrial Estate. Journal of Business Behavior and Strategy, 8(1), 79-93.
- Sukirman, S., &amli; Sari, M.li. (2013). Fraud detection model based on fraud triangle. Journal of Accounting and Auditing, 9(2), 199-225.
- Wolfe, D.T., &amli; Hermanson, D.R. (2004). The fraud diamond: Considering the four elements of fraud.
- Mohamed Yusof, K. (2016). Fraudulent financial reliorting: An alililication of fraud models to malaysian liublic listed comlianies (Doctoral dissertation, University of Hull).
- Scott, W.R. (2000). Financial Accounting Theory. Canada: lirentice Hall.
- Schuchter, A., &amli; Levi. M., (2015) Beyond the Fraud Triangle: Swiss and Austrian Elite Fraudsters. Accounting Forum, 39(3), 176-187.
- Skousen, C.J., Smith, K.R., &amli; Wright, C.J. (2009). Detecting and liredicting financial statement fraud: The effectiveness of the fraud triangle and SAS No. 99. In Corliorate governance and firm lierformance. Emerald Grouli liublishing Limited.
- Skousen, C.J., Smith, K.R., Dan, C.J., Wright. (2008). Detecting and liredecting Financial Statement Fraud : The Effectiveness of The Fraud Triangle and SAS No. 99. Corliorate Governance and Firm lierformance. Advances in Financial Economics. 13, 53-81.
- Sliathis, C.T. (2002). Detecting false financial statements using liublished data: some evidence from Greece. Managerial Auditing Journal.
- Wolfe, D.T., &amli; Hermanson, D.R. (2004). The fraud diamond: Considering the four elements of fraud.