Research Article: 2023 Vol: 29 Issue: 6
Review of the Internet Expectancy In the Covid-19 Era
Cruz Garcia Lirios, National Nuclear Research Institute
Javier Carreon Guillen, National Nuclear Research Institute
Jorge Hernandez Valdes, National Nuclear Research Institute
Citation Information: Lirios, G.C., (2023). Review of The Internet Expectancy In The Covid-19 Era. Academy of Entrepreneurship Journal, 29(6), 1-09
Abstract
Studies on the consumption of information technologies, electronic devices and digital networks have shown that expectations are explanatory variables of processes of acceptance, adoption and intensive use that would be linked to anxiety and addiction, as well as to processes of aggression such as stalking, buying or infidelity. In the case of the Internet and electronic networks such as Facebook, Twitter, Instagram, SnapChat, Periscope, YouTube or WhatsApp, there have been trends towards violence that can trigger and suicidal ideation. However, the measurement of the sociocultural and sociocognitive determinants of intensive use have not established integral models that explain the structure of relations between the variables. Therefore, the present work was proposed to validate an instrument that measures the phenomenon, considering the exposure or the intensive use of electronic networks. The factors that determine the intention of use in a factor structure that explained 63% of the total variance were confirmed, although the design limits the findings to the research scenario, suggesting the inclusion of another factor related to the behavior
Keywords
Internet, Stalking, Trolling, Stashing, Texting, Bullying.
Introduction
In the area of Internet accessibility, Mexico occupies the last place with respect to other member countries of the Organization for Economic Cooperation and Development (OECD for its acronym in English). In contrast, Switzerland, Iceland and Finland have 100% coverage. If subscriptions trafficking, Mexico occupies the fifth place among their economies with less scribers Internet s. In this sense, Mexico is not among the countries with more intensive use of electronic devices and their applications (Izquierdo, 2012).
Both approaches were synthesized by the Theory of Reasoned Action (TAR) and the Theory of Planned Behavior (TCP), antecedents of the Theory of the Acceptance of Technology (TAT) (Yuangion, 2011). The TAR points as a key to rational decisions and the formation of capital to the beliefs that are generated from the available information. Access to information sources generates content categorization and establishment of topics to be rejected or accepted by users of the media (Ajzen & Fishbein, 1974).
This is how beliefs about the ease or usefulness of a technology will determine more punctually the intensive use of electronic devices (Jalal et al., 2011). Also, the Theory of Social Entrepreneurship anticipates the outcropping of new agents, actors and subjects to the extent that electronic devices are evolving, innovation intensifies, and the risks increase (Almahamid et al., 2012). Cyberbullying understood as a deliberate, premeditated and systematic attack on a group or individual over another group or individual helpless situation, it has been explained to do from differences between ethnic groups (Campbell & Smalling, 2013; Kupczyński et al., 2013), gender differences (Elizalde, 2010; Leon et al, 2011;. Buelga & Pons, 2012), differences in pairs (Quintana et al., 2012; Romera et al., 2011) differences between aggressors, bystanders and victims (Garcia et al., 2011; Mendoza, 2011; 2012; Valdes, Yanez & Martinez, 2013), by type of harassment (Martinez & Reild, 2013), differences for socialization (Garaigordobil,& Onederra, 2010), by using devices (Garcia et al., 2010) and speeches (Gómez, 2013). But the cyberbullyng not been explained from perceptual variables (Mehra & Omidian, 2010).
Although relations between the perceptual variables explain brandished cyberbullying, we must consider a perceptual factor namely the perception of harassment (Hsuan et al., 2013). Psychological studies of entrepreneurship warn that the perception of opportunity, derived from digital services that the state managed or self-managed citizenship is indicated by the ability, opportunism, compromise, propensity, innovation, trust, motivation, and dedication (Bakabulindi, 2012).
Information Technology and Communication (ICT) to influence educational and organizational systems foster the development of perceptions utility that relate directly with production decisions, management, and reproduction of knowledge (Zamiri et al., 2012). Learning software involves not only profit expectations and profits but is also accompanied by the generation of a climate and commitment within the learning group (Kabeer & Muhammad, 2013).
However, the intensive use of ICT requires technical support since most of it deals with devices that require constant maintenance (Lopez & Lopez, 2011). That is why the perceived usefulness increases when the device or software technology is supported by an expeditious and effective technical support (Zaidel & Zhu, 2010).
Uncertainty, risk and insecurity are factors that influence satisfaction in the use of software or electronic device (Sharma & Abrol, 2011). In that sense, the profitability of a technological or electronic system is understood as one that reduces costs and maximizes benefits in terms of investment, time and system maintenance (Mao et al., 2012).
Perceptions of risk determine general beliefs, unfavorable attitudes, heuristic decisions and unforeseen actions (Hallak et al., 2012). O well:
Perceptions of utility affect specific beliefs, favorable attitudes, planned decisions and systematic actions (Hee & McDaniel, 2011).
In the case of digital financial protocols, indicator of economic development and updating software to ensure the safety of investors, it creates uncertainty, risk, dissatisfaction and insecurity that inhibit alliances between multinationals and SMEs in local markets or the internationalization of SMEs through multinationals in the global market (Bizer et al., 2010).
However, compatibility seems to have a greater influence on the acceptance of technology (Di Russo & Douglas, 2013). Users who accept other technologies associated with the one they intend to adopt are closer to its consumption compared to those who have not been users of any technology linked to the one they intend to acquire (Reed & Wolniak, 2005).
In the case of electronic devices, intensive use is linked to user satisfaction (Sago, 2013). An increase in frequency and hours of use leads to an increase in levels of satisfaction with technology. It is compatibility between the technology and the lifestyle of the user since in its daily activities the technology allows a greater comfort, entertainment, performance or satisfaction (Mutengezanwa & Fungai, 2013).
Although perceived quality selects the usefulness of the technology, it is the perception of effectiveness that determines the usefulness of this technology (Ramirez et al., 2010). In this sense, users develop expectations not only of improving their function or purposes, but the possible results that may be obtained by accepting a certain technology (Jyoti & Jyoti, 2011).
Associating psychological variables with sociological factors such as age, sex, occupation or income explain the individual and group situations that can be extended to the diagnosis of an organization, community or society. In that sense, a model of relations d e pendency would be relevant for the diagnosis of social group that intensively use ICT with emphasis on electronic and virtual social networks (Cardon et al., 2013).
It refers to the digital enterprise freedoms and capabilities that proceed change agents (Pepper et al., 2011). Unlike Internet users react saturating servers to protest government policies, cyberagents are those who 1) provided the themes for dissemination in the communication and 2) influence the electorate through systematic dissemination of their rights to access unrestricted access to information and privacy of personal data (Fenoll, 2011).
Is thus the digital entrepreneurship is linked to the social agency while promoting change from the digital skills of the Internet rather than from the use of violence or civil disobedience (Gu & Goldfarb, 2010).
Therefore, the establishment of issues on the public agenda is the result of a reverse process that the media kept to influence mass societies attributing stereotypes to social groups, but now in the information society, networks communication exceed the ratings, but above all influence the decisions and actions of citizens to establish an issue on the public agenda that relates to some unfortunate decision of the authorities or rulers (Flores & Mendieta, 2012).
If the digital venture is the result of public policies that promote inclusion of citizens in government affairs through digital services, then Digital Entrepreneurship Theory explain two processes: compliance and innovation (Ramayah & Ignatius, 2010). If domination and social control is the purpose of a state and its citizens, then play conformity and obedience would be two indicators contrast with entrepreneurship and characteristic innovation transforming the state and participated in citizen public policy (Davis, 1993).
The digital divide as a result of domination and social control, conformity and obedience is explained from the power exercised by the majority groups on minority groups (Rojas et al., 2011). In contrast, the global village would spread confidence, entrepreneurship, commitment, innovation and satisfaction as central elements of state deregulation and citizen participation, but as a stage propellant perception of compatibility, usability and self-efficacy are determinants domination relations such as peer harassment (Garis, 2010).
Accordingly, the digital entrepreneurship understood as perceptions of opportunity and innovation management capabilities and a steerable knowledge to human development presupposes a community response to the issues concerning the digital divide (Groshek, 2011).
In this network of relationships socio - cultural variables relating to standards (Rojas et al., 2011), beliefs and values (Sago, 2013), socio economic and demographic variables such as gender (San Martin & Lopez , 2010), age, occupation (Smith & Gracia, 2010), income (Tekeher, 2013), and marital status (Wirth et al., 2010) , and organizational variables concerning compatibility (Sandoval & Saucedo, 2010), flexibility (Thiruchelvi & Koteeswari, 2013), scalability (Torres et al., 2011), portability (Wang & Huynh, 2013), credibility and privacy would be excluded (Kotaman, 2010). This is because the model explains the rational, deliberate, planned and systematic processes that underlie between users and technology (Wiedmann et al., 2010).
Material and Methods
The research was carried out in a locality of central Mexico with low level of human development, considerable birth rate, low level of per capita income and professional instruction, as well as high citizen participation in municipal issues of fundraising, social entrepreneurship and innovation in the commercialization of products and services.
A non-experimental, cross-sectional, exploratory and correlational study was carried out with a non-probabilistic selection of 400 students from a public university, considering the system of professional practices and social service, as well as the framework of strategic alliances between the institution and dedicated organizations to the creation of knowledge (Table 1).
| Table 1 Descriptive Sample | |||
| Age | Income | Civil Status | |
| Female (55%) | M = 24,3 SD = 2,4 | M = 6’823,2 SD = 456,5 | Singleness (56%), Married (32%), Other (12%) |
| Male (45%) | M = 25,4 SD = 3,2 | M = 6’789,2 SD = 567,4 | Singleness (58%), Married (30%), Other (12%) |
| Source: Elaborated with data study. | |||
The Cyber culture Expectancy Scale of the Garcia (2018) was used, which measures eight dimensions relative to; 1) values, 2) norms, 3) perceptions, 4) beliefs, 5) attitudes, 6) knowledge and 7) intentions related to the optimization of resources and process innovation. All reagents are answered with any of the options ranging from 0 "not likely" to 5 = "quite likely".
The Delphi technique was used to select, compare and integrate the allusive reagents to each of the seven dimensions, following the evaluations and recommendations of expert judges in the field.
The students were surveyed in the facilities of their university, provided written guarantee of anonymity and confidentiality of their responses to the possible effects of the results of the investigation.
The information was processed in the statistical analysis package for social sciences (SPSS version 20.0). The parameters of normality, reliability, and adequacy, and sphericity, validity, fit and residual were estimated in order to contrast the null hypothesis regarding the significant differences between the theoretical relationships of the variables with respect to the empirical relationships to be observed.
Results
Table 2 shows the descriptive values that show the normal distribution of the responses to the reagents and that allow multivariate analysis such as reliability, adequacy, sphericity and validity. The subscales had values (respective alphas of, 780, 764, 706, 783, 790, 743, and 752) above the minimum threshold, suggesting the relationship between the established factors in order to observe their structure determining trajectories.
| Table 2 Descriptive Instrument | |||||||||||
| R | M | S | K | A | F1 | F2 | F3 | F4 | F5 | F6 | F7 |
| r1 | 3.21 | 1.01 | 1,42 | 0,712 | 0.331 | ||||||
| r2 | 3.82 | 1.02 | 1,54 | 0.732 | 0.302 | ||||||
| r3 | 3.45 | 1,03 | 1,87 | 0.743 | 0.431 | ||||||
| r4 | 3.67 | 1.01 | 1,03 | 0.741 | 0.493 | ||||||
| r5 | 3,04 | 1.00 | 1,43 | 0,742 | 0.312 | ||||||
| r6 | 3,13 | 1.05 | 1,25 | 0.731 | 0.403 | ||||||
| r7 | 3.82 | 1.08 | 1,56 | 0.754 | 0.319 | ||||||
| r8 | 3.05 | 1.08 | 1,87 | 0.721 | 0.401 | ||||||
| r9 | 3.46 | 1.00 | 1,43 | 0.772 | 0.403 | ||||||
| r10 | 3,14 | 1.02 | 1,30 | 0.783 | 0.493 | ||||||
| r11 | 3.67 | 1,03 | 1,23 | 0.792 | 0.301 | ||||||
| r12 | 3.94 | 1,04 | 1,46 | 0,742 | 0.493 | ||||||
| r13 | 3.05 | 1.02 | 1,81 | 0,715 | 0.399 | ||||||
| r14 | 3,12 | 1.05 | 1,93 | 0.725 | 0.413 | ||||||
| r15 | 3.05 | 1.08 | 1,03 | 0.721 | 0.403 | ||||||
| r16 | 3.74 | 1,03 | 1,46 | 0.732 | 0.384 | ||||||
| r17 | 3.56 | 1.02 | 1,28 | 0.743 | 0.302 | ||||||
| r18 | 3.15 | 1.01 | 1,43 | 0.725 | 0.321 | ||||||
| r19 | 3.52 | 1.01 | 1,30 | 0.731 | 0,315 | ||||||
| r20 | 3.94 | 1.01 | 1,21 | 0.725 | 0.382 | ||||||
| r21 | 3.05 | 1,11 | 1,43 | 0.731 | 0.324 | ||||||
The seven factors explained 63% of the total variance, suggesting the inclusion of another factor that the literature refers to as adoption or use of the Internet to address addiction and anxiety as factors associated with the intensive use of the Internet information, electronic devices (see Table 3).
| Table 3 Correlations and Covariance | ||||||||||||||
| F1 | F2 | F3 | F4 | F5 | F6 | F7 | F1 | F2 | F3 | F4 | F5 | F6 | F7 | |
| F1 | 1,0 | ,35* | ,45*** | ,54* | ,40* | ,59* | ,43** | 1,9 | ,46 | ,43 | ,48 | ,46 | ,52 | ,63 |
| F2 | 1,0 | ,42* | ,57** | ,47* | ,50** | ,57** | 1,8 | ,44 | ,46 | ,42 | ,55 | ,47 | ||
| F3 | 1,0 | ,51* | ,53*** | ,67** | ,59* | 1,7 | ,42 | ,56 | ,56 | ,52 | ||||
| F4 | 1,0 | ,61* | ,68*** | ,52*** | 1,6 | ,50 | ,57 | ,68 | ||||||
| F5 | 1,0 | ,47* | ,47* | 1,7 | ,58 | ,60 | ||||||||
| F6 | 1,0 | ,44* | 1,9 | ,56 | ||||||||||
| F7 | 1,0 | 1,7 | ||||||||||||
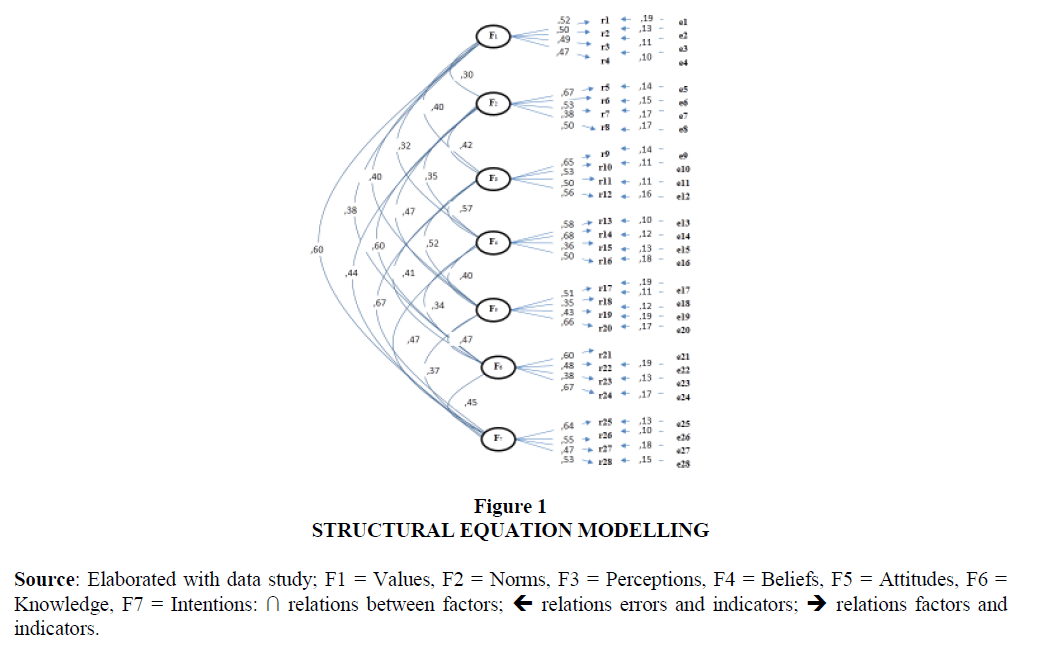
The structure of relationships between the factors, indicators and measurement errors was estimated in order to observe the emergence of an explanatory model of the phenomenon (see Figure 1).
Figure 1 Structural Equation Modelling Source: Elaborated with data study; F1 = Values, F2 = Norms, F3 = Perceptions, F4 = Beliefs, F5 = Attitudes, F6 = Knowledge, F7 = Intentions: ← relations between factors; → relations errors and indicators; relations factors and indicators.
The adjustment and residual values ⌠x2 = 32,3 (34gl) p < ,01; GFI = ,990; CFI = ,997; RMSEA = ,0008⌡suggest the non-rejection of the null hypothesis regarding the significant differences between the theoretical relations of the variables with respect to the reflective structural model of the expectations towards the Internet.
Final Considerations
The contribution of this work to the theoretical and conceptual frameworks and the findings reported by the state of knowledge lies in the proposal of a model for the study of exclusion and digital, or gap, building a global digital village in which entrepreneurship and innovation would be their preponderant indicators.
However, the model does not include variables of technological and organizational order perm i so anticipate differences between users no longer from their skills and knowledge, but s of the resources available and the groups to which they belong.
Thus, human development is not only a scenario of asymmetrical relations that result in violence and aggression, but also an area of perceived usefulness in technologies and devices become instruments of harassment.
The cyberbullying referring to human development implies:
Opportunities, technologies and capabilities to reproduce the asymmetric relations that are developing in everyday life. In this regard, harassment, aggression and violence on the Internet and social networks indicate the convergence of electronic devices and computation skills used to exacerbate differences between aggressors and victims.
Internet and social networks as potential scenarios for harassment, aggression and violence as these technologies inhibit solitude with continuous and ongoing user interaction.
References
Ajzen, I. and Fishbein, M. (1974). Influencing factors intention intentions and behavior relation. Human Relations, 27, 1-15.
Almahamid, S., McAdmas, A., Kalaldeh, T. & Alsa, T. (2012). The relationships between perceived usefulness, perceived ease of use, perceived quality information, and use e-intention the government. Journal of Theoretical and Applied Information Technology, 1, 30-44.
Bakabulindi, F. (2012). Does use of ICT Relate With the way it is perceived? Evidence from Mekerere University. International Journal of Computing and ICT Research, 6, 75-94.
Bizer , G., Larsen, J. & Petty, R. (2010). Exploring the valence framing effect: Enhances framing negative attitude strength. Political Psychology. 32, 59-80.
Indexed at, Google Scholar, Cross Ref
Buelga , & S. Pons, J. (2012). Aggression among teens via mobile phone e-Internet. Psychological Intervention, 21, 91-101.
Campbell, E. & Smalling, S. (2013). American Indians and Bullying in school. Journal of Indigenous Social Development, 2, 1-15.
Cardon, M., Gregoire, D., Stevens, C. and Patel, P. (2013). Measuring entrepreneurial passion: Conceptual foundations and scale validation. Journal of Business Venturing, 28, 373-396.
Indexed at, Google Scholar, Cross Ref
Davis, F. (1993). User acceptance of information technology: systems Characteristics, user perception and behavioral impacts. International Journal of Man Machine Studies, 8, 475-487.
Di Russo, D. and Douglas, M. (2013). The validity of the technology acceptance model in collaboration system software. Business and Management Reviews, 3: 1-5.
Elizalde, A. (2010). Descriptive study of coping strategies bullying in Mexican teachers. Journal of Research in Educational Psychology, 8, 353-372.
Fenoll, V. (2011). User’s assets and liabilities. The audience interactivity in digital media. Journal of Social Sciences. 51, 1-26.
Flores, L. and Mendieta, A. (2012). The perception of sensationalist journalism on the front, a case study. Journal of Communication. 14, 1-13.
Garcia, C. (2011). Structure of attitudes towards e - commerce. Contributions to Economics, 14, 1-10.
Garcia, C. (2012). Hybrid structure of socio - Demographic determinants of consumer electronics. Gepu, 3, 43-53.
Garcia, C. (2013). Reliability and validity of a measuring instrument internet search. Antioch, 5, (1) 27-34.
Garcia, L., Orellana, O., Pomalaya , R., Yanac , E., Orellana, D., Sotelo, L., Herrera, E., Sotelo, N., Chavez , H. and Fernandi , P. (2011). Peer bullying (bullying): Empathy and social mal-adjustment in participants Bullying. Journal of Research in Psychology, 14, 271-276.
Garis, A. (2010). Temporal logic model checking software. Origin and evolution to modern times. Fundamentals of Arts, 11 (21), 151-162.
Groshek , J. (2011). Media, instability, to democracy: examining the granger causal relationships of the 122 country clubs from 1943-2003. Journal of Communication. 61, 1161-1182.
Gu, M. & Goldfarb, B. (2010). Affect and the framing effect witting Individuals over time: risk taking investment in a dynamic simulation. Academic Journal of Management. 53, 411-431.
Hallak, R., Brown, G. Lindsay, N. (2012). The place identity relationships among tourism entrepreneur’s performance: a structural equation modeling analysis. Tourism Management, 33, 143-154.
Hee, D. McDaniel, S. (2011). Using an extended technology acceptance model in exploring antecedents to adopting fantasy sports league websites. International Journal of Sport Marketing & Sponsorships. 17, 240-253.
Indexed at, Google Scholar, Cross Ref
Hsuan, Y., Hsu, C., Shan, R. and Ming, C. (2013). The effects of website trust, perceived ease of use, and perceived usefulness on consumer online booking intention: Evidence from Taiwan B2B sector. Life Science Journal, 10, 1516-1523.
Izquierdo, L. (2012). The thematic consistency in international sections of the Madrid daily against local sections. Communication Papers, Media Literacy & Gender Studies. 1, 97-104.
Jalal, A., Marzooj, J. and Nabi, H. (2011). Evaluating the impacts of online banking motivating factors of the process of e-banking. Journal of Management of Sustainability, 1, 32-42.
Indexed at, Google Scholar, Cross Ref
Jyoti, J. and Jyoti S. (2011). Factors Affecting orientation and satisfaction of women Entrepreneurs in rural India. Annals of Innovation Entrepreneurships, 2, 1-8.
Indexed at, Google Scholar, Cross Ref
Kabeer, A. and Muhammad A. (2013). Factors affecting adopting in mobile banking in Pakistan: Empirical evidence. International Journal and Research in Business and Social Science, 3, 54-61.
Kotaman, H. (2010). Turkish early childhood educators’ sense of teacher efficacy. Education & Psychology, 8, 603-516.
Leon, B., Brown, E., Fajardo, F. and Gómez, T. (2012). Cyberbullying in a sample is or dents of secondary education: Modulatory variables and social networks. Journal of R and search in Educational Psychology, 10, 771-778.
Lopez, L. and Lopez, J. (2011). Models’ adoption of information technologies from the attitudinal paradigm. Notebooks EBAPE. 9, 176-196.
Mao, Y., Richter, M., Burns, K. & Chaw, J. (2012). Homelessness coverage, social reality, and media ownerships: Comparing to national newspapers to regional newspapers within Canada. Mass Communication & Journalism. 2 1/7.
Mehra, V. and Omidian, F. (2010). Predicting Factors Affecting university student's attitudes to adopt e-learning in using technology acceptance model. International Journal of New Trends in Education of Their Implications, 1, 33-43.
Mendoza, B. (2011). Bullying peer and scaling aggression teacher student relationship. Psychology Iberoamerican, 19, 58-71.
Mutengezanwa , M. and Fungai , M. (2013). Socio-demographic factors Influencing adoption of Internet banking in Zinbabwe. Journal of Sustainable Development in Africa, 15, 132-141.
National Institute of Statistics, Geography and Informatics (2010). XIII National Population and Housing Census. Mexico: INEGI.
Pepper, W., Aiken, M. & Garner, B. (2011). Usefulness and usability of a system multilingual meeting. GLOBAR Journal of Computer Science and Technology, 11, 34-39.
Ramayah, T. and Ignatius, J. (2010). Intention to shop online: The mediating role of perceived ease of use. Middle East Journal of Scientific Research, 5, 152-156.
Ramirez, P., Rondán, F. and Arenas, J. (2010). Influence of gender on the perception and adoption of e-learning: an exploratory study in a Chilean university. Journal of Technology Management of Innovation. 5, 129-141.
Reed, E. and Wolniak, G. (2005). Diagnosis or determination: Human capital assessment through explained theory and the concept of skills. Journal of Sociology, 1, 1-15.
Rojas, R., Garcia, V., Ramirez, A. (2011). How can we Increase Spanish technology firm? Journal of Knowledge Management. 15, 759-778.
Rojas, R., Garcia, V. Garcia, E. (2011). The influence on corporate entrepreneurship of technological variables. Industrial Management & Data System, 111 984-1005.
Sago, B. (2013). Factors Influencing social media adoption and frequency of use: And exam i nation of Facebook, Twitter, Pirenterest and Google+. International Journal of Business and Commerce. 3, 1-14.
San Martin, S. Lopez, B. (2010). Purchase possibilities B2C mobile phone sales compared with the Internet. Journal of Management, 10, 17-34.
Sandoval, R. Saucedo, N. (2010). Stakeholders in social networks: The case of Hi5 and Facebook in Mexico. Education and Humanities. 4, 132-142.
Sharma, R. and Abrol, S. (2011). Concentration of online banking. International Research & Education Consortium, 1, 22-35.
Smith, J. and Gracia, E. (2010). Internet and social support: Online sociability and AJU s you in psychosocial information society. Psychological. 7: 9-15.
Tekeher, S. (2013). Mathematics teacher educator's and preservice teacher's beliefs about the use of technology in teaching in African university. International Journal of Innovative Research Interdisciplinary, 12, 9-20.
Thiruchelvi, A. and Koteeswari, S. (2013). A conceptual framework of employees' intention to use Continuance of e-learning system. Asian Journal of Research in Economic and Business Management, 1, 3-6.
Torres, C., Robles, J. and Molina, O. (2011). Why do we use the information technologies and communications? A study on the social foundations of individual utility Internet. Magazine International of Sociology, 69, 371-392.
Wang, D. and Huynh, Q. (2013). An assessment of the role of the perceived usefulness in the adoption of management accounting practices. African Journal of Social Sciences, 3, 85-96.
Wiedmann , K., Hennings , N., Varelmann , D. and Reeh , M. (2010). Determinants of Consumers perceived trust in IT-ecosystems. Journal of Theoretical Applied Electronic Commerce Research, 5, 137-154.
Wirth, W., Matthes , J., Schemer, C., Wettstein , M., Friemel , T., Hânggli , R. & Siegert , G. (2010). Agenda building and setting in referendum campaign: the flow of arguments investigating among campaigners, the media, and the public. Journalism & Mass Media Communication. 87, 328-345.
Yuangion , Y. (2011). The impact of strong ties on entrepreneurial intention. An empirical study based on the mediating role of self-efficacy. Journal Entrepreneurship, 3, 147-158.
Received: 28-Aug-2023, Manuscript No. AEJ-23-14040; Editor assigned: 31-Aug-2023, PreQC No. AEJ-23-14040(PQ); Reviewed: 14-Sep-2023, QC No. AEJ-23-14040; Revised: 20-Sep-2023, Manuscript No. AEJ-23-14040(R); Published: 27-Sep-2023