Research Article: 2023 Vol: 27 Issue: 2
Comparative Analysis of Carbon Foot-Print and Energy Consumption of Crypto-Mining Consensus Methodologies
Sumit Kumar, Indian Institute of Management, Kozhikode
Citation Information: Kumar, S. (2023). Comparative analysis of carbon foot-print and energy consumption of crypto-mining consensus methodologies. Academy of Marketing Studies Journal, 27(2), 1-43.
Abstract
To investigate the major existing digital money agreement calculations considering various qualities that might assume a critical part in the drawn-out manageability of a cryptographic money biological system and to relatively assess a choice of existing calculations or cryptographic forms of money to reason the most feasible models as of now in presence. There are presently many cryptographic forms of money in the presence and the innovative spine of a significant number of these monetary standards is a blockchain-a computerized record of exchanges. To arrive at this objective, the expression "supportability of digital forms of money" was first characterized through the method for a point-by-point investigation of different properties that characterize digital currencies just as their award frameworks. To investigate existing agreement components and prize frameworks just as their present abilities, deficiencies, and spread, a writing audit was led. This establishes the framework for the resulting near examination on the presented agreement calculations and allowance of a reasonable variation that satisfies the primary manageability models distinguished for this unique situation: adaptability, security, power utilization, long haul administration just as the motivating forces and expenses of taking part in the agreement convention. Throughout this examination, just one existing agreement calculation classification under the name of delegated Proof-of-Stake (DPoS) has been displayed to best accomplish the qualities laid out above, and the particular illustration of cryptographic money called EOS is recognized and expounded exhaustively. Having laid out the underlying meaning of practical digital money, future innovative work toward this path is prescribed to audit the inconspicuous yet significant contrasts inside the class of PoS cryptographic forms of money to decide the most reasonable methodology and possibly refine the given definition. The serious course of adding squares to the chain is calculation escalated and requires huge energy input. The trust over the data is decreased radically, causing an increment in security and protection concerns step by step. Blockchain is one of the most outstanding arising advances for guaranteeing protection and security by utilizing cryptographic calculations and hashing. We will talk about the rudiments of blockchain innovation, agreement calculations, an examination of significant agreement calculations, and areas of utilization.
Keywords
Consensus algorithm, Distributed Ledger Technology (DLT), PoS, PoW, Sustainability.
CCS Concepts
Anonymity and privacy issues and measures to enhance them ➝ Consensus protocols for blockchains.
Acronyms
CPU :- Central Processing Unit
DAG :- Directed Acyclic Graph
DLT :- Distributed ledger technology
LPoS :- Liquid proof-of-stake
NPoS :- Nominated proof-of-stake
PoS :- Proof-of-stake
PoW :- Proof-of-work
tps :- Transactions per second
UTXO :- Unspent transaction output
zk :- Zero-knowledge.
Introduction
Cryptographic forms of money have seen an enormous flood in prominence and behind these new virtual monetary standards is a creative innovation called the blockchain: an appropriated advanced record where digital currency exchanges inside a record are confirmed by different customers or validators, inside the digital money's shared systems administration involving one of many shifted agreement calculations for settling the issue of dependability in an organization including numerous questionable hubs. The most broadly utilized agreement calculation is the PoW algorithm, and the PoS algorithm; notwithstanding, there are likewise other agreement calculations that use elective executions of PoW and PoS, just as other half-breed executions and a few by and large new agreement techniques. A near investigation of common agreement calculations and a portion of their peers that are as of now being used in current blockchains. Our fundamental spotlight is on the investigation of the algorithmic advances taken by every single agreement calculation, the versatility of the calculation, the strategy for the calculation rewards validators for their time spent on confirming squares, and the security chances present inside the algorithm.
Blockchain innovation is profoundly affecting the monetary and specialized areas giving a system to the making of decentralized monetary forms and various applications in various fields. At the center of the innovation, there is a consensus convention empowering the support of an appropriated record. As a general rule, current frameworks are intricate plans that carry out a blend of a cryptographic algorithm, conveyed strategies, and motivation-driven conduct.
The consensus algorithm is the central foundation of the blockchain and a significant assurance for the security of the blockchain framework. The blockchain is a decentralized framework, and the consensus algorithm numerically permits a huge number of hubs spread all over the globe to settle on the formation of blocks. The consensus algorithm additionally incorporates a motivating force instrument to advance the powerful activity of the blockchain framework, which is the reason for building trust in the blockchain. To put it plainly, the blockchain consensus system is a calculation for arriving at a distributed consensus on blockchain exchanges. Because of the great organization delay in the shared organization, the request for exchanges seen by every hub may not be by and large something very similar. In this way, the blockchain framework needs to plan a system to settle on the request for exchanges that happen inside a comparative timeframe. This calculation for settling on the request for exchanges inside a period window is known as a "consensus mechanism." Blockchain is a sort of conveyed framework. For concentrating various degrees of blockchain, we want various techniques to execute issue lenient agreement calculations to guarantee the security of the books. Regularly involved agreement instruments for blockchain public connections incorporate POW, POS, DPOS, PBFT, and a consensus mechanism with an assortment of systems.
Blockchain is the spine innovation behind digital currency and Bitcoin. By idea, Blockchain is a conveyed data set where exchanges are recorded in an upright and non-modifiable way. At present, Blockchain innovation is imagined as a strong structure for open-access organizations, decentralized data, handling, and sharing frameworks, and so on.
A Blockchain innovation-based framework is a traditional conveyed framework where every one of them taking part elements is topographically dissipated yet associated through various kinds of organizations. It was officially estimated and carried out in the years 2008 and 2009, separately Nakamoto (2008); Nakamoto, & Bitcoin (2008). Customary exchange the board frameworks require a unified believed party who is liable for the affirmation and capacity of exchanges. This clearly has many issues like expense, protection, effectiveness, security, and so on Decentralization is the central trait of Block chain which can be utilized to settle the above issues. Blockchain essentially gives a stage where different substances that don't confide in one another can work or share data in a typical stage. Bitcoin, the principal application that carried Block chain into the worldwide picture, is likewise the main cryptographic money created and utilized. Yet, with progress and top to bottom investigation of Blockchain innovation, its application is not any more restricted to the monetary area as it were. Maybe it has acquired a lot of ubiquities in different fields like Government, Technological endeavours, Supply chain, and so on Shen & Pena-Mora (2018). Predominantly Blockchain can be utilized in two distinct ways Permission-less and Permissioned. The consent less plan which is, for the most part, settled on an open climate like Bitcoin, Ethereum, permits anybody to join the framework just as permits keeping in touch with the common blocks. The consent less plan additionally gives equivalent honour to every one of the hubs if there should be an occurrence of the consensus cycle. Despite what is generally expected, a Permissioned Blockchain plan, for example, Hyperledger texture is overseen by a known arrangement of substances and is set up in a closed environment. However, every one of the elements are permitted to perform exchanges, just a proper arrangement of foreordained hubs can participate in the agreement interaction in a Permissioned Blockchain. Consensus algorithms hold a significant part in dealing with the effective and secure Blockchain framework. A portion of the well-known algorithm is Proof of Work (PoW), Proof of Burn (POB), Proof of Stake (PoS), Raft, Practical Byzantine Fault Tolerant (PBFT).
Blockchain is a carefully designed computerized record that can be utilized to record public or private shared organization exchanges and it can't be modified retroactively without the modification of all ensuing squares of the organization. A blockchain is refreshed by means of the agreement convention that guarantees a direct, unambiguous requesting of exchanges. Blocks ensure the trustworthiness and consistency of the blockchain across an organization of disseminated hubs. Different blockchain applications utilize different agreement conventions for their working. Byzantine adaptation to non-critical failure (BFT) is one of them and it is an attribute of a framework that ensures the class of disappointments known as the Byzantine Generals Problem. Hyperledger, Stellar, and Ripple are three blockchain application that utilizes BFT consensus. The best variation of BFT is Practical Byzantine Fault Tolerance (PBFT). Hyperledger texture with deterministic exchanges can run on top of PBFT.
Recently & late headways of remote correspondence, registering power, Internet, huge information, distributed computing increment the information step by step. The intense expansion in information makes a ton of issues like security, protection, trust, and confirmation. The obligation of IT is to guarantee the protection and security of gigantic approaching data and information because of the intense advancement of the IoT before long. The blockchain has arisen as one of the significant advances that can possibly change the approach to sharing tremendous data and trust to another. Building trust in the dispersed and decentralized climate without a believed outsider is a technological progression that can possibly change forthcoming situations of society, ventures, and associations. In the present time of huge information and AI, IoT is assuming an extremely pivotal part in practically all regions like social, financial, political, training, medical services. Troublesome innovations, for example, huge information and distributed computing have been profited from IoT. Because of the development of IoT, enormous and basic data is accessible over the Internet. The trust over the data is diminished definitely, causing an increment in security and protection concerns step by step. The blockchain is one of the most incredible arising advances for guaranteeing protection and security by utilizing cryptographic algorithms.
Blockchain innovation has diverted out from the idea of timestamping of an advanced report distributed in 1991. Time stepping of an advanced archive is utilized to keep up with the respect and honesty of the computerized report by a specific hub Haber & Stornetta (1990); Bayer et al. (1993). Cryptocurrency or we can also say that the Digital currency in any form like; Bitcoin has procured such a lot of distinction executed in the year 2009 Nakamoto (2008). There are numerous digital forms of money that exist, however, nobody gets equivalent to Bitcoin. It has arisen as a decentralized framework. Blockchain innovation is thought of and viewed as a public record. "Blockchain is a morally sound decentralized computerized public record of monetary exchanges that can be modified to record monetary exchanges as well as for all intents and purposes everything of qualities to work with information decentralization, straightforwardness, the changelessness of advanced record, security, and protection provenance, trust, and absolution in a shared organization." Blockchain is carried out as a computerized record on top of the Web which should be visible as a relationship to SMTP, HTTP, or FTP running on top of TCP/IP. Blockchain is affix just, unchanging, and just updatable with the assent of friends inside the organization is conceivable, which can be performed utilizing the inherent agreement component Bentov et al (2016).
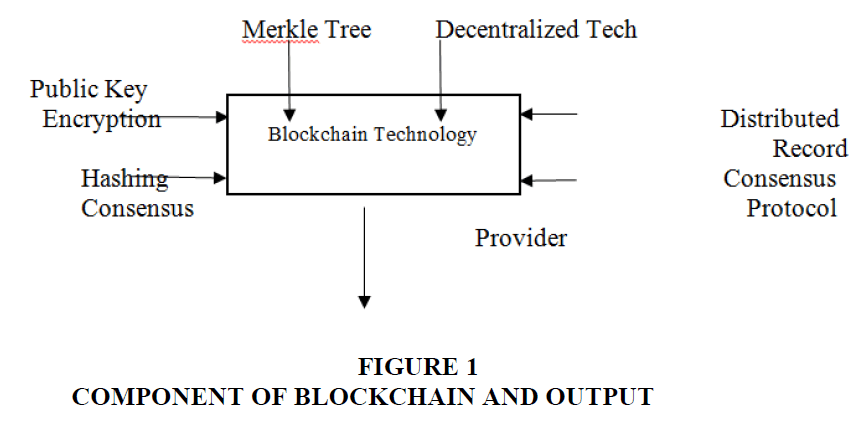
Blockchain innovation is the successful utilization of existing innovation, for example, decentralization, hash cash, public record, agreement, Merkle tree, public-key encryption, and hashing algorithm. Decentralization can be considered as the primary most significant point of view of blockchain innovation. Fundamentally, decentralization is a stage where different friends can take an interest to create blocks having similar power and participating. Each companion associated will have a similar position to make changes in the public record if appropriate. Network disappointment during the execution of the exchange doesn't influence the exchange a lot on the grounds that each companion makes their own different organization. The public record is documentation of each fruitful exchange which is accessible and sharable to all peers (in peer-to-peer network) (Figure 1).
1. Information Centralization.
2. Straightforwardness/Transparency.
3. Security & Privacy.
4. Sealed imitated record.
5. Permanent record
6. Computerization and Smart Contract.
7. Better approach for Storage capacity
The structure and the size of the block are execution subordinate. The greatest number of exchanges that a square can contain relies on the square size and the size of every exchange. Blockchain can't ensure exchange security since the upsides of all exchanges and balances for every open key are freely noticeable. A square has a square header, and a square body block header contains a square form, Merkle tree root hash, timestamp, N bits target limit of a substantial square hash, nonce, and parent block hash. Block body contains exchange counter and exchanges. Blockchain is a chain of squares. It is viewed as longer the chain of squares more will be focused on adding another square to give protection and security. Every one of the squares associated in the chain can profit security, decentralization, and permissionless office in frameworks where any clients can take partake without giving their character Castro, M., & Liskov (2002). It will prompt dealing with all pernicious actions in the exchange stage. Mining is only and only solution to such an issue. Excavators will conclude the block size and exchange likelihood, and whether or not it will add to the blockchain. On the off chance that the response is true, which chain will be utilized to add a block additionally chosen by excavators. At last, after examination, new blocks will add to the longest chain. Making a piece change of nonce will influence the entire hash of all replacement blocks. It is truly challenging to distinguish the genuine hash esteem. Diggers get a few motivators to keep up with their genuineness with block size and exchange. Change in exchange will give a copy of that specific block to each friend associated with that exchange. Variety in exchanges should be possible by diggers. It prompts a trustworthiness issue and neglects to plan a safe and private framework. Digger having a powerful processing machine will get more motivating force. The powerful figuring machine consumes a tremendous measure of power. It is a main issue for the digger. The answer for this is to utilize a powerful agreement calculation. There are a few consensus algorithms have proposed. We will examine a few most significant consensus algorithms and do a relative investigation Dai et al. (2019).
Cryptocurrency & Digital currencies and blockchain, by and large, have ignited far-reaching interest throughout the most recent years, prompting the development of endless cryptographic forms of money and various methodologies and algorithms to oversee their blockchain. The sort of consensus mechanism just as the characterized ascribes -, for example, block-time, - size, and - reward - direct different parts of a cryptographic money's economy just as its conceivable use cases. For instance, the utilization of digital money as a store of significant worth, instead of a method for instalment, varies insofar that the exchange time is somewhat irrelevant while putting away the cash long haul, though the recurrence and span of exchanges are basic with regards to moment installments. Most of the existing cryptographic forms of money - including Bitcoin as the perfect representation - are depending on the energy-concentrated Proof-of-Work (PoW) consensus algorithm. With the increasing reception rate and the shortage and expected future worth of such cryptographic forms of money, the exemplary PoW mining process with its expanding trouble and motivating force to hoard registering assets probably prompts an impractical biological system. The referenced motivation concerning computational power to tackle every PoW puzzle initially is established in the higher likelihood to procure the square award. This as result definitely prompts a weapons contest and solidification of hashing power, where the member with the most proficient equipment, least energy taxes, and most monetary assets wins. This thusly adds the square prize as extra capital that might be reinvested, along these lines further expanding the benefit. Considering decentralization as one of the centre components for the accomplishment of public blockchains, this perspective imperils the dependability of a blockchain, as a solitary substance might gather the vital hashing ability to adequately control it.
Literature Review
The first ever blockchain consensus protocol is PoW, Proof of Work. Bitcoin utilizes a PoW protocol to accomplish consensus, and its center thought is to guarantee the consistency of information and the security of consensus by presenting the registering power rivalry of appropriated hubs. New exchanges are continuously being produced in the Bitcoin framework, and hubs need to place real exchanges into blocks Nakamoto (2008); Antonopoulos (2014) recommended that the square header contains six sections, which are the variant number, the past square hash esteem, the Merkle root, the timestamp, the trouble target clamor, and the irregular number Antonopoulos (2014). The hub which can quickest tackle this issue will get the square bookkeeping right and the Bitcoin reward naturally created by the framework. PoW protocol exists pretty much in advanced monetary standards, for example, Dogecoin Li et al. (2020); Möser et al. (2016) and Litecoin. Nonetheless, to keep energy utilization economically, a few researchers likewise did a great deal of exploration work for this objective Huh & Kim (2019), by presenting a strategy for applying blockchain to a new and sustainable power exchange framework by introducing a consensus protocol that can work on its foundation and execution. After bringing up that manageability; objective in the plan of brilliant urban communities these days; actually, at present, there are no affirmations of economical urban communities where digital money mining is at full scale Fadeyi et al. (2020). Global exchange players might profit from the innovative reengineering of monetary cycles through the execution of blockchain, and the security and maintainability of the exchanging framework are ensured Chang et al. (2020). In the energy business, by utilizing the new blockchain innovation that invigorates advancement and development in the energy and a significant degree of computerization however savvy gets, the business stays away from energy waste and misappropriation "assaults" occur in the framework 17.
Enescu et al. (2020) a few nations endeavor to accomplish the objective of making a new and sustainable power exchange framework by introducing a consensus protocol that can work on its foundation and execution in security through using a blockchain framework Huh & Kim (2019). With respect to the versatility of the PoW framework, Back & Bentov (2014) proposed to move exchanges on Bitcoin to other digital money blockchain frameworks, along these lines expanding the throughput of exchange handling and further developing the exchange each second of the framework. Narayanan et al. (2016) brought up that the consensus protocol itself requires a lot of correspondence and figuring assets, and the number of exchanges will keep on expanding over the long haul, while the hub's registering restrictions will cause bottlenecks in the exchange cycle. Stifter et al. (2019) proposed a public blockchain circulated consensus protocol that arrives at the consensus of the gathering individuals through the Byzantine understanding. This protocol improves the exchange cycle capacity of the Bitcoin framework by separating hubs into bunches haphazardly and by confirming various exchanges.
Another significant blockchain consensus protocol is the PoS protocol King & Nadal (2012) Its primary element is the evidence of value rather than the verification of responsibility, and the hub with the most noteworthy value understands the expansion of new squares and the securing of motivation pay. Contrasted and PoW, Houy (2014) expressed that PoS is more similar to a lottery, gathering more money to win open doors, yet when a specific worth is consumed, the likelihood of winning again is decreased, subsequently lessening the effect of centralization brought by the more extravagant individuals.
There are likewise a few other generally utilized consensus protocols. Designated PoS consensus protocol, Miglani et al. (2020) in April 2014, can additionally accelerate the exchange speed and tackle the security issue that the hubs in PoS collect mint piece age limitlessly. RCAP (Ripple Consensus Algorithm) protocol Schwartz et al. (2014) is an organization exchange synchronization protocol that focuses on information precision. It depends on the consensus come to by unique hubs (likewise called "entryways"). PBFT protocol is concentrated by Castro & Liskov (1999), which is additionally the most regularly utilized BFT (Byzantine Fault Tolerance) consensus protocol which takes care of the issue of the failure of the first Byzantine adaptation to non-critical failure algorithm. PBFT protocol Sukhwani et al. (2017) lessens the intricacy of the algorithm from the remarkable level of the number of hubs to the square level of the number of hubs, making the adaptation to the internal failure algorithm of Byzantium more achievable in down to earth framework applications. PAXOS protocol Lamport (2001) is a consensus protocol in view of message passing and is exceptionally shortcoming open-minded. Pontoon protocol Ongaro& Ousterhout (2014) is the place where the center thought is that assuming the underlying condition of every data set is predictable, the steady information can be ensured by performing reliable activities. POOL (confirmation pool) protocol Edgington & Hayter, (2000) depends on customary dispersed consistency innovation, in addition to an information check protocol.
Blockchain innovation is somewhat new and the opposition among consensus protocols is serious. Subsequently, the benefits and bad marks of numerous consensus protocols are not stringently assessed, and it is likewise expensive, on the off chance that certainly feasible, to test them broadly in all actuality. Right now, the writing on looking at consensus protocols is developing, some of which verifiably broke down these protocols under a few aspects. We summed up these papers in Table 1, just as their thought about aspects and examination techniques. It tends to be observed that there is an absence of an all-inclusive system for consensus protocol correlation.
| Table 1 Existing Frameworks for Consensus Protocol Comparison | ||
| Paper | Considered Dimensions | Research Method |
| Saleh [2021] | Energy-saying, robustness | qualitative examination and game hypothetical investigation |
| Han & Liu (2017) | energy-saving, productivity, rationality, mistake lenient rate, extensibility | qualitative examination, and quantitative exploration. |
| Zhou (2017) | energy-saving, processing power & distribution | qualitative examination |
| Wei et al. (2020) | coin value record, demand fulfilled proportion, Gini index | agent-based model displaying and Simulation & reproduction |
| Bach et al. (2018) | energy-saving, endured force of the foe, TPS, market capitalization | qualitative examination, and quantitative exploration. |
Our correlation set incorporates DLT frameworks with a high market capitalization that share a basic shared factor: utilizing a PoS-based consensus algorithm. In PoS, validators with a higher stake - frequently as the DLT framework's local cash - impact the exchange approval more. In this manner, the scant asset of energy to stay away from Sybil assaults in PoW is supplanted by the scant asset of capital in the digital currency Sedlmeir et al. (2020). In spite of the shared characteristics, these frameworks vary in a scope of different perspectives, for example, the base edges to approve and designate, the need to secure tokens to stake ("holding"), and the engineering of motivators comprising of punishments ("cutting") and prizes past exchange expenses ("block rewards"). With regards to energy utilization, nonetheless, contrasts in the bookkeeping model, exchange approval mechanism, and hub authorizations setting, along with the compositional plan of every framework's particular PoS protocol, are of specific significance. In this part, we depict every one of the PoS-put together frameworks with a concentration with respect to those viewpoints. A full investigation of all potential variables is past the extent in that particular Research.
Ethereum 2.0: Ethereum is an exceptionally famous permissionless blockchain that is at present progressing as of PoW (Ethereum 1.0) towards PoS (Ethereum 2.0). In Ethereum 1.0, each occupied hub requires to accumulation every one of the 350 GB of present status information. In any case, the capacity of the full history of all exchanges is utilized by chronicle hubs as it were. There are likewise light hubs putting away just the header chains and mentioning all the other things on or after a complete hub on which they be subject to. The sharing proposition (Ethereum 2.0 step 1), intended to restrict register, stockpiling, & data transmission require, isn't so far dynamic.
Algorand: Algorand is a permissionless, account-based framework where transfer hubs store the whole record and non-hand-off hubs store roughly 1,000 squares. A proposition to restrict capacity needs through exchange termination and sharding ("Vault") isn't yet dynamic Gilad et al. (2017).
Cardano: Cardano is likewise permissionless and the main unspent exchange yield (UTXO)- based framework in our correlation set. In Cardano, hubs store all exchanges made. Its proposition for sidechains and sharing ("Basho") isn't yet dynamic. A likelihood of is being chosen as the block proposer for an age-weighted by the stake. Notwithstanding, it is feasible to appoint the stake to a stake pool, whose director gets rewards when the pool is chosen and afterward shares them with the delegators. Rewards are decreasing with the pool size assuming a pool is enormous that it surpasses an immersion boundary. Non-chose stakes confirm proposed blocks Badertscher et al. (2018).
Polkadot: In Polkadot's permissionless nominated Proof of stake (NPoS), every hub can appoint a stake to up to 16 validators, among which the stake is constantly isolated similarly. Prizes to validators are proportionate to approval work, not to their stake. Polkadot likewise recognizes chronicle hubs (putting away all previous squares), full hubs (256 squares), and light hubs (putting away just runtime and present status, yet no previous squares). The initial five shards ("parachains") have been now sold on the test net however have not been conveyed in the fundamental chain.
Tezos: In Tezos' permissionless liquid proof of stake (LPoS), the stake can likewise be assigned. A few agents are block makers, different representative’s check; both get awards for it corresponding to their stake Goodman et al. (2014). Hubs have a "full mode" putting away the essential information expected to recreate the total record state since the beginning square, yet not context-oriented information from a designated spot onwards; a "chronicle mode" where all blockchain information since the beginning square including logical information, for example, past equilibriums or marking privileges past the designated spots are put away; and "moving mode" that main stores the insignificant information that is important to approve blocks.
Hedera: Rather than the other five frameworks examined, Hedera is a consent network that utilizes a coordinated non-cyclic chart (DAG)- based information design to store the exchange history and applies PoS Baird (2016). The organization has its consensus hubs run exclusively by its board individuals right now, with the arrangement to open up to permissionless hubs in the future4. Exchanges don't shape impedes yet are spread through a "tattle about tattle" protocol where new data got by any hub is spread dramatically quickly through the organization Hedera (2021). The consensus computation appears as a weighted normal of all meddling hubs' data, for example, exchange requests, with the weight proportionate to a hub's stake Table 2.
| Table 2 Comparison of the Analysed DLT Systems in Accounting Model, Data Structure, and Node Permissions Setting | ||||||
| Platform | Accounting Model | Data Structure | Permissioning | |||
| Account | UTXO | Block | DAG | P’ned | P’less | |
| Ethereum 2.0 | Yes | Yes | Yes | |||
| Algorand | Yes | Yes | Yes | |||
| Cardano | Yes | Yes | Yes | |||
| Palkadot | Yes | Yes | Yes | |||
| Tezos | Yes | Yes | Yes | |||
| Hedera | Yes | Yes | Yes | |||
Research Objective and Methodology
The point of this work is to break down existing consensus algorithms considering various qualities that are recognized by writing to affect the drawn-out manageability of the biological system and to assess a determination of existing algorithms or digital currencies to derive the most maintainable models as of now in presence. The methodology follows the accompanying three stages:
a) Define the maintainability of cryptographic money concerning the consensus algorithm and award framework utilized as well as potential extra viewpoints distinguished throughout the span of this exploration.
b) Analyse existing consensus mechanisms and prize frameworks.
c) Define a prize framework and consensus mechanism (complete biological system) that intends to satisfy the characterized rules or expand on a current example.
This work can commonly be named subjective, pugnacious logical examination in the domain of social science because of its exploration plan and strategic methodology. The emphasis lies on the comprehension of what delivers a cryptographic money environment economical in the long haul rather. As per Webster and Watson, the contentious insightful strategy serves the examination of complex, experimentally caught connections to recreate reality, which permits the issue to be straightforwardly outlined. This is further strategy characterizes a proposed arrangement on an absolutely etymological level by creating contentions in view of existing experimental examinations or speculations. Because of the curiosity of this exploration point and with it the particular issue concerning the maintainability of cryptographic forms of money, the deliberate writing investigation is appropriate to coherently and etymologically find the extraordinary blend of supportability and digital currencies from the more-broad information on digital currencies, their consensus mechanisms, and prize frameworks, and manageability. In light of existing examination on these points, the underlying quest for significant writing is led utilizing a rundown of characterized terms. The catalogue of results yielded during this first stage was then examined in a subsequent stage, with the objective of expanding the premise of information progressively. The objective of this two-overlap approach eventually lies in accomplishing an incorporating outline of the current collection of information. This methodology through their discoveries that pugnacious rational examination is common and along these lines grounded in research did in the space of consensus algorithm from an energy utilization viewpoint. This exploration further brings up that the examination of existing related works reinforces the meticulousness of logical exploration.
Consensus Algorithm
We realize that blockchain is a decentralized conveyed network that gives security, permanence, straightforwardness, and protection. There is no understanding of centralization to check and approve the exchanges, yet, exchanges in the blockchain are viewed as totally confirmed and got. This is the aftereffect of a center algorithm present in each blockchain network called a consensus protocol.
A consensus algorithm is a strategy through which every one of the companions of the blockchain network agrees about the present status of the conveyed record. Along these lines, consensus algorithms give trust and unwavering quality among obscure companions in a dispersed climate. A consensus mechanism guarantees that each new square added to the blockchain is the main truth that is settled upon by all the blockchain hubs Lucas & Páez (2019).
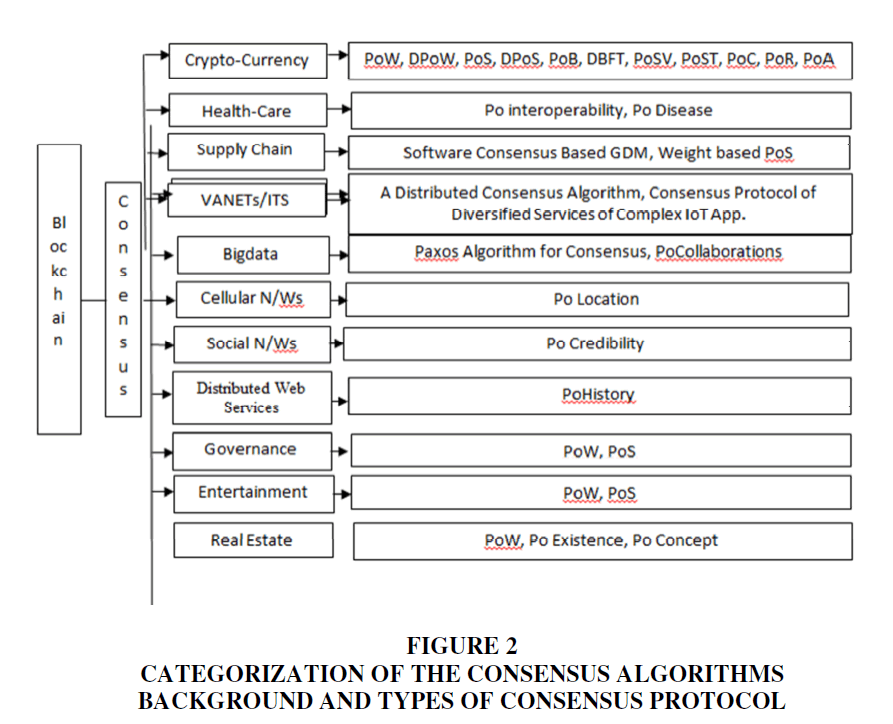
The blockchain consensus protocol contains a few explicit points that are coming to an arrangement, participation, cooperation, compulsory support of every hub in the consensus cycle, and equivalent freedoms to each hub. Consequently, a consensus algorithm targets observing a typical understanding that is a success for the entire organization. The above-talked-about applications are arranged and consensus algorithms in view of these classes are additionally examined underneath. Figure 2 shows a downright graph of the consensus and their circulation.
Well-known permissionless conveyed record innovation (DLT) frameworks utilizing proof-of-work (PoW) for Sybil assault obstruction have outrageous energy necessities, drawing harsh analysis from the scholarly world, business, and the media. DLT frameworks expanding on elective consensus mechanisms, preeminent proof-of-stake (PoS), intend to address this disadvantage.
In this paper, we venture out towards contrasting the energy necessities of such frameworks to comprehend whether they accomplish this objective similarly well. While numerous examinations have been attempted that investigate the energy requests of individual blockchains, minimal near work has been finished. We approach this examination hole by formalizing a fundamental utilization model for PoS blockchains. Applying this model to six original blockchains produces three fundamental discoveries: First, we affirm the worries around the energy impression of PoW by showing that Bitcoin's energy utilization surpasses the energy utilization of all PoS-based frameworks broken down by something like two significant degrees. Second, we outline that there are critical contrasts in energy utilization among the PoS based frameworks broke down, with permissionless frameworks having a generally bigger energy impression. Third, we call attention to that the kind of equipment that validators use extensively affects whether PoS blockchains' energy utilization is tantamount with or impressively bigger than that of brought together non-DLT frameworks.
Crypto-mining algorithm utilized as proof-of-work consensus algorithm (utilized for permissionless blockchain innovation, i.e., Bitcoin). It is utilized to control email and save such a framework from the for the swearing of assaults. The animal power technique is the best way to carry out the hashcash. The consensus algorithm is the core of blockchain innovation. The consensus is considered as the mainstay of the blockchain network. Numerous consensus algorithms have been proposed to get the framework protected from any noxious action in blockchain innovation: Proof of work (PoW), proof of stake (PoS), designated proof of stake (DPoS), commonsense byzantine adaptation to internal failure (PBFT), and so on, are some of them. Consensus guarantees the achievement of sensible choices so every friend ought to concur whether or not an exchange ought to be submitted in the data set Yadav & Singh (2021); Mingxiao et al. (2017). Blockchain utilizes the method of hash work, Merkle tree, nonce (to make hash work more enthusiastically to follow), and others to give information centralization, straightforwardness, security, and protection, carefully designed repeated record, permanent record non-renouncement, irreversibility of records, mechanization, and savvy contract, a better approach for putting away.
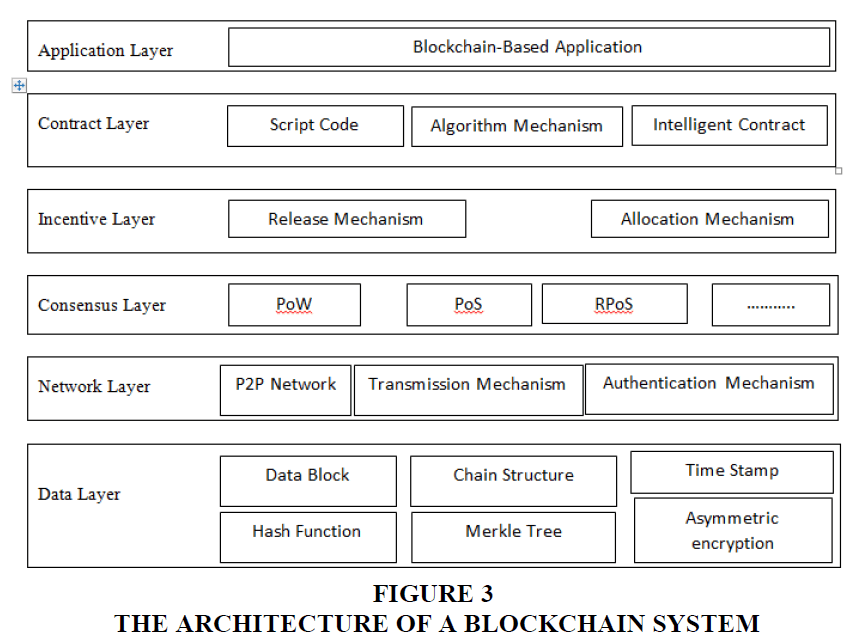
The abbreviations in the Figure 3 are shown in follows. PoW: Proof of Work, PoS: Proof of Stake, RPoS: Robust Proof of Stake, P2P: Peer-to-peer networking, is a distributed application architecture that partitions tasks between peers. See the table in Appendix A for a brief introduction to the acronyms.
The Proposed Comparison Framework and Two Consensus Protocols
In this segment, we initially propose another structure for contrasting consensus protocols and afterward present the PoW and PoS under this framework.
The Proposed Framework: -
Persuaded by the examinations in Table 1, we propose a correlation structure with a portion of the different-different basically four viewpoints:
1. Energy-saving: - With the quick financial turn of events, a lot of energy utilization brings about a lot of carbon dioxide discharges, which has essentially changed the worldwide environment and genuinely impacted the living climate of people. Hence, it is significant to plan a dispersed economy framework with low energy protection and carbon dioxide outflow Saleh (2021). This is the reason the vast majority of the papers in Table 1 considered the element of energy-saving.
2. Robustness: - As referenced in the Introduction segment, blockchain frameworks are likewise under many sorts of digital assaults, for example, the DAO assault Mehar et al. (2019) and arbitrary number assault [8], which turned into a colossal danger to the steady and maintainable improvement of blockchain frameworks Dolenc, et al. (2020). Consequently, numerous systems in Table 1 considered the connected aspects, for example, power 30.Saleh (2021) and mistake lenient rate Han & Liu (2017).
3. TPS is a significant pointer to gauge the effectiveness of a monetary framework, as it addresses the exchange volume finished by the framework each second Bach et al. (2018); Li et al. (2020). Interestingly, the notable blockchain frameworks (like Bitcoin and Ethereum) can reach under 40 TPS, making them difficult to deal with the exchange volume in reality Mearian (2020). Subsequently, we see that Han & Liu (2017); Bach et al. (2018) remembered the TPS for their systems.
4. Trade solicitation fulfilled proportion. A blockchain framework can be considered an exchange network among independent merchants who have the solicitation to one or the other purchase, sell or hold coins. Dissimilar to the financial exchange, brokers in the blockchain framework have no focal counter-party which gives clearing and settlement administrations. The ones who need to trade coins need to observe an exchange accomplice satisfy their requests. Subsequently, the exchange demand fulfilled proportion is characterized as the division of all-out fulfilled coin demands by complete coin demands Wei et al. (2020). The bigger the proportion is, the higher the exchange demand fulfilled proportion of a blockchain framework is.
Subsequent to deciding the four aspects above in light of Table 1, we see that the initial three aspects can scarcely be measured, in an examination article, for the accompanying reasons. To start with, the real energy utilization is straightforwardly impacted by the number of clients, particularly the diggers, in the blockchain framework. Notwithstanding, it is very hard to figure out the client numbers and the energy utilization, particularly when PoW or some energy-related consensus protocol is applied. Second, the power of a consensus protocol is frequently examined utilizing game-hypothetical investigation, which requires generally severe suppositions. Subsequently, we think about consensus protocols as far as strength hypothetically, as in Saleh (2021). Third, the greatest TPS of a consensus protocol is undeniably challenging to assess on the grounds that it depends on numerous PC and organization-related elements Wei et al. (2020). Henceforth, analysts for the most part talked about it hypothetically Zheng et al. (2018). Be that as it may, the specialist-based model created by Wei et al. (2020) can be changed to look at changed consensus protocols quantitatively.
In the following two subsections, we present a few standard consensus protocols in blockchain frameworks: - PoW and PoS. We likewise examine their exhibitions in a portion of these aspects: energy-saving, vigorous against assaults, and TPS.
Proof-of-Work (PoW) Consensus Algorithm
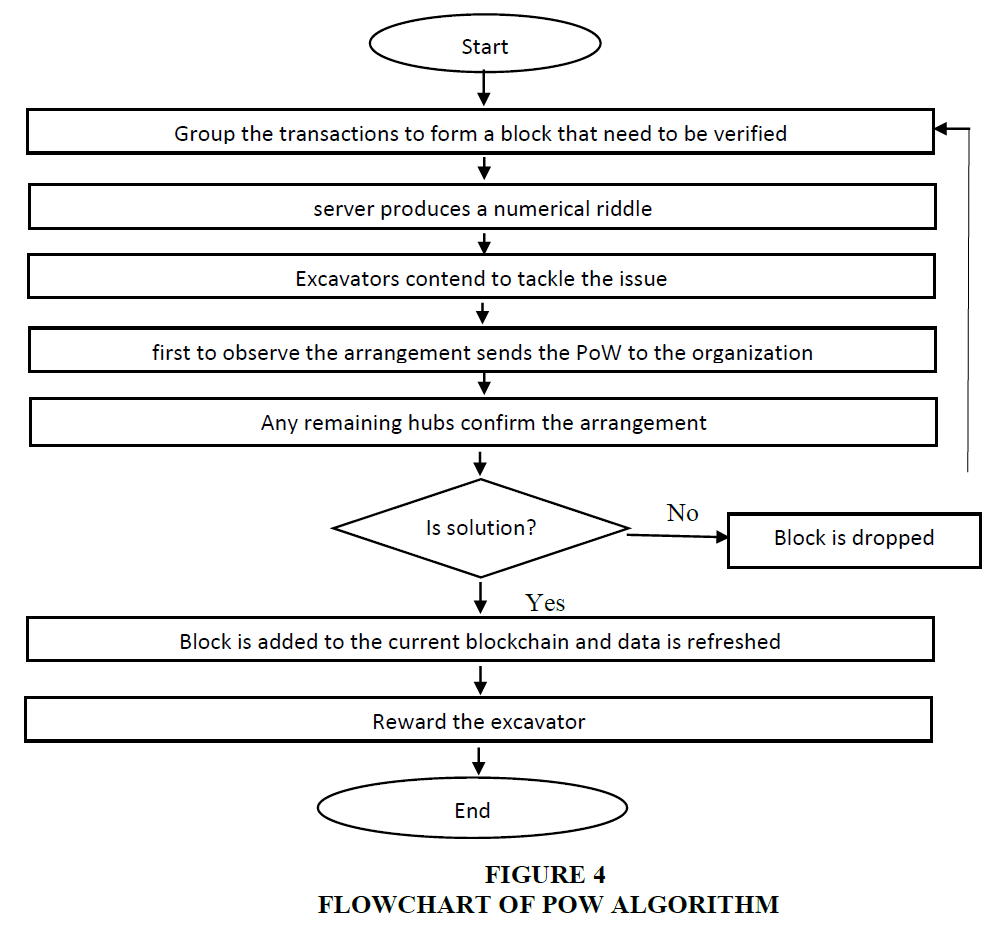
Proof of work was designed in 1993 and formalized in 1999. It guarantees monetary measures to forestall the disavowal of administration assaults. DoS assaults to keep real clients from utilizing the assistance. It is the deviation, i.e., hard on the requester side, yet simple to check for the specialist organization. The proof of work forestalls extortion hubs to take a few to get back some composure of genuine hubs. The idea of PoW is utilized past blockchain. Preferably, the idea is to create a test for a client, and the client needs to deliver an answer that should show some proof of work being done against that test. Whenever it is approved, the client acknowledged it. It disposes of the element that is slow or not proficient enough to produce PoW. In the blockchain, PoW is utilized to produce a worth that is hard to create and simple to confirm. To produce block hash, there are n driving 0. It will help in the arrangement and is known as a nonce (Figure 4).
The beast power strategy is applied to track down the worth of the nonce. The mix of the nonce and the square information which has been produced, including the hash worth of the past square emerges with the necessary driving 0. More is the worth of n, more the intricacy. PoW with regards to blockchain connotes that the calculation required is outstanding to the quantity of driving 0 expected in PoW. As the squares are anchored, re-trying will require a whole chain to be revamped. It likewise implies that some measure of calculation and exertion has been put resources into finding the answer for the issue [9].
Since large numbers of the excavators work in a similar permissionless organization, it will be hard to recognize which digger will submit the square and check the panel exchange block. In PoW, excavators are taking around 10 min to accumulate every one of the serious exchanges and produce another square for them. So presently what can be metadata contained in a square that should be past square hash, block hash, Merkle tree, nonce, and it makes the aggressors exceptionally miserable except if assailant ought not be mined for that reason excavators are granted a few impetuses in type of digital money when they produce another square Jaag & Bach (2017).
The method involved with implanting the consensus algorithm into the advanced money framework is as per the following:
1) The new exchange is communicated to the whole organization of diggers.
2) Each digger gathers exchange records and develops another Merkle tree.
3) The digger utilizes registering assets to observe a nonce that meets the current trouble esteem.
4) The digger tracks down a practical nonce arrangement and broadcasts the square to the whole organization.
5) Other excavators confirm the block.
6) If the exchange record in this square is legitimate, the square hash meets the trouble esteem necessity, and the square is the longest square among every one of the forks, then, at that point, other genuine hubs will build the new block after this block Figure 4.
PoW is likewise hard for the excavators to propose another square (i.e., to observe a nonce that won't influence the past square hash), and diggers should show their earlier taken care of business which he had created prior to proposing another square to different hubs. Timestamping should likewise be an element of the square so that later companions can't differ on its exchange made. The serious issue for the diggers is to get the number of zeros the hash code ought to be produced. In PoW, the hub having a powerful machine will perform more exchanges to be submitted and create another square. This will prompt higher motivations toward hubs using the more impressive machine in producing new squares Bentov et al. (2016).
Advantage
1) High level of decentralization: the algorithm is straightforward and simple to carry out, the hubs can enter uninhibitedly, and the level of decentralization is high.
2) High security: - harm to the framework requires a colossal venture, security is incredibly high.
3) Machine trust: - The decision of square makers is addressed by the hub tackling hash work. The last course of creating and checking the proposition to the consensus is an absolutely numerical issue. The hubs can arrive at a consensus without trading extra data. The entire cycle No human inclusion is required.
Disadvantages
1) Long affirmation time: - In request to guarantee the level of decentralization, the affirmation season of the square is hard to abbreviate.
2) poor expansion: helpless development and no irrevocability, the requirement for designated spot mechanism to compensate for the conclusion, yet the chance of arriving at a consensus with the expansion in the number of affirmations has additionally expanded dramatically.
3) waste of resources: - misuse of assets & the trouble of mining, combined with the overhaul of equipment, bringing about twofold misuse of equipment + assets.
Proof of Burn
The Proof of Burn consensus mechanism was created by Ian Stewart. This mechanism is utilized in P4Titan Slimcoin (2018). Here, diggers send a few coins to an arbitrary invalid obscure location prior to making a square. The location changes after each square are made. As it is an invalid location, the coin which is shipped off that address is unusable or burned. This address is otherwise called an 'eater address'. Among the excavators, just one can make the following square and get a prize. Here, the award incorporates the exchange charges and the mining coin.
The Proof of Burn algorithm rouses long-haul venture. The chance of getting an award depends on the hour of the venture. Since each exchange in Proof of Burn is recorded, the financial backer who constantly contributes for a significant stretch gets more honors towards accomplishing a prize. Notwithstanding having a transient misfortune, financial backers can benefit through long-haul speculation. A downside is as the coin is burned; a financial backer stands to lose extensive cash prior to being compensated. The mechanism doesn't give any assurance that, after a specific measure of the venture, the financial backer will have a chance to mine the coin. Likewise, on the off chance that the quantity of diggers in the organization builds, the possibility of getting a reward turns out to be less.
Proof of burn is an elective technique for agreeing to a blockchain network. The thought behind it is that diggers ought not to burn through energy or time to demonstrate that they have done something hard to do. In this algorithm, excavators need to burn a portion of their all-around claimed cryptographic forms of money to get rewards. Burning here implies that a client is expected to send some cryptocurrency to an "eater address" to get coins, tokens, or mining honors on the organization. Proof of burn is an elective technique for agreeing to a blockchain network. The cash shipped off an eater's location is unrecoverable and nobody can spend it once more, so it is called burnt and is unavailable for general use. Very much like the cycles in PoW, burning coins is a costly movement for the client however consumes no assets and energy. The main asset being utilized in PoB is the client's eagerness to assume a momentary misfortune to get a drawn-out remuneration on account of eater addresses, the location is produced haphazardly and isn't related to any private key. Not having any connection with any private key implies that the cash put away in an eater address is essentially blocked off and it's not possible for anyone to spend it. It should be noticed that all PoB cryptographic forms of money require burning proof of work mined digital currencies like bitcoin. The more coins a client burn the more possibilities she/he will get to track down the following square. This is additionally like PoS in which the rich would most presumably get more extravagant.
To sum up its credits, it is making greater soundness as we probably are aware somebody who hazards a momentary misfortune and spends his cash thusly, would remain in the organization for a more extended time frame to acquire benefits. In addition, as there is no component making the financial backers brought together, PoB improves decentralization and makes a disseminated network. Then again, burning PoW mined coins burns through energy and time. Assuming one day the worth of PoB coins becomes more prominent than the PoW burned coins, we could say that PoB is more energy-effective than PoW, and the squandered coins, energy, and time would be in some way recuperated.
Proof-of-Stake (PoS) Consensus Algorithm
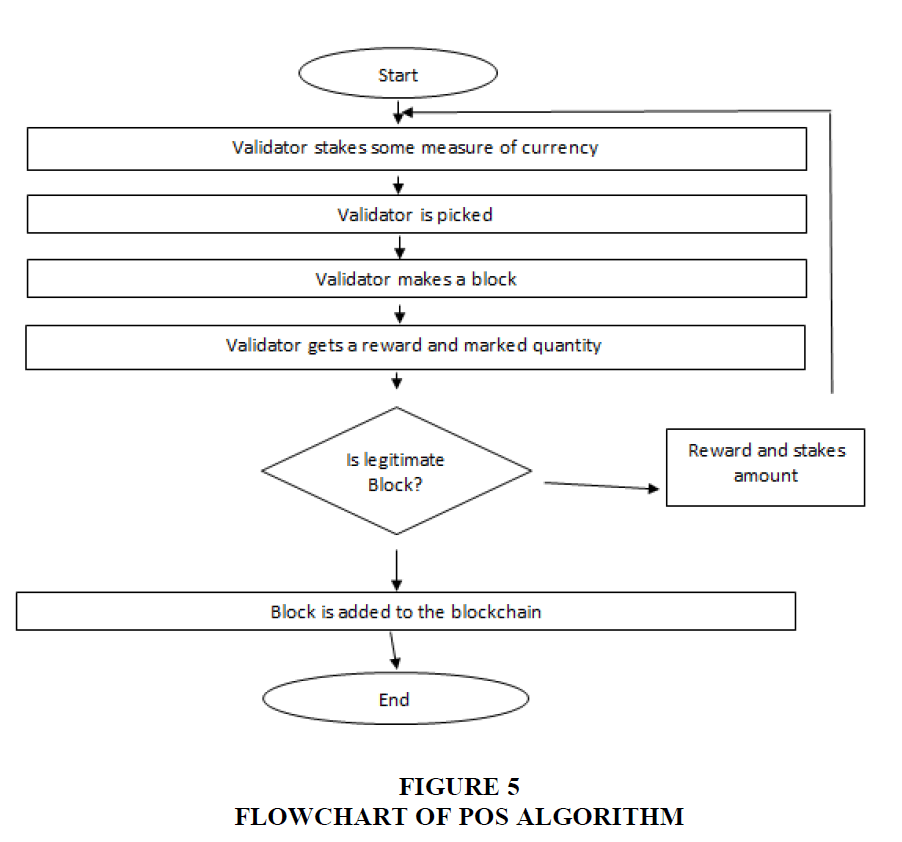
In proof of work, diggers are expected to give an answer for the complex cryptographic hash issue. Diggers contend with one another to turn into the first to track down the nonce. The primary excavator who addresses the riddle gets the prize. Mining in a proof-of-work algorithm requires a great deal of processing power and assets (Figure 5). All the energy is utilized to settle the riddle. The higher the computational power, the higher the hash rate, and in this manner, the higher the possibilities mining the following square. This prompts the arrangement of mining pools where diggers meet up and share their computational ability to settle the riddle and divide the prize between themselves. Proof of work utilizes an enormous measure of power and supports mining pools which take the blockchain toward centralization Zheng et al. (2018). To tackle these issues, another consensus algorithm was proposed called proof of stake. A validator is picked arbitrarily to approve the following square. To turn into a validator, a hub needs to store a specific number of coins in the organization as a stake. This cycle is called marking/stamping/manufacturing. The possibility of turning into the validator is relative to the stake. The greater the stake is, the higher the possibilities approve the square. This algorithm leans toward the rich stake Figure 5.
When a validator attempts to support an invalid square, he/she loses a piece of the stake. When a validator supports a substantial square, he/she gets the exchange charges and the stake is returned. Subsequently, how much the stake ought to be higher than the all-out exchange expense to keep away from any false square being added. An extortion validator loses a greater number of coins than he/she gets. In the event that a hub doesn't wish to be a validator any longer, his/her stake, as well as exchange expenses, is delivered after a specific period (not promptly as the organization needs to rebuff the hub in the event that he/she is associated with a false square). Proof of stake doesn't request tremendous measures of electrical power, and it is more decentralized.
It is more harmless to the ecosystem than proof of work. 51% assault is less inclined to occur with proof of stake as the validator ought to have essentially 51% of the multitude of coins which is an exceptionally colossal sum. Proof of stake is performing for the more defensive way and to utilize less use of the ability to execute the exchange. In some cases, an individual having more cryptocurrency (i.e., Bitcoin) will have a greater likelihood to mine another square, however, once more, it was emerging the issue of strength when an individual has half or more and afterward it will have the most elevated likelihood to mine the square so the arrangement has been made as far as a few randomization protocols where irregular hubs are chosen to mine another square. Since it was additionally observed that hubs are monasteries beginning with PoW, they move to PoS for better and smoother utilization.
In PoW, diggers can mine just one square, and picking some unacceptable fork is exorbitant for excavators. In the event that an excavator picks some unacceptable branch, later, another branch turns out to be the longest chain, and the digger's assets for mining the square are squandered. In PoS, the validators can fashion different forks, and picking some unacceptable fork isn't exorbitant as excavators didn't spend costly assets. Each other validator can chip away at numerous branches. A misrepresentation validator can twofold enjoy with the cash. A hub can remember a false square for one branch and hang tight for it to be affirmed by the assistance; whenever it is affirmed, the hub can twofold spend the cash by remembering the square for the other branch Sankar et al. (2017). A noxious validator can endorse a "terrible" block in one fork and a "great" block in the other. On the off chance that the equivalent validator again finds the opportunity to approve the squares, he/she may work in the "terrible" branch, making the "awful" branch longer than the "upside" one. Consequently, other validators, as well, may begin chipping away at the longest chain that incorporates a fake square. In PoS, validators ought to have some measure of cash for the stake. The issue is the means by which the validators would figure out how to obtain cash toward the starting when the PoS was at its underlying stage. Proof of stake needs the coins to be disseminated at first as the coins are required for manufacturing. In Pos, the assailant can return to the past squares and change the set of experiences. The aggressor might get some old private keys from the old validators who have lost interest in producing. A hub marking a bigger measure of cash than different hubs have more possibilities turning into the validator.
Advantage
1.) Save resources: - In secure assets mining doesn't squander power, and the money is in a premium bearing mode.
2.) The block confirmation time is fast: The block affirmation time is quick in PoS. The PoS consensus further develops the block affirmation effectiveness since hub mining doesn't need actual estimations and just requires value proof, which significantly lessens the ideal opportunity for consensus affirmation.
Disadvantages
1.) Poor security: The execution rules are complicated, there are many moderate advances, and numerous human elements are involved, which is not difficult to create security openings.
2.) Point check: As with the PoW consensus mechanism, there is no conclusion, and a designated spot mechanism is expected to compensate for the irrevocability.
3.) Matthew effect: The aggregate sum of value under the POS consensus mechanism is duplicated by the number of coins held when holding the cash. It will undoubtedly shape a champ bring home all the glory circumstances.
4.) The accounting node incentive problem: The bookkeeping hub motivating force issue and mining in PoS isn't squandering power costs, despite the fact that PoS mining has a specific impetus, the motivator for diggers is exceptionally restricted contrasted with PoW.
5.) Nothing-at-Stake attack: Because mining doesn't cost, so the fork assault achievement rate is exceptionally high, it is not difficult to be a parted assault. Also, even without a 51% interest, you can effectively send off a fork assault.
Securing Proof-of-Stake Protocols
The Securing Proof-of-Stake Blockchain Protocols essentially plunges into two unique arrangements that might reduce or tackle the didn't regularly know anything in question and long-range assaults that, as per the creators, most existing PoS variations actually endure. Aside from the two methodologies clarified, the internal functions of a nonexclusive PoS consensus protocol are summed up and different past and current weaknesses are nitty-gritty.
The SPoS as it examinations current security worries of PoS frameworks repeats past weaknesses and sums up the means taken for relief. As security is one of the vital traits in any cryptocurrency and consequently profoundly applicable to its drawn-out maintainability, this source will uphold the examination or possibly the origination of a reasonable protocol, would it be a good idea for it utilizes the PoS algorithm or a variety thereof.
Proof of Capacity
The Proof of Capacity algorithm honours the limit of an excavator's stockpiling rather than hashing power. The idea of Proof of Capacity (PoC), is otherwise called Proof of Space (PoSpace). The objective of this mechanism is to diminish the utilization of computational energy, just like the case in Proof of Work. Rather than ascertaining the hash in each square, Proof of Capacity permits putting away the rundown of potential arrangements, even prior to mining the square. The excavator who has more space can store more arrangements, which gives the digger a benefit to address the square. This innovation was first presented in Burst coin Larsson & Thorsén (2018).
Here, excavators utilize the free spaces on their hard circles to mine free coins. The principal cryptocurrency that used this algorithm was Burst coin established in 2014. The PoC algorithm comprises of plotting the hard drive which means processing and putting away arrangements on your hard circle before the mining starts. A few arrangements are quicker than others. Assuming that a hard drive has put away the quickest (nearest) answer for the new square's riddle, then, at that point, it wins the square.
In Burst coin, carrying out the PoC algorithm comprises of two phases. The primary stage is named plotting in which diggers make something named "Nonce". Nonces are made by continued hashing of information including excavator's ID utilizing an extremely sluggish hash work known as Shabal. As the Shabal hashes are difficult to work out, they are determined ahead of time and are put away in the hard drive as nonces. The more liberated space a digger designates to plotting, the more nonces would be made.
It should be noticed that not at all like bitcoin which needs extraordinary equipment like ASICs and CPUs/GPUs for mining, the main equipment used in PoC is any ordinary Hard Disk Drive, and accordingly, nobody can exploit unique equipment. In addition, utilizing Hard Drives is supposed to be multiple times more energy-productive than ASIC-based mining and there is no compelling reason to persistently update your equipment, as an old Disk Drive can likewise store nonces. Also, as everybody has simple admittance to Hard Disk drives, the organization would stay decentralized.
This mechanism contains two stages: plotting the hashes and mining the coins. By constant hashing of information, utilizing his/her id, the digger plots generally conceivable nonce esteems that can contain arrangements. Here, a portion of the algorithms is utilized for hashing. In the wake of plotting, an excavator begins the mining system. During this cycle, the excavator produces a scoop number. With that scoop, the excavator computes the cut-off time worth of each conceivable nonce s/he plots. Among those cut-off times, the most minimal cut-off time is gotten by the excavator. A cut-off time is edge esteem in seconds to fake a specific square. Whenever a digger chooses a base cut-off time and no other excavator can produce the square in the following cut-off time period, the digger can request the award and fake the square. Proof of Capacity is versatile and cost-proficient, as diggers don't need to rival each other by utilizing computational power. Nonetheless, it can prompt another contest over extra room to plot more nonces.
Proof-of-Activity (PoA) Consensus Algorithm
Since PoA can be considered as the blend of proof of stack (PoS) and proof of work (PoW), PoA changes the answer for PoS. To submit a few exchanges in a square concerning mine another square, then, at that point, to submit that mined square into the data set, and afterward, the greater part of each hub signs the block for approval Li et al. (2020) (Figure 6).
Proof of Importance
Proof of Importance (PoI) is an advanced consensus mechanism similar to Proof of Stake which was first used in NEM cryptocurrency Bach et al. (2018). To eliminate the drawback of the rich becoming richer, which exists in Proof of Stake, the Proof of Importance mechanism introduces some new regulations, including a score-based protocol known as the Proof of Importance score. A participant with a higher score has an increased possibility of being selected as a validator. This score is calculated according to three factors: vesting, transaction partner and number and size of transactions in the previous 30 days.
The participant who invests more coins in the network receives a higher PoI score. The number of harvest coins should be at least 10,000. The score also increases with the size and number of transactions. More transactions bring an increased possibility of being a validator. Also, these transactions should be net transfer. If two or more users perform the same transaction among themselves, the PoI score will not change
Proof-of-Elapsed Time Consensus Algorithm (PoET)
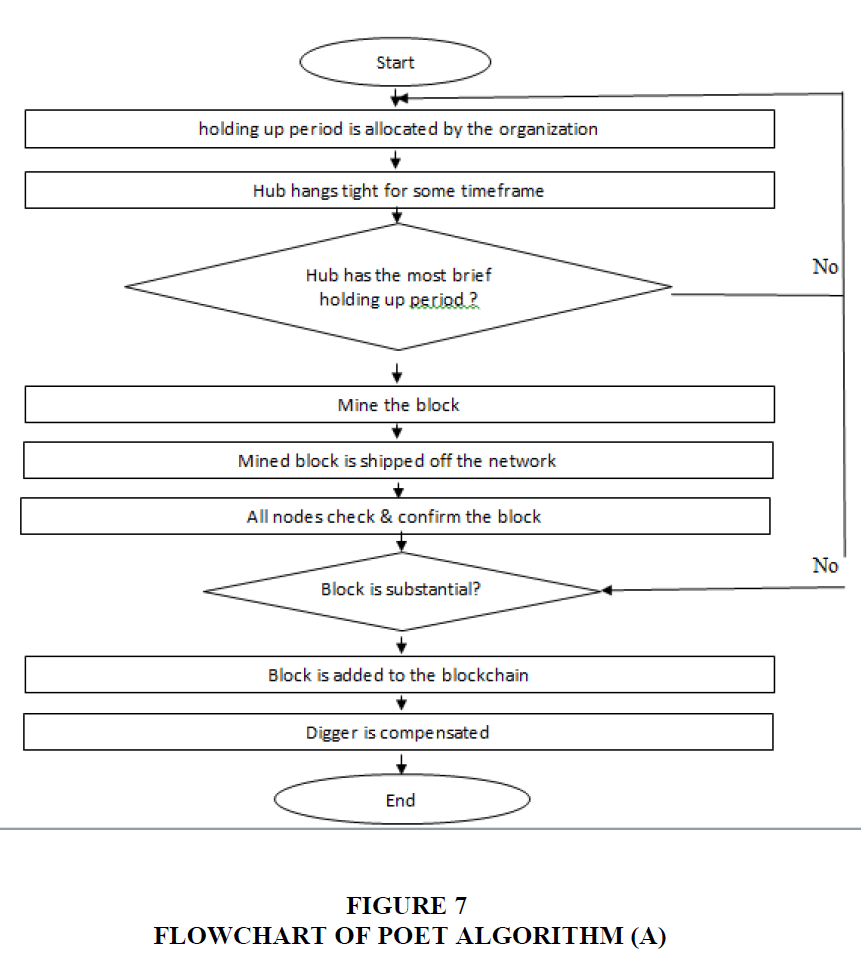
The PoET algorithm recommends a few normal strides to choose the excavator that would mine another square. Every excavator that had mined the earlier square had trusted that arbitrary time quantum will do as such. Any excavator which is proposing any new square to dig should hang tight briefly, and it will be not difficult to decide if any digger which is proposed for the new square to dig has sat tight for quite a while or not by concluding that a digger has used a unique CPU guidance set (Figure 7)
Tangle
Tangle is the consensus protocol utilized in IOTA Kusmierz (2017). Particle is a cryptocurrency that is fundamentally evolved to keep up with the environment among IoT (Internet of Things) gadgets. A significant distinction among Tangle and other consensus protocols is that rather than utilizing a Blockchain network it utilizes a Directed Acyclic Graph (DAG) to plot the organization. DAG is a unidirectional noncyclic chart organized organization that makes it conceivable to confirm numerous exchanges by various diggers simultaneously.
Tangle is a persistently developing record, where unverified exchanges are known as tips. An unverified exchange should be checked by something like two exchanges or hubs in the organization. These two hubs are arbitrarily chosen by the Markov Chain Monte Carlo (MCMC) procedure. To check the exchange, a little Proof of Work, for example, hash cash, is required. Nonetheless, confirming by two hubs isn't to the point of finishing the exchange. The new hub additionally needs to affirm somewhere around two all the newer exchanges to finish the first exchange. Hence, to finish a singular exchange, a hub needs to check other inadequate exchanges. This keeps up with decentralization in the organization and each member puts forth a practically equivalent attempt to keep up with a consensus.
Tangle doesn't need an exchange expense. Since every member has practically a similar commitment in view of the exchange number of people, no expenses or rewards are required. Additionally, adaptability increments with the organization's development. With more interest, more exchanges can be checked simultaneously. Nonetheless, the organization actually requires a lot of energy utilization as a little Proof of Work should be directed to check an exchange.
Practical Byzantine Fault Tolerance (PBFT)
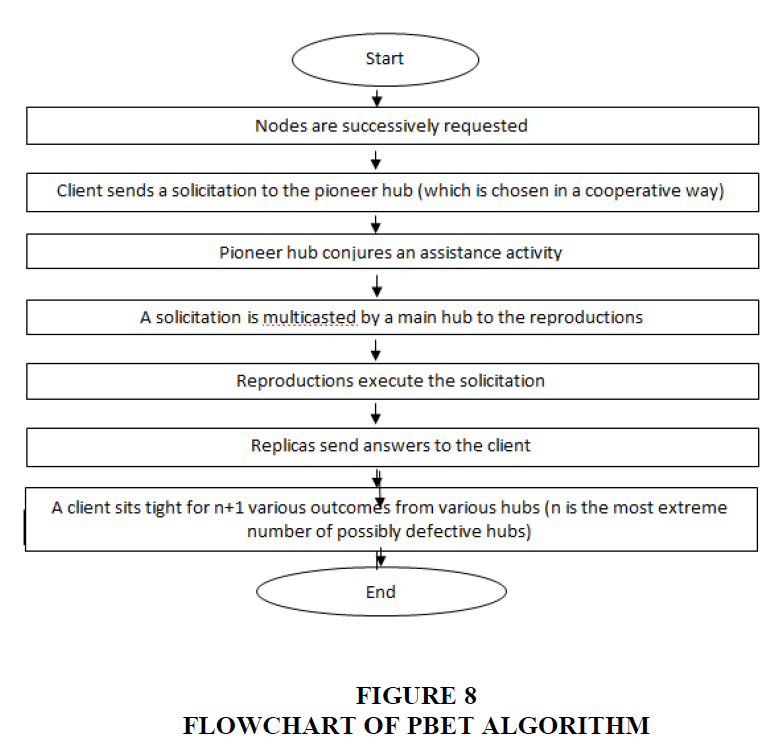
PBFT algorithm is concerned when at least one hub in any organization become flawed and act malignantly that subsequent in ill-advised correspondence among all hubs associated with that organization. Such things bring about a postponement in working, though time is an intense worry as we as of now are working in a nonconcurrent framework where on the off chance that no less than one shortcoming happens, it would be difficult to tackle the consensus issue. It will likewise produce separation in reactions of different hubs. PBFT works for the authorization model. In viable byzantine adaptation to non-critical failure, state machine replication happens at various hubs and the client will hang tight for a n + 1 reaction from all hubs where n is the quantity of broken hubs, however it isn't giving the legitimate answer for this since n + 1 can't decide the greater part vote in favour of the client. PBFT applies to the nonconcurrent framework Correia et al. (2010).
For the most part, PBFT was achieved after PAXOS and RAFT that both have greatest adaptation to internal failure of n/2 − 1 among all hubs where n is by all accounts the quantity of flawed hubs Zheng et al. (2017). Be that as it may, PBFT is getting around 3n + 1 reaction among all non-flawed hubs where not entirely settled as the defective hubs. As we are examining the state machine replication, then, at that point, it is essential to get it (Figure 8).
The Practical Byzantine Fault Tolerance (PBFT) is a true replication of the BFT consensus mechanism. In everyday practice, on account of cryptocurrency, a gathering of people is predefined to approve the exchanges in a PBFT model [8]. Whenever another exchange emerges, the predefined bunch gets the exchange and arrives at a consensus. Among the hubs, one hub is considered as a pioneer hub and different hubs as a reinforcement hub. To arrive at a consensus, the hubs vigorously speak with one another. They likewise need to confirm that no information has been changed during the transmission. In a PBFT model, no less than 2/3 of the general hubs need to arrive at a consensus to settle on a choice. It doesn't make any difference if 1/3 of the general hubs are pernicious. The exchanges are handled in four stages. Initial, a client demands an exchange from the pioneer. The pioneer then, at that point, communicates the exchange to the reinforcement hubs. In the third step, the reinforcement hubs check the exchange and advise the client. The client hangs tight up to a specific number of similar answers. This specific number should be more than the quantity of vindictive hubs which the framework can permit. The pioneer hub might change after a specific period and furthermore assuming that the incomparable larger part quantities of reinforcement hubs choose if the pioneer is noxious. In cryptocurrency, PBFT is executed [8]. The Delegated Byzantine Fault Tolerance (DBFT) is a marginally changed form of PBFT. In Neo, DBFT is utilized as the consensus mechanism Bach et al. (2018) Figure 8.
The entire algorithm works as per the accompanying system. There are 3n + 1 hubs in a circulated framework, which can endure n Byzantine blunder hubs.
1) The client demands the calling administration from the essential hub.
2) The expert hub multicasts the solicitation to the auxiliary hub.
3) The optional hub executes the solicitation and sends an answer to the client.
4) The client gets n + 1 answers with a similar response, and the client gets the mentioned information.
Since the Byzantine shortcoming lenient algorithm has to know the number of hubs ahead of time, the hubs can lay out associations with one another, and the hubs can't be progressively made due, which can't meet the prerequisites of the public chain. Be that as it may, in specific conditions, the blockchain consensus can be accomplished utilizing the PBFT algorithm, for example, the China Central Bank's electronic charging framework, Hyperledger Fabric, whose number of not entirely set in stone.
Advantage
1.) The fundamental organization is steady without a fork
Disadvantages:
1.) Low scope of application: Low extent of utilization is just for collusion chain and private chain.
2.) the system, poor scalability, the framework, helpless versatility.
3.) The system node is fixed: the framework hub is fixed and cannot adapt to the open climate of the public chain, just applies to the collusion chain or private.
4.) Low fault tolerance: In Low adaptation to non-critical failure; The PBFT algorithm requires the complete number of hubs f>=3n+1 (where n addresses the number of detestable hubs). The quantity of bombed hubs of the framework will not surpass 1/3 of the hubs of the entire organization, and the adaptation to internal failure rate is somewhat low.
Simplified Byzantine Fault Tolerance (SBFT): -
In an improvement on byzantine adaptation to internal failure (SBFT), a square accumulates every one of the exchanges, clusters them, and approves them in another square. Namasudra et al. (2021). Every one of the hubs observes the guidelines of a square generator to approve every one of the exchanges. A square endorser approves these exchanges and adds its own mark. In this way, assuming any of the squares miss one of the keys, it is dismissed. This algorithm utilizes an embraced rendition of a Practical PBFT consensus algorithm. This protocol is additionally expected to give enhancements over PoW. There is a solitary validator who is a known party and the idea of the record is permissioned. The validator structures another square with a heap of proposed exchanges. Consensus is accomplished when a base number of hubs support a square. The number of hubs to arrive at a consensus is 2n + 1 that has 3n + 1 number of hubs where f is the number of broken hubs. For instance, in the event that a framework has seven hubs and two of them are broken, 5 hubs should concur.
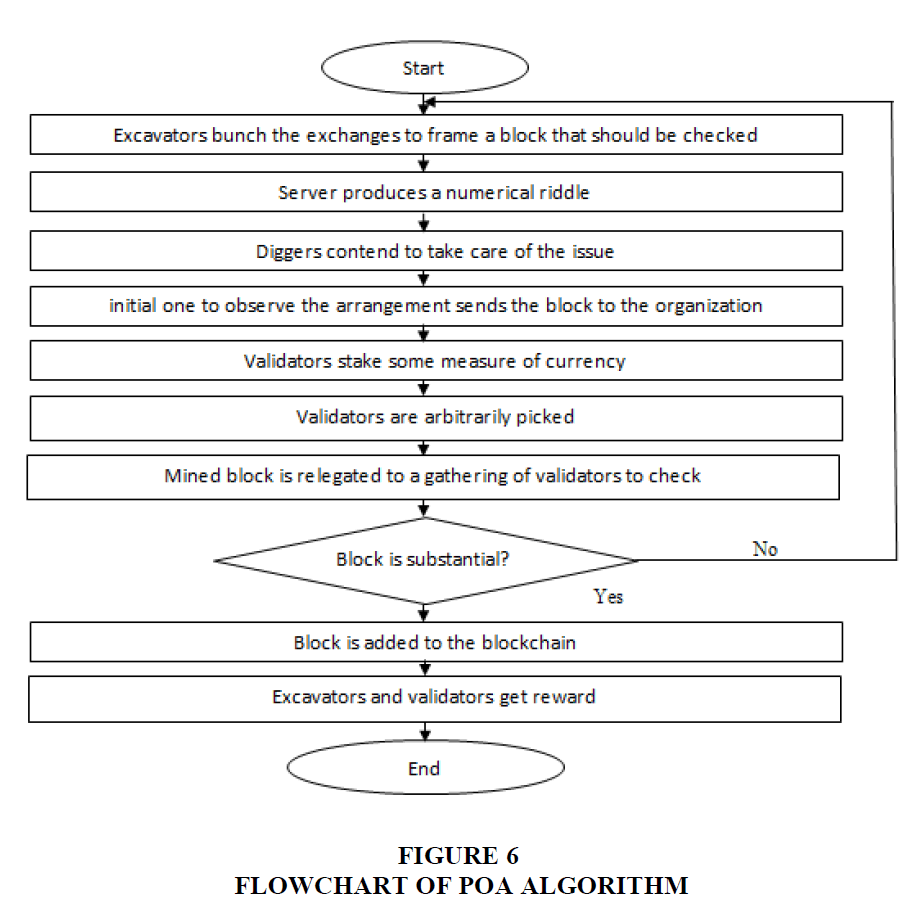
Delegated Proof-of-Stake (DPoS) Consensus Algorithm
Designated proof of stake is like the PoS algorithm. It alludes to a more decentralized design in the blockchain organization, and it additionally changes the way by which energy can be used regularly exceptionally less in executing the legitimate control. Designated proof of stake for the most part offers the opportunities to investors to give their votes to the people who need to mine further coming the square ought to be submitted in the information base. Cryptocurrency holders will likewise have the potential chance to choose the excavator to mine a further square. Will pick the representatives which will be liable for the mining of new square, and some way or another a few observers are likewise chosen on political race premise by cash holders to perform appropriate control like looking of nonce and approval of square and how the agents need to treat that they will choose how much motivations to be given to witnesses, and they will likewise conclude the elements like square size, power, and an official choice will be made by partners to what in particular delegates will have proposed to them. Witnesses will change inside some time length or seven days. Witnesses ought to play out the exchange distributed inside the given time term. Everything revolves around the standing of witnesses; the more they play out the exchange effectively inside the given time length, the more will be their opportunities to get choice again in the mining system by selectors (i.e., cryptocurrency holders). DPoS is likewise expanding more decentralized design as what proposed in PoS was more in a concentrated manner to whom will have the higher measure of money will have the really overwhelming impact in the entire organization; however, in DPoS, it has been changed and made a framework something circulated that is eliminating the centralization interaction Zheng et al. (2017).
Advantage
1.) Simple and proficient: Significantly decrease the quantity of taking an interest check and bookkeeping hubs to accomplish a second-level consensus confirmation.
2.) Save resources & assets: just need the essential hub to confirm the organization.
3.) High scalability: second-level confirmation, quick block out, the solid limit of the principal organization.
Disadvantages: The whole consensus mechanism depends on tokens, and numerous business applications don't need tokens
1.) Centralization: reducing the number of confirmation hubs, not the widespread check hub, straying from the essential soul of everybody in the blockchain world, unnecessary centralization.
2.) Bribery makes the main network fail: the notable EoS pay-off the issue, the principal network vote can-not be finished, in addition to the super-hub pay off to make the EoS administration confounding.
Hybrid Consensus, Regression of the Pow Consensus
Albeit numerous public chains have their own one-of-a-kind plan theory, for the sake of security, they actually can't safeguard the POW consensus mechanism. For open and independent public-chain conditions, the POW consensus mechanism has better material-ness; while the POS consensus process has high administration costs, the POS consensus mechanism must be utilized in significant dynamic cycles, for example, algorithm changes and fork determination. Its utilization esteem, however this is as of now a moderately focal dynamic mechanism.
The accompanying table sums up the current consensus mechanisms for the use of different public chain projects Table 3:
| Table 3 Hybrid Consensus, Regression of the Pow Consensus | ||
| Sr. No. | Public chain project | Consensus mechanism |
| 1. | Bytom | PoW: Artificial Intelligence & Computerized reasoning ASIC Chip-Friendly POW Consensus Mechanism |
| 2. | Aeternity | PoW + PoS: The PoW mechanism produces blocks, and major decisions of significant choices are made by the PoS mechanism, giving the tokenish holders the freedoms. |
| 3. | Aelf | PoW + PoS: The principal chain takes on the PoS consensus mechanism, and the side chain embraces the PoW consensus mechanism. PoS the board costs are high, so it is appropriate for the fundamental chain, and the side chain utilizes PoS to work securely and independently. |
| 4. | Zilliqa | PoW + PBFT: The security of the PoW consensus mechanism is utilized to confirm the hubs, and the checked hubs are given over to the PBFT consensus mechanism for navigation |
Advantages and Disadvantages of the Four Major Consensus
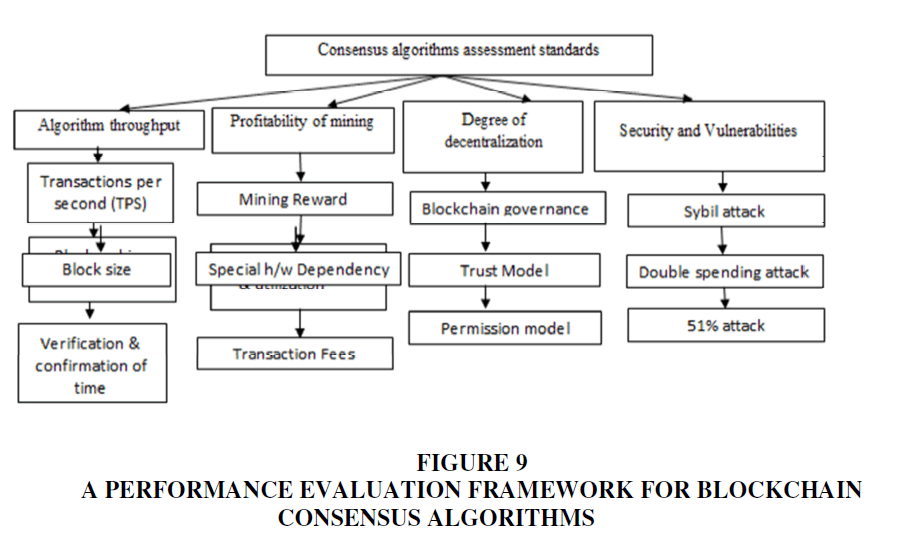
We analyze the consensus algorithms of the blockchain normal chain and the permit chain, and look at the benefits and impediments of every algorithm from asset utilization, centralization degree, throughput, and exchange affirmation time Table 4.
| Table 4 Advantages and Disadvantages of Each Algorithm | ||
| Consensus protocols | Advantage | Disadvantages |
| PoW | 1. Protected and steady, a serious level of opportunity of hubs. 2. Serious level of decentralization, open hub system. |
1.Weak scalability & adaptability and low performance & execution 2.Causing hardware equipment waste & squander. |
| PoS | 1.Less energy 2. Serious level of decentralization, open hub system. |
1.Complex implementation & execution process 2.Security breach, |
| DPoS | 1.Less energy 2.High performance & Elite execution. 3.Finality & Conclusiveness |
1. weak degree & feeble level of decentralization shut nodes framework |
| PBFT | 1.Higher performance & Better execution. 2. Finality & Conclusiveness 3.High security |
1.Weak degree & Frail level of decentralization, shut node framework 2.Low adaptation to non-critical failure |
Other Consensus Mechanisms
Different other consensus mechanisms are utilized in various cryptographic forms of money. One of the critical mechanisms is Proof of Correctness which is utilized in Ripple 56. Chase & MacBrough (2018). Here the servers gather the unsubstantiated exchanges and unveil them as up-and-comer sets. Those competitor sets are casted a ballot by all servers in view of their veracity. The applicant sets, which surpass a foreordained limit vote count, will continue to the following round. The interaction proceeds until a set gets essentially 80% votes of the servers and afterward that set is added to the record. Proof of Authority 57. Tedeschi et al. (2019) is utilized in Ethereum's Network. It is like the PoS mechanism. Be that as it may, the chance of turning into a validator relies upon the standing of a competitor, not how much stake. Proof of Believability is a consensus mechanism that is utilized by IoS Token. Here, the validators are chosen by their past conduct and commitment record. The expected information is dispersed to the hubs utilizing a decency algorithm Table 5.
| Table 5 Comparison other Consensus Models | |||||
| Testing Base | PoW | PoET | PoS | Federated BFT | BFT & Variants |
| Trust Model | Untrusty | Untrusty | Untrusty | Semi-trusted | Semi-trusted |
| Transaction Finality | Probabilistic | Probabilistic | Probabilistic | Instantaneous | Instantaneous |
| Transaction rate | Slow | Medium | Rapid | Rapid | Rapid |
| Cost of Participation | Present | Absent | Present | Absent | Absent |
| Scalability | Large | Large | Large | Large | Low |
| Token requirement | Yes | No | Yes | No | Yes |
| Type of Blockchain | Permissionless | Both | Both | Permissionless | Permissionless |
Comparison of Consensus Algorithms
To agree in a blockchain network is a perplexing and significant errand that is characterized as a consensus issue and has wide applications truly including dispersed registering, load adjusting, and exchange approval in blockchains. Over ongoing years, many investigations have been done to adapt to this issue. In this paper, a similar and insightful audit of the cutting edge blockchain consensus algorithms is introduced to edify the qualities and imperatives of every algorithm.
In view of their intrinsic details, every algorithm has an alternate area of relevance that respects propose a few exhibition rules for the assessment of these algorithms. To outline and give a premise of correlation with additional work in the field, a bunch of incommensurables and clashing execution assessment standards is recognized and weighted by the pairwise examination technique Table 6.
| Table 6 Comparison of Permissioned Network Consensus Algorithms | ||||
| BFT | RBFT | PBFT | PAXOS | RAFT |
| Closed network | Closed network | Synchronous | Synchronous | Synchronous |
| Used for business working based in view of savvy contracts, and light of shrewd agreements | Used for business working based in view of savvy contracts, and light of shrewd agreements | Smart contract-subordinate | Smart contract-subordinate | Smart contract-subordinate |
| State machine replication is utilized | The legitimate specialists are dealing with appropriate work. | State machine replication is utilized. | Sender, proposer, and acceptor mutually work | Collecting record on some agreement & consent to work. |
| Good conditional and transactional throughput | Good conditional, value-based & transactional throughput | Greater conditional, value-based & transactional throughput | Greater conditional, value-based & transactional throughput | Greater conditional, value-based & transactional throughput |
| Based on traditional, customary and conventional thoughts. | Based on traditional, customary and conventional thoughts. | It can bear f-1 acceptance & resistance | PAXOS can bear f/2-1 deficiencies | RAFT can bear f/2-1 shortcomings |
These standards are characterized into four classes including algorithms' throughput, the productivity of mining, level of decentralization, and consensus algorithms weaknesses and security issues Table 7.
| Table 7 Comparison of Permissionless Network Consensus Algorithms | |||
| Proof of Work (PoW) | Proof of Stake (PoS) | Proof of Burn (PoB) | PoET |
| Utilized for ventures working on monetary level | Used for enterprises working on monetary level | Used for businesses working on monetary level | Used for industries dealing with a monetary level |
| Utilizing public-key encryption (i.e., Bitcoin) | Using RSA algorithm for encryption | RSA algorithm for encryption | RSA algorithm for encryption |
| Power inefficient | Power inefficient | Power inefficient | Power inefficient |
| Open environment | Open environment | Open environment | Open environment |
| Bitcoin script is used | Mostly, Go long is used | Mostly, Go long is used | …………….. |
Applications Area
In the new, blockchain-based application isn't just restricted monetary area, however have filled in bookkeeping, casting a ballot, energy supply, quality confirmation, self-sovereign, character (KYC), medical care, coordinated operations, agribusiness and food, law implementation, modern information space, advanced recognizable pieces of proof, and validations, gaming, and betting government, and hierarchical administration, work market, market estimating, media, and content appropriation, network foundation, generosity straightforwardness, and local area administrations, genuine state notoriety check and positioning ride, sharing assistance, interpersonal organization, production network accreditation in the food business. Blockchain generally disapproves of versatility and security, which should be handled Tables 8 & 9.
| Table 8 Comparison Based on Characteristics | |||
| Characteristics | PoW | PoS | PoB |
| Trusted Model | Un-trusted | Un-trusted | Un-trusted |
| Blockchain Type | Permission less | Both | Both |
| Transaction Finality | Probabilistic | Probabilistic | Probabilistic |
| Degree of Decentralization | High | High | High |
| Scalability | High | High | High |
| Compliance to Distributed Consensus Properties | Probabilistic | Probabilistic | Probabilistic |
| Reward | Yes | Yes | Yes |
| Table 9 Comparison Based on Performance | |||
| Performance Attributes | PoW | PoS | PoB |
| Crash fault tolerance | 50% | 50% | 50% |
| Response Time | 10 Minutes | 1 Minute | 1 Minute |
| Rate of Energy consumption | High | Better than PoW | Better than PoW |
| Transaction Throughput | Very Low | Low | Low |
| Transaction Latency | Very High | High | High |
Technical Challenges
Blockchain innovation execution has issues like versatility, block size, number of exchanges each second. It may not matter to high-recurrence exchanges. The compromise between block size and security prompts an egotistical mining system. Excavators can conceal their dug block for more income later on. There is an opportunity of protection spillage in any event, when clients just make exchanges with their public key and the private key. Clients' genuine IP locations could be followed and the quantity of squares is mined per unit time can't satisfy the prerequisite of the course of millions of exchanges in an ongoing manner. What will the greatest chain length and the most extreme number of diggers be an inquiry? Is there any likelihood to go for an incorporated framework utilizing blockchain? A bigger square size could dial back the spread speed and loan blockchain branch is difficult for some applications. There is plausible of little exchanges can be postponed because of excavators giving more execution to a high exchange charge specialized. As blockchain is an impending innovation, it faces a few difficulties.
1. Space:
One of the significant difficulties looked by blockchain is the absence of room. The chain continues to develop and consequently requires an ever-increasing number of assets and influences execution adversely. Because of millions of exchanges requiring consideration, the blockchain turns out to be weighty. It is important to store all past exchanges to approve the new ones which expands the requirement for a greater limit. This makes another issue excavators favour exchanges with a greater expense, which brings about a postponement in the little exchanges. A couple of the proposed arrangements are as per the following.
a. Capacity improvement should be possible by erasing more established information which liberates the hubs from holding every single past exchange.
b. The blockchain could be updated where the square is isolated into two areas one to hold the exchanges and the other for the diggers to contend to turn into the pioneer who creates the miniature blocks.
2. Security:
There are different weaknesses and we can say that the vulnerabilities found in the protocol.
a. Miner selfishness: There are different weaknesses found larger part (51%) of the diggers could influence the blockchain and even change the exchanges that have happened. This represents a genuine danger to the security of the clients and the blockchain. Late analysts have observed that even without the larger part, the excavators could genuinely influence the blockchain.
b. Double spend attack: Since it requires an exchange of a specific profundity before it very well may be affirmed, which can require 2040 minutes by and large, it is feasible for vindictive clients to spend a similar coin once more. This should likewise be possible with the assistance of a digger. Consequently, it represents a genuine danger to the exchanges
3. Coin loss:
As the cryptocurrency is just present in web-based wallets, it is conceivable that a client fails to remember the secret key of their record after some time which prompts the deficiency of those coins as there is no technique to work with such coins.
4. Privacy:
A significant element of all cryptographic forms of money is that all exchanges are straightforward. As the data is accessible to people in general, it has been observed that it very well may be utilized to arrive at the clients associated with the exchange. Every client can be distinguished through the hubs it associates with and this data could be utilized to track down the start of an exchange. This abuses the security of the client which was guaranteed through the namelessness of the client. There is a strategy accessible to connect the client's pen name their IP address regardless of whether they use firewalls. This is a break of the security of the client. A couple of proposed techniques to handle this are as per the following.
a. Mixing/blending: This alludes to performing exchanges through numerous info and result addresses. This would make it hard to track down a connection between the two members. Mediators could be involved to guarantee significantly more protection. In any case, assuming that the mediator hub is self-centred, it could uncover the members' data or even remain quiet about the cash. A simple arrangement is encoding the information so the burglary could be recognized.
b. Anonymous: This alludes to the possibility of totally unknown exchanges where the diggers don't have any data about the exchange and the client data is encoded.
c. Off chain: Sensitive information are not put away on the blockchain and must be gotten to simply by approved work force. This additionally takes care of the issue of room as a portion of the data is put away in an alternate area.
Therefore, in this manner, because of an increment in protection and secrecy, digital currencies could be utilized in illegal exercises which is one more danger to the innovation Narayanan (2016); Miglani et al. (2020).
Sustainability
There are various ways the way in which maintainability can be characterized in a framework setting. Maintainability straightforwardly relies upon the setting of interest, be it biological, monetary, monetary, social, political or institutional and is additionally perceived as something with a direct conduct sway on the arrangement of interest. The normally utilized three mainstays of maintainability are centred around the climate, economy and society as the limits of this perplexing theme. Further, more the manageability data absolutely relies upon these three points of support as well as their noteworthy foundation.
Contingent upon the perspective, cryptocurrency environments can be considered data innovation helped financial or money related frameworks. This large number of perspectives are important for this situation, and with the immediate effect on the climate through energy utilization, the three mainstays of maintainability - economy, climate, and society - give off an impression of being material and will along these lines be applied to the current point. Notwithstanding the three mainstays of maintainability, data innovation will likewise be thought of as because of the undeniable reliance of cryptographic forms of money on the basic equipment and programming, all the more explicitly blockchain innovation. Contingent upon the focal point of interest, these four regions might show separating qualities, which is the reason an appropriate definition for this work will be characterized as follows:
The maintainability of cryptographic forms of money is vigorously impacted by its adaptability, security, influence utilization, and long-haul administration as well as the motivations and expenses of partaking in the consensus protocol.
The adaptability can additionally be parted into exchanges each second and the quantity of taking an interest hub, while the security angle comprises of adaptation to internal failure and exchange irrevocability. The economy of participating in the consensus mechanism contains block prizes and exchange charge compensations in contrast with mining or approving equipment gear and energy costs related with the activity
Consensus Algorithms Evaluation Criteria
With the broad and escalated development of blockchain innovation and its application in various areas, an assortment of intricate consensus algorithms are created which have novel, yet different properties and applications. The fundamental reason for this paper is to observe the main rules which would influence the presentation of these algorithms. With an extensive audit of the writing, we recognized an assorted arrangement of standards that have been applied to the various circumstances as introduced in Table 10. To decide the main measures among the rules sets, the matched correlation network strategy is applied. The pairwise correlation technique is perhaps the most widely recognized strategy to decide the significance or weight of every model. In this technique, the rules are contrasted and one another. This examination is done base on deciding the worth of every standard's inclination over different ones as displayed in Tables 10 & 11. The worth of this inclination is shaped by the progressive dynamic technique and the pairwise correlation strategy.
| Table 10 Summary of Different Sets of Performance Evaluation Criteria Used in Blockchain Consensus Literature | ||
| Authors | Year & Reference | Performance evaluation criteria |
| Croman | Croman et al. (2016) | 1- Maximum throughput, 2- Latency, 3-Bootstrap time, 4-Cost per Confirmed Transaction, 5-Transaction validation & approval 6-Bandwidth, 7-Storage |
| Baliga, Arati | 2017 | 1-Transaction finality, 2-Transaction rate, 3-Token required, 4-Cost of participation & investment, 5-Scalability of the companion organization, 6-Trust model, 7-Adversary Tolerance |
| Mingxiao | Mingxiaoet al.(2017a); Mingxiaoet al. (2017b) | 1-Byzantine fault tolerance, 2-Crash fault tolerance & adaption to non-critical failure, 3-Verification speed, 4- Throughput (TPS), 5-Scalability |
| B. Xu, Luthra, Cole, & Blakely | Xu et al. (2018) | 1-Architecture (Accounts, Transactions, and Contracts, State Management, Execution Environment), 2-Fault tolerance & resistance, 3- Economic Systems Analysis, 4- Block Size, 5-Block Time, 6-Transactional Throughput, 7-Block Throughput, 8- CPU Usage, 9-Transaction Size |
| Nguyen and Kim | Nguyen & Kim et al. (2018) | 1-Energy efficiency & productivity, 2-Modern equipment, 3-Forking, 4-Double spending attack, 5-Block making speed, 6-Pool mining |
| Wang | Wang et al. (2019a); Wang et al. (2018); Wang et al. (2019b) | 1-Origin of Hardness, 2-Implementation portrayal, 3-ZKP Properties, 4- Simulation of arbitrary function & capacity, 5-Features of puzzle design, 6-Virtual mining, 7- Simulating Leader election |
| Tang, Shi, & Dong | Tang, Shi, & Dong et al. (2019) | 1-Basic innovation of technology, 2-Applicability, 3-TPS, 4-Market capitalization, 5-Number of forks, 6-Total commits in GitHub, 7-Ranking in GitHub, 8-Team action |
| Alsunaidi & Alhaidari | Alsunaidi & Alhaidari (2019) | 1-Node Identity management, 2-Data Model, 3-Electing excavators' technique & method, 4- Energy saving, 5-Tolerated power of the adversary & force of the foe, 6-Transaction expenses, 7-Block reward, 8-Verification speed, 9-Throughput, 10-Block making speed, 11- Scalability, 12-Extendible 13-51% Attack, 14-Double Spending, 15-Crash Fault Tolerance, 16- Byzantine fault tolerance (BFT) &adaptation to non-critical failure. |
| Hasanova, Baek, Shin, Cho, & Kim | Hasanova et al. (2019) | 1-Double spending attack, 2-51% attack, 3-Private key security, 4-Noting at stake, 5-criminal issues, 6-selfish mining (self-centred mining), 7-block keeping, 8-Bribery attack, 9-DDos/DoS, 10-Sybil attack, 11-Routing attack, 12-Time jacking attack |
| Bano | Bano et al. 2017(a); Bano et al. 2017(b), Bano et al. 2019 | 1-Committee design & configuration, 2-Transaction censorship resistance & oversight opposition, 3-DoS obstruction & resistance, 4-Adversary model, 5-Throughput, 6-Scalable, 7-Latency, 8- Experimental arrangement & setup. |
| Table 11 The Pairwise Comparison Scales Among Two Criteria | |
| Types of preferences | Assigned value |
| Equal Importance | 1 |
| Weak Importance | 2 |
| Moderate importance | 3 |
| Moderate plus | 4 |
| Strong importance | 5 |
| Strong plus | 6 |
| Very strong | 7 |
| Very, very strong | 8 |
| Extreme importance | 9 |
To decide the significance of the distinguished rules, a survey is planned and given to eight specialists in this field. The consequences of these eight polls are consolidated by mathematical mean to frame a last pairwise correlation grid as introduced in Table 1. The heaviness of distinguished standards is considered as the mathematical mean of every one of the columns in the standardized pairwise examination network. At long last, the consistency of the pairwise examination not entirely settled by ascertaining the incongruence rate that was under 0.1. The acquired outcomes are given in Table 4 and the model a worth upper than 0.04 is considered as the main measurement for assessing the presentation of the blockchain consensus algorithm.
In this part, we will truly do advance examination of these models and foster a system to assess the consensus algorithms' exhibition in view of the algorithm's throughput, benefit of mining, level of decentralization, and consensus algorithms weaknesses as displayed in Figure 9. In the accompanying, we would present the fundamental models and their sub-classes that are presented as a system for consensus algorithms execution assessment.
Comparative Analysis of Consensus Algorithms in the Blockchain
This part examines the boundaries pertinent in assessing the consensus algorithms in the blockchain. Blockchain type, exchange rate, versatility, foe resilience model, exploratory arrangement, idleness, throughput, transmission capacity, correspondence model, correspondence intricacy, assaults, energy utilization, mining, consensus class, and consensus certainty are recognized as a basic boundary for looking at the different consensus algorithms for blockchain. Near investigation of a few as of late proposed algorithms: ELASTICO 73.
Luu, et al. (2016), pioneer free Byzantine consensus Crain et al. (2017), certain consensus and blockchain with unbounded throughput Ren (2017), Proof of Trust (PoT) Zou et al. (2018), DBFT consensus Jeon (2018), PoPF Fu (2018), Ripple. Schwartz (2014), Proof of Vote Li, et al. (2017), and Proof of work Nakamoto, S., & Bitcoin (2008) is performed. The similar perspective on the consensus algorithms is introduced in table I-III. The recognized boundaries and examination of the consensus algorithms concerning them are introduced as under.
Block chain Type
There are three sorts of blockchain, public, private, and consortium Khatwani, (2018). The kind of blockchain characterizes the enrolment control in the consensus algorithm. This must be considered while assessing the consensus algorithms to check what sort of participation is accepted in the plan. The kind of blockchain ought to be picked by the idea of the business application.
Scalability/Adaptability/Versatility
Versatility is a centre necessity to manage large information in the present climate. Versatility is accomplished if expanding the quantity of hubs brings about more exchange blocks being handled. Proof of trust and ELASTICO are adaptable. Certain consensus and PoW are not versatile arrangements. Different algorithms associated with examinations are not tried concerning their adaptability yet.
Adversary Tolerance Model and Foe Resistance Model
The enemy model controls the small portion of blockchain networks that can endure disappointment or assault without influencing consensus. The algorithm proposed for consensus in blockchain accompany a limit an incentive for this foe model. A higher incentive for the enemy limit is better. ELASTICO has the best enemy command over the other algorithms.
Performance-Related Parameters and Execution Related Boundaries
A portion of the current consensus algorithms are not tentatively assessed. They are just thought about hypothetically utilizing rightness proofs. Notwithstanding, alongside this, there is a need to have a quantitative examination set up that audits the exhibition and security of these consensus algorithms. Inactivity, throughput, and data transfer capacity are the three center exhibition angles that should be centered around for every one of the consensus algorithms. Aside from ELASTICO, different algorithms are not tentatively assessed concerning these exhibition viewpoints.
Communication Model and Complexity and Correspondence Model and Intricacy
In simultaneous correspondence, the shipper trusts that the beneficiary will recognize the solicitation. In offbeat correspondence, the shipper doesn't have to sit tight for the reaction from the beneficiary and proceed with the correspondence. For constant applications that can't manage the cost of deferrals, PoW, PoT, Ripple, and understood consensus can be thought of. In the event that there are more perused activities expected in an application, a simultaneous model should be picked as it gives prompt reaction. ELASTICO and pioneer free consensus algorithm Crain et al. (2017) has a nonconcurrent correspondence model accepted in consensus algorithm plan. Pioneer free consensus algorithm Crain et al. (2017) has a direct and preferred expense of correspondence over ELASTICO and PoT. The correspondence cost of the other algorithms isn't examined at this point in the writing.
Attacks
Swell is inclined to a Sybil assault in which a solitary assailant controls various organization hubs by making different IP addresses, virtual machines, and client accounts. Pioneer free consensus, PoT is secure against this assault. The algorithms are not assessed and investigated concerning the quantity of safety assaults conceivable in a blockchain network. It is essential to audit the algorithms concerning security assaults.
Energy Consumption & Utilization
Energy utilization characterizes how much energy or power that the equipment framework consumes in the blockchain network. The energy utilization of practically all of the consensus algorithms isn't tentatively assessed.
Mining and Consensus Class & Category
It characterizes how the most common way of mining is completed in the blockchain network. It is firmly connected with how the confirmation interaction happens. Proof-based consensus is great for networks with countless hubs. Vote-based consensus, then again, works best with a set number of hubs. In the event that the organization has countless hubs, it is desirable over use ELASTICO, PoW, PoPF, and understood consensus. For another situation, the remainder of the consensus protocols (associated with correlation) would fit best.
Consensus Finality
Conclusion in blockchain shows that the exchange is finished and won't be returned. It is a significant angle to consider while planning a consensus protocol for blockchain. Probabilistic certainty and outright absolution are the two classifications of consensus conclusion. In probabilistic certainty, as the square gets further into the chain the opportunity of its returning declines. Be that as it may, in outright conclusiveness, an exchange is promptly settled after its consideration in the blockchain. In the event that outright consensus conclusiveness is to be accomplished, ELASTICO, PoPF, and implied consensus are recommendable variations in consensus. In outline, a few elements exist to assess a consensus algorithm concerning its working, execution, and security-related angles.
Related Work
We led a casual writing audit utilizing the inquiry string ("Blockchain" OR "DLT" OR "Conveyed Ledger") AND ("Energy Consumption" OR "Energy Demand" OR "Power Demand" OR "Carbon Footprint") on the Bielefeld Academic Search Engine (BASE). We in this manner acquired many aftereffects of different earlier work on examining the energy interest of various DLT frameworks, with a critical spotlight on PoW blockchains overall and explicitly Bitcoin. Ordinarily, models take one of the accompanying two structures.
Experimental Models
The primary structure spins around leading analyses utilizing mining equipment and estimating its genuine energy utilization, as currently done, with various setups of computational assets Igumenov et al. (2019). This approach has been utilized to determine utilization attributes for various use situations. The "BCTMark" structure Saingre et al. (2020), for example, takes into account the organization of a whole investigation stack, including the DLT framework under test. Utilizing load generators, a sensible organization responsibility can be made. The consequences for the energy utilization of this arrangement under changing burdens can hence be estimated through energy sensors associated with the testbed. A test review on the energy utilization of the non-PoW XRP record exhibits that redoing validator equipment can yield decreases in energy request Roma & Hasan (2020). Measurements detailed for normal digital forms of money have been joined with testbed analyses to display the energy utilization practices of different consensus algorithms Cole & Cheng (2018).
Mathematical Models
An elective strategy is to measure suppositions about the climate in which a DLT framework works. Regularly, such models utilize a "hierarchical" approach that depends on openly discernible elements -, for example, hash rate on account of Bitcoin - and partners them with normal mining equipment or even look to decide the equipment utilized through overviews Lei et al. (2020); Lei et al. (2021). Gallersdörfer (2020); Küfeoglu & Özkuran (2019); Zade, (2019) are instances of this hash rate-based methodology. attempt a fundamental correlation of various DLT structures with the end that the energy utilization varies essentially relying upon the plan picked Sedlmeir et al. (2020). A further report refines past models for Bitcoin's power utilization, for example, the one by Vranken (2017), and underlines that the main thrusts behind power utilization are the Bitcoin cost and the accessibility of modest power. The utilization of a straight relapse model to anticipate Ethereum's energy utilization in view of the noticed hash rate and trouble level 93.
Eshani, et al. (2021); notwithstanding, the utilization of short-sighted interjection strategies alone is probable not a proper technique for PoW blockchains Lei et al. (2020); Lei et al. (2021). Though inferred numerical model for the energy utilization of the PoS-based Polkadot blockchain by extrapolating from the power interest of a solitary validator machine Powell et al. (2021).
Comparative Analysis
This Section presents a correlation of the different consensus algorithms that we have talked about such a long way in this paper. Table 8, Table 9 above and Table 12 beneath present a point-by-point correlation between the previously mentioned consensus algorithms as far as qualities and execution.
| Table 12 Comparative Analysis of Consensus Mechanisms | ||||||
| Sr. No | Consensus Mechanisms | PoW | PoS | Hybrid PoW & PoS |
BFT | Tangle |
| 1. | Energy Consumption | Waste considerable energy | Less energy consumption | Uses a significant amount of energy | Less energy consumption | Uses a significant amount of energy |
| 2. | Advanced H/W Requirement | Required | Not Required | Differ in various mechanisms | Not Required | Required, however at that point of PoW |
| 3. | Centralization | Decentralized | Partially centralized | Partially centralized | Centralized | Decentralized |
| 4. | Double Spending Attack | Theoretically Possible | Difficult | Possible, yet less genuine than PoW | Not Applicable | Difficult |
| 5. | Versatility & Scalable Memory Requirements | Not scalable, because of public record | scalable, because of public record. | Partially Scalable vary in various Mechanisms | Scale less then PoW or PoS | Scale less then PoW or PoS |
| 6. | Security | Attack is conceivable with 51% hash power, which is unfeasible in the real world | Removes 51% of attack threat | Remove 51% of attack threat | May have a solitary mark of Failure | N/w can be assaulted with 234% hash power |
Applying a suitable consensus mechanism is vital for a cryptocurrency. The confirmation interaction, the security of the organization, approval time, and the expense of handling all rely upon the consensus mechanism. Apparently cryptographic forms of money put the best accentuation on security and decentralization. Thus, most of digital currencies utilize Proof of Work as a consensus protocol. Due to its approval interaction, the following most well-known consensus mechanism is Proof of Stake. In spite of the fact that there are numerous consensus algorithms, most of digital forms of money utilize these two strategies. In view of their strategies and attributes, different consensus mechanisms can be partitioned into five significant gatherings: Proof of Work; Proof of Stake; a cross breed or mix of both PoW and PoS; Byzantine Fault Tolerance with various forms; and Tangle. Proof of Work, which is a laid out decentralized and secure protocol, requires a lot of computational energy to make a square. Additionally, all digital forms of money that follow the PoW algorithm are confronting adaptability issues. As an answer, PoS became possibly the most important factor with a more straightforward approval process and with lower energy utilization. Nonetheless, the PoS mechanism faces centralization issues. It is expected that a couple of financial backers later on will control cryptographic forms of money under the PoS mechanism. Therefore, the crossover or consolidated mechanisms of PoW and PoS were made. These, half and half mechanisms contrast from each other. The PoW stresses the decentralization and security of the organization while the PoS accentuates adaptability and energy utilization. Accordingly, the consolidated mechanisms comprise of both the advantages and disadvantages of the PoW and PoS. Be that as it may, the two mechanisms face stockpiling issues since, because of centralization, all companions need to save the consistent public record. The Byzantine Fault Tolerance related mechanism addresses a large portion of the disadvantages of both the PoS and PoW. Nonetheless, it is unified. As an outcome, this mechanism is for the most part utilized in private or permissioned Blockchains rather than in a public Blockchain. The significant contrast among Tangle and different mechanisms is that Tangle doesn't utilize a Blockchain organization yet utilizes DAG to develop the organization. In this way, the approval interaction in Tangle is unique in relation to other people.
Discussion
Interpretations
These outcomes can essentially be perceived as an unmistakable affirmation of the normal assessment that the energy utilization of PoW frameworks, particularly Bitcoin, is unreasonable. Hence, they can be deciphered as a solid contention for the modernization of PoW-based frameworks towards PoS. Ethereum is taking an estimable lead in this regard with the improvement of Ethereum 2.0. Moreover, the outcomes demonstrate that the energy utilization of various non-PoW blockchains is shockingly disparate (e.g., by a component of around 1 × 103 between the PoS framework with the most noteworthy utilization and the one with the least). In outright terms, nonetheless, the utilization paces of PoS-based frameworks are moderate and hence a lot nearer to the figures for conventional, incorporated instalment frameworks like Visa Net.
The fundamental justification for why our model yields extensive difference between PoS frameworks is the different number of validators. In particular, in permissioned frameworks, energy utilization can be controlled through the capacity to restrict the quantity of validators on an organization, so the permissioned network dissected in this study is portrayed by low energy utilization. Nonetheless, this perception doesn't warrant ends, for example, that authorization frameworks are essentially less energy destructive. Besides, while in permissioned frameworks an administrator can impact the quantity of hubs, it doesn't really imply that that number should be lower.
Regardless of whether a decreasing impact of per missioning on energy utilization could be expressed with assurance, this ought not be confused as a contention for expanded centralization or a contention for authorization networks over permissionless ones. This ends up being undeniable while considering a consent DLT framework in extremis: such a framework would comprise of just a solitary validator hub and would subsequently be actually incorporated. This speculative situation shows that, assuming an authorization worldview is applied, close consideration ought to be paid to framework section obstructions implemented through gatekeeping capacities. If not, there is a danger of centralization, which might offer benefits as far as energy utilization, yet will invalidate the utilitarian benefits of a decentralized worldview. Of down to earth significance is likewise the outcome that the determination of reasonable validator equipment is vital to energy utilization. Data in regards to sufficient equipment for validators is frequently conflicting. Thusly, normalized suggestions ought to be advanced to help administrators of validator hubs in choosing the most energy-effective equipment arrangement.
This study is just an initial move towards measuring the energy utilization of PoS frameworks. In any case, notwithstanding its restrictions, it gives impulse to originators of decentralized frameworks by uncovering the reliance between validator number, burden, and equipment setup. Our model can along these lines be utilized to decide the carbon impression of a specific use case. It can besides provoke administrators of validator hubs to painstakingly choose appropriate equipment.
Limitations
Up until this point, we have utilized expansive utilization reaches to display the energy utilization of individual validator hubs. While we are certain that the genuine energy utilization is truth be told inside these reaches, fundamental qualities of various PoS protocols that may affect energy utilization, for example, the bookkeeping model, have been overlooked. Second, while expecting that the power utilization of a validator hub is autonomous of framework throughput is very much defended for the permissionless frameworks investigated Buterin (2021), permissioned frameworks that are intended to help high throughput may not warrant such suspicion. While we have represented this by expecting all the more impressive equipment for permissionless hights frameworks, more work is expected to comprehend permissioned blockchains' energy utilization attributes better. Also, the effect of various jobs on energy utilization ought to be thought of; for instance, basic instalments exchanges might have lower computational prerequisites when contrasted with other brilliant agreement calls, yet up to this point, we have not recognized exchange types.
Further, while our model proposes that PoS frameworks can remain energy-proficient while increasing to Visa Net throughput levels, there is no hard proof on the side of this contention, as no DLT-based framework has encountered a supported volume of this greatness to date on the base level.
We overlooked the chance of accomplishing really higher throughput than the predefined most extreme through layer 2 (L2) arrangements, for example, the Lightning organization or by means of hopeful and zero-information (zk)- rollups that are getting expanding consideration.
At long last, despite the fact that there are motivations to help its credibility, the supposition that a relative capacity can be utilized to communicate the quantity of validators as far as throughput is sketchy. While we accept that it applies to Hedera, this probably won't be a reasonable presumption for other permissioned settings. The material-ness of this model to other permissioned frameworks ought to along these lines be all the more officially broke down.
Result
The averaged data found that the middle value of time-series information of exchange demand fulfilled proportion. The re-enactment results at the last time step are introduced in Table-3, Table-4 will show that the positive(convince) and negative(inconvenience) similarities for both of the algorithm (PoW & PoS), Table-5 will tell us Testing base criteria, and at last Table-8 & Table-9 will show the comparison in both PoW & PoS with checking the attributes based on characteristics and performance in which the qualities arrive at the midpoint across with characteristics & performance-based examples, and the standard deviations.
We can see that each subplot in the irregular and little world organizations is extremely similar. Moreover, in these two subplots, PoW and PoS have comparative exchange demand fulfilled proportion, while the PoS has the most elevated exchange effectiveness. This is on the grounds that both PoW and PoS won't reset the calculation influence or the coin equilibrium of the chosen excavator, while the PoS will exhaust the stake of chosen digger, prompting more modest abundance disparity. Specifically, PoW and PoS will quite often construct a positive, criticism between "huge likelihood of being chosen" and "better condition in excavator choice", and just a couple of diggers will be compensated with new coins under PoW and PoS. Then, at that point, a rich specialist needs to manage numerous somewhat more unfortunate specialists to satisfy his/her coin demand, prompting the low solicitation fulfilled proportion. Conversely, the digger under PoS will be probably not going to be chosen a few time steps later, prompting what is happening that more excavators will be compensated. Since the abundance imbalance is more modest under PoS, specialists are bound to exchange with one another in arbitrary and little world organizations.
Future Works
Consensus mechanisms are intended to focus on one or the other decentralization or effectiveness. It is trying to arrive at a choice in an absolutely appropriated framework contrasted with a concentrated framework, particularly when there are no monetary motivators. In Blockchain assuming that decentralization expands, effectiveness diminishes.
The consensus algorithm is the primary innovation of Blockchain, however continuous exploration of the consensus algorithms is as yet in its underlying stage. On the off chance that we attempt to build effectiveness, the organization some way or another becomes concentrated. In spite of the fact that apparently DAG settles both adaptability and decentralization, it brings a huge security danger.
Conclusion
The famous consensus algorithm of blockchain is summed up. By depicting its various prerequisites and conditions, the inward execution, benefits, and inconveniences of the four consensus algorithms of POW, POS, DPOS, and BPFT are explained. As of now, the POW-POS half breed consensus mechanism is the focal point of exploration. It is additionally another heading to utilize shrewd agreements to fabricate more straightforward consensus rules. The use of the consensus algorithm to rehearse is additionally a trial of the algorithm. The new assault strategy can cause us to comprehend the insufficiencies of the current consensus algorithm. Likewise, for consensus algorithms on the permit chain, pluggable switchable is a pattern. For various business situations, throughput necessities, and security suppositions, we can utilize different hidden consensus mechanisms to all the more likely serve high level applications.
Consensus mechanisms are examined by and large for a disseminated framework and explicitly for blockchain. We contrasted a few as of late proposed consensus algorithms and regard to various boundaries that altogether affect the consensus algorithm. The boundaries recognized for examination cover both security and execution perspectives. Aside from these, various different perspectives are additionally vital to be thought of.
We give broad information on consensus techniques utilized in cryptographic forms of money as well as in different regions like medical services, smart transportation frameworks, supply chains, banks, instruction, and different regions. The consensuses talked about connect with permissioned as well as permissionless, private, and public.
An exhaustive assessment uncovers that, disregarding versatility and energy utilization issues, PoW is the most well-known cryptocurrency mechanism. This implies that digital forms of money focus on decentralization over energy utilization. Mixture arrangements endeavour to defeat this issue by keeping up with decentralization. For future work, we intend to play out a near assessment for private and combined Blockchain organizations.
We have talked about the fundamentals of blockchain innovation, consensus algorithms, examination and investigation of significant consensus algorithms, and area of utilization in this paper.
References
Alsunaidi, S. J., & Alhaidari, F. A. (2019, April). A survey of consensus algorithms for blockchain technology. In 2019 International Conference on Computer and Information Sciences (ICCIS) (pp. 1-6). IEEE.
Antonopoulos, A.M. (2014). Mastering Bitcoin: unlocking digital cryptocurrencies. " O'Reilly Media, Inc.".
Indexed at, Google Scholar, Cross Ref
Bach, L. M., Mihaljevic, B., & Zagar, M. (2018, May). Comparative analysis of blockchain consensus algorithms. In 2018 41st International Convention on Information and Communication Technology, Electronics and Microelectronics (MIPRO) (pp. 1545-1550). IEEE.
Back, A., & Bentov, I. (2014). Note on fair coin toss via bitcoin. arXiv preprint arXiv:1402.3698. Indexed at, Google Scholar
Badertscher, C., Gaži, P., Kiayias, A., Russell, A., & Zikas, V. (2018, October). Ouroboros genesis: Composable proof-of-stake blockchains with dynamic availability. In Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security, 913-930.
Indexed at, Google Scholar, Cross Ref
Bano, S., Al-Bassam, M., & Danezis, G. (2017). The road to scalable blockchain designs. USENIX; login: magazine, 42(4), 31-36.
Bano, S., Sonnino, A., Al-Bassam, M., Azouvi, S., McCorry, P., Meiklejohn, S., & Danezis, G. (2017). Consensus in the age of blockchains. arXiv preprint arXiv:1711.03936.
Bano, S., Sonnino, A., Al-Bassam, M., Azouvi, S., McCorry, P., Meiklejohn, S., & Danezis, G. (2019). SoK: Consensus in the age of blockchains. In Proceedings of the 1st ACM Conference on Advances in Financial Technologies ,183-198.
Bayer, D., Haber, S., & Stornetta, W. S. (1993). Improving the efficiency and reliability of digital time-stamping. In Sequences Ii (pp. 329-334). Springer, New York, NY.
Bentov, I., Gabizon, A., & Mizrahi, A. (2016, February). Cryptocurrencies without proof of work. In International conference on financial cryptography and data security (pp. 142-157). Springer, Berlin, Heidelberg.
Buterin, V. (2021). Why sharding is great: demystifying the technical properties. Vitalik. ca.
Castro, M., & Liskov, B. (1999). Practical byzantine fault tolerance. In OSDI (Vol. 99, No. 1999, pp. 173-186).
Castro, M., & Liskov, B. (2002). Practical Byzantine fault tolerance and proactive recovery. ACM Transactions on Computer Systems (TOCS), 20(4), 398-461.
Indexed at, Google Scholar, Cross Ref
Chang, S. E., Luo, H. L., & Chen, Y. (2019). Blockchain-enabled trade finance innovation: A potential paradigm shift on using letter of credit. Sustainability, 12(1), 188.
Indexed at, Google Scholar, Cross Ref
Chase, B., & MacBrough, E. (2018). Analysis of the XRP ledger consensus protocol. arXiv preprint arXiv:1802.07242.
Cole, R., & Cheng, L. (2018, July). Modeling the energy consumption of blockchain consensus algorithms. In 2018 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData) (pp. 1691-1696). IEEE.
Correia, M., Veronese, G. S., & Lung, L. C. (2010, March). Asynchronous Byzantine consensus with 2f+ 1 processes. In Proceedings of the 2010 ACM symposium on applied computing (pp. 475-480).
Crain, T., Gramoli, V., Larrea, M., & Raynal, M. (2017). DBFT: Efficient byzantine consensus with a weak coordinator and its application to consortium blockchains. arXiv preprint arXiv:1702.03068.
Indexed at, Google Scholar, Cross Ref
Croman, K., Decker, C., Eyal, I., Gencer, A. E., Juels, A., Kosba, A., ... & Wattenhofer, R. (2016, February). On scaling decentralized blockchains. In International conference on financial cryptography and data security, 106-125. Springer, Berlin, Heidelberg.
Dai, H. N., Zheng, Z., & Zhang, Y. (2019). Blockchain for Internet of Things: A survey. IEEE Internet of Things Journal, 6(5), 8076-8094.
Dolenc, D., Turk, J., & Pustišek, M. (2020, July). Distributed Ledger Technologies for IoT and Business DApps. In 2020 International Conference on Broadband Communications for Next Generation Networks and Multimedia Applications (CoBCom) (pp. 1-8). IEEE.
Edgington, D. W., & Hayter, R. (2000). Foreign direct investment and the flying geese model: Japanese electronics firms in Asia-Pacific. Environment and Planning A, 32(2), 281-304. Google Scholar
Enescu, F. M., Bizon, N., Onu, A., Răboacă, M. S., Thounthong, P., Mazare, A. G., & Șerban, G. (2020). Implementing blockchain technology in irrigation systems that integrate photovoltaic energy generation systems. Sustainability, 12(4), 1540.
Eshani, G., Rajdeep, D., Shubhankar, R., & Baisakhi, D. (2021). An Analysis of Energy Consumption of Blockchain Mining and Techniques to Overcome It. In Proceedings of International Conference on Computational Intelligence, Data Science and Cloud Computing (pp. 783-792). Springer, Singapore.
Fadeyi, O., Krejcar, O., Maresova, P., Kuca, K., Brida, P., & Selamat, A. (2020). Opinions on sustainability of smart cities in the context of energy challenges posed by cryptocurrency mining. Sustainability, 12(1), 169.
Indexed at, Google Scholar, Cross Ref
Fu, X., Wang, H., Shi, P., & Mi, H. (2018, March). Popf: A consensus algorithm for jcledger. In 2018 IEEE Symposium on Service-Oriented System Engineering (SOSE) (pp. 204-209). IEEE.
Gallersdörfer, U., Klaaßen, L., & Stoll, C. (2020). Energy consumption of cryptocurrencies beyond bitcoin. Joule, 4(9), 1843-1846.
Gilad, Y., Hemo, R., Micali, S., Vlachos, G., & Zeldovich, N. (2017,). Algorand: Scaling byzantine agreements for cryptocurrencies. In Proceedings of the 26th symposium on operating systems principles, 51-68.
Haber, S., & Stornetta, W. S. (1990, August). How to time-stamp a digital document. In Conference on the Theory and Application of Cryptography (pp. 437-455). Springer, Berlin, Heidelberg.
Han, X., & Liu, Y. (2017). Research on the consensus mechanisms of blockchain technology. Netinfo Security, 5(9), 147-152.
Hasanova, H., Baek, U. J., Shin, M. G., Cho, K., & Kim, M. S. (2019). A survey on blockchain cybersecurity vulnerabilities and possible countermeasures. International Journal of Network Management, 29(2), e2060.
Indexed at, Google Scholar, Cross Ref
Houy, N. (2014). The economics of Bitcoin transaction fees. GATE WP, 1407.
Huh, J. H., & Kim, S. K. (2019). The blockchain consensus algorithm for viable management of new and renewable energies. Sustainability, 11(11), 3184.
Igumenov, A., Filatovas, E., & Paulavičius, R. (2019). Experimental investigation of energy consumption for cryptocurrency mining. In 11th international workshop on data analysis methods for software systems (DAMSS 2019), Druskininkai, Lithuania, 2019. Vilnius University Press.
Jaag, C., & Bach, C. (2017). Blockchain technology and cryptocurrencies: Opportunities for postal financial services. In The changing postal and delivery sector (pp. 205-221). Springer, Cham.
Indexed at, Google Scholar, Cross Ref
Jeon, S., Doh, I., & Chae, K. (2018, January). RMBC: Randomized mesh blockchain using DBFT consensus algorithm. In 2018 International Conference on Information Networking (ICOIN) (pp. 712-717). IEEE.
Khatwani, S. (2018). Different Types Of Blockchains In The Market and Why We Need Them. Dostupno na: https://coinsutra. com/different-types-blockchains/(13.3. 2019.).
King, S., & Nadal, S. (2012). Ppcoin: Peer-to-peer crypto-currency with proof-of-stake. self-published 19(1).
Küfeoglu, S., & Özkuran, M. (2019). Energy consumption of Bitcoin mining.
Kusmierz, B. (2017). The first glance at the simulation of the Tangle: discrete model. IOTA Found. WhitePaper, 1-10.
L. Goodman, Tezos. (2021).https://cryptorating.eu/whitepapers/Tezos/position_paper.pdf
L.Hedera Hashgraph, (2021). https://hedera.com/learning/what-is-gossip-about-gossip
Lamport, L. (2001). Paxos made simple. ACM Sigact News, 32(4), 18-25.
Larsson, T., & Thorsén, R. (2018). Cryptocurrency performance analysis of Burstcoin mining.
Lei, N., Masanet, E., & Koomey, J. (2020). Best practices for analyzing the direct energy use of blockchain technology systems: Review and recommendations.
Indexed at, Google Scholar, Cross Ref
Lei, N., Masanet, E., & Koomey, J. (2021). Best practices for analyzing the direct energy use of blockchain technology systems: Review and policy recommendations. Energy Policy, 156, 112422.
Li, A., Wei, X., & He, Z. (2020). Robust proof of stake: A new consensus protocol for sustainable blockchain systems. Sustainability, 12(7), 2824.
Indexed at, Google Scholar, Cross Ref
Li, K., Li, H., Hou, H., Li, K., & Chen, Y. (2017, December). Proof of vote: A high-performance consensus protocol based on vote mechanism & consortium blockchain. In 2017 IEEE 19th International Conference on High Performance Computing and Communications; IEEE 15th International Conference on Smart City; IEEE 3rd International Conference on Data Science and Systems (HPCC/SmartCity/DSS) (pp. 466-473). IEEE.
Indexed at, Google Scholar, Cross Ref
Lucas, B., & Páez, R. V. (2019, July). Consensus algorithm for a private blockchain. In 2019 IEEE 9th International Conference on Electronics Information and Emergency Communication (ICEIEC) (pp. 264-271). IEEE.
Luu, L., Narayanan, V., Zheng, C., Baweja, K., Gilbert, S., & Saxena, P. (2016). A secure sharding protocol for open blockchains. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, 17-30.
Mearian, L. (2020). MIT’s blockchain-based ‘Spider’offers 4X faster cryptocurrency processing. ComputerWorld, Feb.
Mehar, M. I., Shier, C. L., Giambattista, A., Gong, E., Fletcher, G., Sanayhie, R., ... & Laskowski, M. (2019). Understanding a revolutionary and flawed grand experiment in blockchain: the DAO attack. Journal of Cases on Information Technology (JCIT), 21(1), 19-32.
Miglani, A., Kumar, N., Chamola, V., & Zeadally, S. (2020). Blockchain for Internet of Energy management: Review, solutions, and challenges. Computer Communications, 151, 395-418.
Indexed at, Google Scholar, Cross Ref
Mingxiao, D., Xiaofeng, M., Zhe, Z., Xiangwei, W., & Qijun, C. (2017, October). A review on consensus algorithm of blockchain. In 2017 IEEE international conference on systems, man, and cybernetics (SMC) (pp. 2567-2572). IEEE.
Möser, M., Eyal, I., & Sirer, E. G. (2016, February). Bitcoin covenants. In International conference on financial cryptography and data security (pp. 126-141). Springer, Berlin, Heidelberg.
Nakamoto, S. (2008a). Bitcoin: A Peer to Peer Electronic Cash System, self-published paper
Nakamoto, S. (2008b). Bitcoin: A peer-to-peer electronic cash system. Decentralized Business Review, 21260.
Nakamoto, S., & Bitcoin, A. (2008). https://bitcoin. org/bitcoin. pdf, 4.
Namasudra, S., Deka, G. C., Johri, P., Hosseinpour, M., & Gandomi, A. H. (2021). The revolution of blockchain: State-of-the-art and research challenges. Archives of Computational Methods in Engineering, 28(3), 1497-1515.
Indexed at, Google Scholar, Cross Ref
Narayanan, A., Bonneau, J., Felten, E., Miller, A., & Goldfeder, S. (2016). Bitcoin and cryptocurrency technologies: a comprehensive introduction. Princeton University Press.
Nguyen, G. T., & Kim, K. (2018). A survey about consensus algorithms used in blockchain. Journal of Information processing systems, 14(1), 101-128.
Ongaro, D., & Ousterhout, J. (2014). In search of an understandable consensus algorithm. In 2014 {USENIX} Annual Technical Conference ({USENIX}{ATC} 14) (pp. 305-319).
P4Titan. "Slimcoin: A peer-to-peer crypto-currency with proof-of-burn", Available: http://www.doc.ic.ac.uk/ds/realdotdot/crypto_papers_etc_worth_reading/proof_of_burn/slimcoin_whitepaper.pdf, 2014, Accessed September 18, 2018.
Powell, L. M., Hendon, M., Mangle, A., & Wimmer, H. (2021). Awareness of blockchain usage, structure, & generation of platform’s energy consumption: Working towards a greener blockchain. Issues in Information Systems, 22(1), 114.
Ren, Z., Cong, K., Pouwelse, J., & Erkin, Z. (2017). Implicit consensus: Blockchain with unbounded throughput. arXiv preprint arXiv:1705.11046.
Roma, C. A., & Hasan, M. A. (2020, May). Energy consumption analysis of XRP validator. In 2020 IEEE International Conference on Blockchain and Cryptocurrency (ICBC) (pp. 1-3). IEEE.
Saingre, D., Ledoux, T., & Menaud, J. M. (2020, November). BCTMark: a framework for benchmarking blockchain technologies. In 2020 IEEE/ACS 17th International Conference on Computer Systems and Applications (AICCSA) (pp. 1-8). IEEE.
Indexed at, Google Scholar, Cross Ref
Saleh, F. (2021). Blockchain without waste: Proof-of-stake. The Review of financial studies, 34(3), 1156-1190.
Sankar, L. S., Sindhu, M., & Sethumadhavan, M. (2017, January). Survey of consensus protocols on blockchain applications. In 2017 4th International Conference on Advanced Computing and Communication Systems (ICACCS) (pp. 1-5). IEEE.
Schwartz, D., Youngs, N., & Britto, A. (2014). https://ripple. com/files/ripple_consensus_whitepaper. pdf.
Sedlmeir, J., Buhl, H. U., Fridgen, G., & Keller, R. (2020). The energy consumption of blockchain technology: Beyond myth. Business & Information Systems Engineering, 62(6), 599-608.
Indexed at, Google Scholar, Cross Ref
Shen, C., & Pena-Mora, F. (2018). Blockchain for cities—a systematic literature review. Ieee Access, 6, 76787-76819.
Stifter, N., Judmayer, A., & Weippl, E. (2019). Revisiting practical byzantine fault tolerance through blockchain technologies. In Security and Quality in Cyber-Physical Systems Engineering (pp. 471-495). Springer, Cham.
Indexed at, Google Scholar, Cross Ref
Sukhwani, H., Martínez, J. M., Chang, X., Trivedi, K. S., & Rindos, A. (2017, September). Performance modeling of PBFT consensus process for permissioned blockchain network (hyperledger fabric). In 2017 IEEE 36th Symposium on Reliable Distributed Systems (SRDS) (pp. 253-255). IEEE.
Tang, H., Shi, Y., & Dong, P. (2019). Public blockchain evaluation using entropy and TOPSIS. Expert Systems with Applications, 117, 204-210.
Tedeschi, P., Piro, G., Murillo, J. A. S., Ignjatov, N., Pilc, M., Lebloch, K., & Boggia, G. (2019). Blockchain as a service: Securing bartering functionalities in the H2020 symbIoTe framework. Internet Technology Letters, 2(1), e72.
Vranken, H. (2017). Sustainability of bitcoin and blockchains. Current opinion in environmental sustainability, 28, 1-9.
Wang, L., Shen, X., Li, J., Shao, J., & Yang, Y. (2019). Cryptographic primitives in blockchains. Journal of Network and Computer Applications, 127, 43-58.
Wang, T. (2018). A unified analytical framework for trustable machine learning and automation running with blockchain. In 2018 IEEE International Conference on Big Data (Big Data) (pp. 4974-4983). IEEE.
Wang, W., Hoang, D. T., Hu, P., Xiong, Z., Niyato, D., Wang, P., ... & Kim, D. I. (2019 a). A survey on consensus mechanisms and mining strategy management in blockchain networks. IEEE Access, 7, 22328-22370.
Wei, X., Li, A., & He, Z. (2020). Impacts of consensus protocols and trade network topologies on blockchain system performance. Journal of Artificial Societies and Social Simulation, 23(3).
Xu, B., Luthra, D., Cole, Z., & Blakely, N. (2018). https://www.whiteblock.io/library/eos-test-report. pdf.
Yadav, A. K., & Singh, K. (2021). Comparative Analysis of Consensus Algorithms and Issues in Integration of Blockchain with IoT. In Smart Innovations in Communication and Computational Sciences (pp. 25-46). Springer, Singapore.
Zade, M., Myklebost, J., Tzscheutschler, P., & Wagner, U. (2019). Is bitcoin the only problem? a scenario model for the power demand of blockchains. Frontiers in Energy Research, 7, 21.
Indexed at, Google Scholar, Cross Ref
Zheng, Z., Xie, S., Dai, H., Chen, X., & Wang, H. (2017). An overview of blockchain technology: Architecture, consensus, and future trends. In 2017 IEEE international congress on big data (BigData congress) (pp. 557-564). IEEE.
Zheng, Z., Xie, S., Dai, H. N., Chen, X., & Wang, H. (2018). Blockchain challenges and opportunities: A survey. International Journal of Web and Grid Services, 14(4), 352-375.
Zhou, Y. (2017). The evolution of blockchain core technology-consensus mechanism evolution. Comput. Educ, 4, 5-9.
Zou, J., Ye, B., Qu, L., Wang, Y., Orgun, M. A., & Li, L. (2018). A proof-of-trust consensus protocol for enhancing accountability in crowdsourcing services. IEEE Transactions on Services Computing, 12(3), 429-445.
Received: 27-Oct-2022, Manuscript No. AMSJ-22-12751; Editor assigned: 31-Oct-2022, PreQC No. AMSJ-22-12751(PQ); Reviewed: 17-Nov-2022, QC No. AMSJ-22-12751; Revised: 02-Dec-2022, Manuscript No. AMSJ-22-12751(R); Published: 05-Jan-2023