Research Article: 2021 Vol: 25 Issue: 6
Online Shopping Behaviours of Generation Y In Canada Behavioural Technology Adoption Models
Allen Lim Chong Guan, East Stroudsburg University
Goi Chai Lee, Curtin University
Peter Dell, Curtin University
Citation Information: Guan, A.L.C., Lee, G.C, & Dell, P. (2021). Online shopping behaviours of generation y in canada: behavioural technology adoption models. Academy of Marketing Studies Journal, 25(6), 1-19.
Abstract
Keywords
Behavioural Technology Adoption Model, Youngest Generation, Online Shopping Behaviour, E-Commerce.
Introduction
Three classifications form the basis of this research. The first involves small business retail, Internet commerce, social networking and mobile marketing, Internet infrastructure, and strategic models. The second involves Generation Y and the third includes behavioural models. Factors contributing to the diffusion of the Internet and e-commerce have been widely covered in previous studies. There are various relevant models and theories that can be applied to explain the usage of the retail websites of small businesses by Generation Y consumers in Canada, and they have overlapping factors. The models and theories discussed so far can be viewed from both the consumers’ and the organisations’ perspectives interchangeably. The theories and models reviewed are Value Chain Analysis (Porter, 1985), Five Forces Model (Porter, 1979), Generic Strategies Model (Porter, 1980), Blue Ocean Strategy (Kim & Mauborgne, 2005), Service Quality (Ziethaml, Parasuraman and Malhotra, 2002), Theory of Reasoned Action (TRA) (Ajzen & Fishbein, 1980), Theory of Planned Behaviour (TPB) (Ajzen, 1991), Diffusion of Innovation Model (Rogers, 2003), Technology Acceptance Model (TAM) (Davis, 1989), Unified Theory of Acceptance and Use of Technology (UTAUT) (Venkatesh et al., 2003), and Unified Theory of Acceptance and Use of Technology Two (UTAUT2) (Venkatesh, Thong and Xu, 2012).
Some researchers have applied behavioural models to predict Internet adoption, such as the Theory of Reasoned Action (TRA) (Ajzen and Fishbein, 1980), Theory of Planned Behaviour (TPB) (Ajzen, 1991; Ajzen and Fishbein, 1980), Diffusion of Innovation Model (Rogers, 2003), and Technology Acceptance Model (TAM) (Davis, 1989), Unified Theory of Acceptance and Use of Technology (UTAUT) (Venkatesh et al., 2003), and Unified Theory of Acceptance and Use of Technology Two (UTAUT2) (Venkatesh, Thong and Xu, 2012).
Among the various diffusion models, Unified Theory of Acceptance and Use of Technology Two (UTAUT2), the updated version of UTAUT, is the most robust and reliable (Venkatesh, Thong and Xu, 2012). It was first developed for use with consumer usage of mobile internet in Hong Kong. UTAUT2 comprises performance expectancy, effort expectancy, social influence, facilitating conditions, hedonic motivation, price value, and habit. It has three moderators that are age, gender, and experience. UTAUT2 focuses on consumer adoption and is most suited for this research that focuses on Canadian Generation Y consumers.
Methodology
This section explains the methodology used in this research. It describes the research paradigm, and focuses on the study overview methods. The study reviewed the existing literature to develop the existing research model. The eleven factors identified as significant are performance expectancy, effort expectancy, social influence, facilitating conditions, hedonic motivation, price value, habit, security and privacy, trust, behavioural intention, and use behaviour.
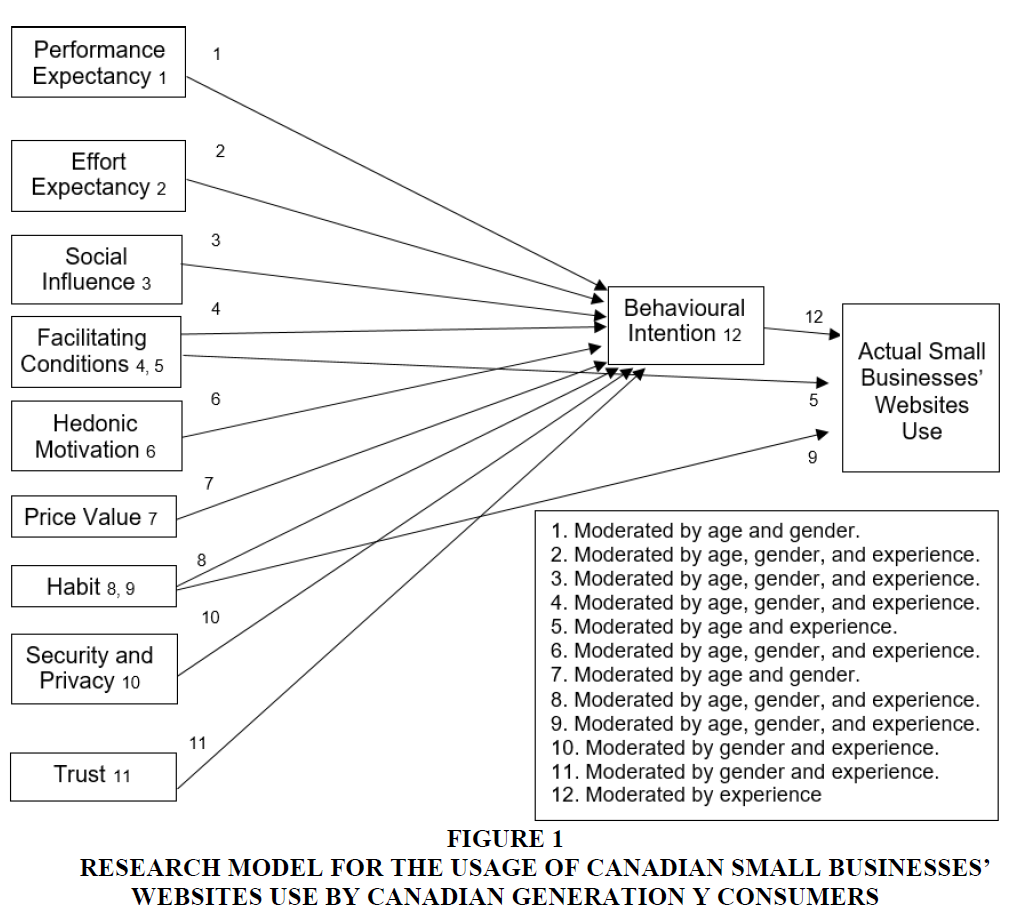
The research model, as shown below in Figure 1, is hypothesised after reviewing all the relevant models and theories in an attempt to answer the Generation Y consumers’ usage of the retail websites of small businesses in Canada.
Figure 1 Research Model for the Usage of Canadian Small Businesses’ Websites use by Canadian Generation Y Consumers
UTAUT2 is the mainstay of the research model that comprises performance expectancy, effort expectancy, social influence, facilitating conditions, hedonic motivation, price value, habit, behavioural intention, and user behaviour (Venkatesh, Thong and Xu, 2012). The three moderating variables are age, gender, and experience, and the two additional factors of security and privacy and of trust. The moderating variables applied to the initial factors are based on the original UTAUT2. The security and privacy factor and the trust factor are moderated by the existing variables supported by literature review. The research model is shown below in Figure 1.
Keywords such as Canadian Generation Y, Generation Y, diffusion, adoption, acceptance, technology, retail, small business, social media, consumers, Internet commerce, electronic commerce, e-commerce, digital marketing, digital commerce, and Internet marketing in various combinations were searched in Business Source, eBook Library, Emerald, Informit, ProQuest, ScienceDirect, Scopus, SpringerLink, Wiley Online Library, Google Scholar, Google, and others, especially the latest publications within the last five years. For non-journal materials, the researcher searched for keywords in Google Scholar, Ebsco, and SpringerLink. Generally, the literature review is based on descriptive materials. Based on a keyword search, other information was discovered and, subsequently, led to more information.
Research Paradigm
This section explains the paradigm for this research. A paradigm is described as a set of assumptions, concepts, and values held by the researcher (Johnson and Christensen, 2008). Since the 1960s, the term “paradigm” has been used to explain the philosophy of the scientific disciplines or epistemological perspectives that have guided the study. Two different philosophical perspectives for a research are the positivist and interpretivist/phenomenological paradigms (Easterby-Smith, Thorpe and Lowe, 1991). The positivist paradigm is the same as the quantitative paradigm, which believes in studying phenomenon by following a scientific method, free from value judgments and from an objective perspective (Khan et al., 2020; Donepudi et al., 2020; Zhu et al., 2021; Vadlamudi et al., 2021a; Paruchuri et al., 2021; Vadlamudi et al., 2021b; Ganapathy et al., 2021; Hussain et al., 2021). The interpretivist paradigm, on the other hand, is the same as the qualitative paradigm. This philosophy believes in studying a phenomenon through the subjective opinions of the actors involved in a situation. The major difference between the two perspectives is that positivists believe social science studies should be modelled after studies in the sciences to discover facts, while the interpretivists believe that there are no “facts” in social science, only subjective realities.
Qualitative Paradigm
The qualitative paradigm began to evolve from the 1980s and has a different ontological and epistemological perspective than the quantitative paradigm (Johnson and Christensen, 2008). The ontology for the qualitative paradigm is that reality is subjective and has multiple views to it (Creswell, 1994). For qualitative researchers, the perspective of a study is not to prove a theory per se but to ascertain facts as they exist (Johnson and Christensen, 2008). There are many realities in the world that are socially constructed, interpreted and subjected to various perspectives (Johnson and Christensen, 2008). Qualitative research is a generic term used for different methodologies such as case studies, naturalistic inquiry, ethnography, and phenomenological studies (Bogdan and Biklen, 1982).
The ontology of the qualitative paradigm is based on interpretivist (Creswell, 2003; Sale, Lohfeld and Brazil, 2002) and is widely used in the MIS discipline because of the rapid technological advancements in this field (Sutherland, 2016). For interpretivists, the definition of behaviour is based on understanding it instead of trying to explain its meaning within a pre-constructed framework. Having an extensive interview, with both structured and unstructured elements, can ensure that the interviewees understand the questions and the researcher understands their interpretation (Denzin and Lincoln, 2011; Saunders, Lewis and Thornhill, 2003). For this study, the interpretivist paradigm is used to support and to improve the reliability of the positivist paradigm. Just like quantitative research, qualitative research also has numerous strengths (Johnson and Onwuegbuzie, 2004). The data gathered from participants offers an insight into their thoughts, experiences as well as the interpretation of a phenomenon based on its natural settings, local conditions, and the stakeholders’ perspectives. By studying a limited number of cases in detail, researchers are able to provide answers to complex and dynamic phenomena. Using cross-analysis among the case studies, the researchers can use inductive logic and arrive at an explanatory theory. Qualitative research also has a few weaknesses (Johnson and Onwuegbuzie, 2004). The information gathered may not be generalised for other people and environments. It is also more difficult to test hypotheses and theories and quantitatively predict a phenomenon. Data collection and data analysis for qualitative research take longer than for quantitative research. The results are also more likely to be influenced by the researcher.
For this research, both inductive and deductive approaches are to be utilised. The existing knowledge base have been used to form the study outline, while the findings of the study has been used to formulate any theories that may emerge. However, this study leans towards a deductive approach as it intends to certify whether the study outline are valid or not.
Behavioural Intention (Bi)
BI is the strength of an individual to carry out a specific behaviour (Fishbein and Ajzen, 1975) and is a strong predictor of the actual use of information technologies (Venkatesh et al., 2003). It has a direct positive relationship with use behaviour, and the moderator is experience (Venkatesh, Thong and Xu, 2012). It is generally accepted by researchers that BI is the extent of readiness and the likelihood of conducting a particular behaviour in the future (Ajzen, 1991).
However, BI or purchase intention does not always translate to actual purchase (Shih and Fang, 2004). Positive and negative emotions have different effects on BI (Koenig-Lewis and Palmer, 2014). Positive emotions are linked to positive consequences, whereas negative emotions are linked with negative consequences (Babin and Babin, 2001). Therefore, scales that are designed to gauge respondents’ emotional responses can predict the consumers’ BI (Andrade, 2005).
Individuals can change their decision to purchase when making real-life decisions. The relationship with BI is ever-changing and based on multiple entities (Karahanna, Agarwal and Angst, 2006). BI does not relate strongly to the external factors based on unforeseen circumstances or unusual events. External and internal stimuli can change rapidly and, thus, impact BI. Factors that beyond the control of the consumers cannot accurately foretell BI.
For the questionnaire survey, only Canadian Generation Y consumers who have had an experience of buying goods/services from the retail websites of Canadian small businesses are included in the sample. The purpose of this research is to identify the contributing factors and variables that can encourage these consumers to have repurchase intentions from different Canadian small business retail websites. The items under the behavioural intention section enquire about the intention to purchase again from these retail websites.
Use behaviour or actual behaviour can be measured on the basis of the frequency of use (Venkatesh, Thong and Xu, 2012). There is a difference between use behaviour or actual behaviour and BI. Similar to Venkatesh, Thong and Xu (2012), Wu and Wang (2005) also define use behaviour as the measurement of actual behaviour, whereas BI is the measurement of the likelihood of an individual carrying out an action. Some examples of use behaviour have been added as a part of a model on actual mobile Internet browsing, instant messaging, and Internet banking (Moon and Kim, 2001).
Although there is a high correlation between BI and actual use (Bernadette, 1996), the time interval between BI and use behaviour can hinder the actual purchase (Fishbein and Ajzen, 1975). For example, although an individual wants to change his or her smartphone for a newer version, he/she may be deterred from doing so after realising the high switching costs from the existing contractual obligation. Likewise, when a person has openly mentioned that he or she wants to change his actual behaviour, it may not happen if the existing habit is still strong (Webb and Sheeran, 2006).
Behavioural Technology Adoption Models
Theory of reasoned action (TRA)
Theory of Reasoned Action (TRA), presented in Figure 2 below, is a model used to study human intention behaviour (Fishbein and Ajzen, 1975). It has contributed significantly to different marketing areas (Bonera, 2011). However, the basic TRA lacks the internal and external considerations when making a decision about using a technology (Bonera, 2011). The underlying concept of TRA is based on the salient beliefs used to identify attitudes and subsequent behaviour intentions and behaviour (Fishbein and Ajzen, 1975). Attitude refers to an individual’s positive or negative feelings for carrying out specific target behaviour. Social norms are influenced by group normative beliefs such as those of friends, family, or relatives, and these beliefs subsequently influence behavioural intention for each individual.
Theory of Planned Behaviour (TPB)
Theory of Planned Behaviour (TPB) (Ajzen, 1985; Ajzen, 1991) was established by extending the Theory of Reasoned Action (TRA) (Ajzen and Fishbein, 1980). An individual’s behaviour is predicted by intentions based on their attitude towards behaviour, attitude, subjective norms, and perceived behavioural control.
The first and second factors are the attitudes towards behaviour used to describe the users’ feelings that will ultimately lead to the decision of whether to use a technology (Amin and Nayak, 2010). The third factor or the subjective norms refer to a user’s decision about a technology that will be affected, for example, by other users’ opinions. Subjective norms, therefore, are similar to social influences (Taylor and Todd, 1995). The limitation of subjective norms is that they cannot be observed (Ozkan and Kanat, 2011). They are more important for novice, users and the relationship between them and intentions is stronger when the users are inexperienced (Taylor and Todd, 1995).
The fourth factor is the perceived behavioural control that refers to time and experience, among other factors (Amin and Nayak, 2010). Perceived behavioural control in most research studies is not a critical predictor of intentions or behaviour. Both subjective norms and perceived control behaviour are the antecedents of perceived usefulness (PU) (TAM) and perceived ease of use (PEOU) (Hu and Dinev, 2005).
Rogers’s Diffusion of Innovation Model
The diffusion of an innovation is not a one-time conclusion but a continuous one (Rogers, 1995). Rogers’s Diffusion of Innovation Model can be classified into the factors of relative advantage, complexity, compatibility, trial ability, and observability (Rogers, 2003). Relative advantage is defined as the extent to which an innovation is perceived to be better than before (Rogers, 2003). In short, it is perceived as the degree to which an innovation has brought additional benefits for a user. It can be measured in the forms of profitability, productivity, and other benefits. Complexity is the degree to which an innovation is perceived to be easy or difficult to comprehend and use.
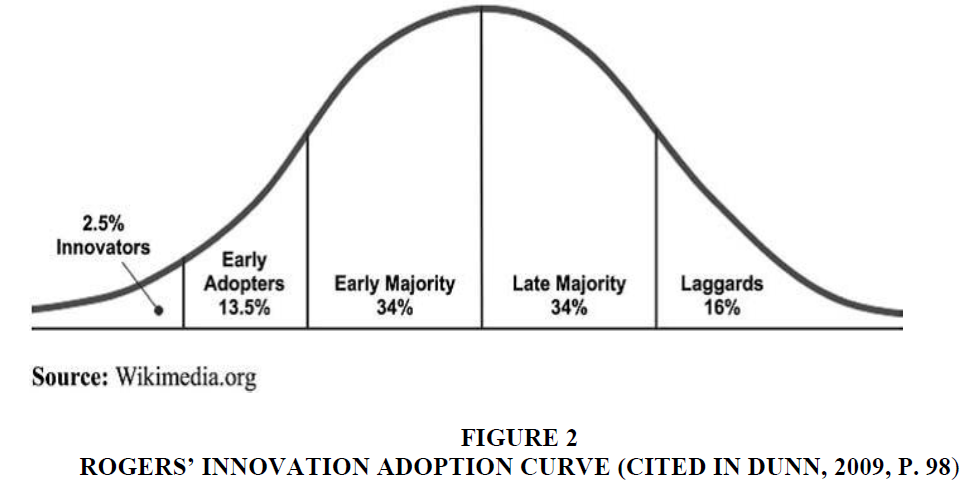
The Rogers’ Diffusion of Innovation Model includes four elements that comprise innovation, communication channels, social systems, and time (Rogers, 2003).
1. The first element is innovation and consists of mainly technological innovations which are adopted faster than the others. The factors that affect the speed of adoption are the relative advantages, compatibility, complexity, trial ability, and observability of the innovations.
2. The second element is the communication channel used to pass information about the inventions to the potential users (Rogers, 2003). Examples of communication channels are the radio, television, magazines, books, signboards, newspapers, fairs, interest groups, and word-of-mouth publicity. Innovators tend to have technical knowledge that potential users may not have or understand, which is why having change agents to communicate them is important.
3. The third element is the social system based on boundaries, status, values, objectives, ethics, cultures, norms, and other demographic variables (Rogers, 2003). These factors can play a vital role in how quickly the innovations are adopted.
4. The fourth element is time as only time can tell whether an innovation is successful or not (Rogers, 2003). Not all users adopt a new technology simultaneously, and it tends to spread over time. Users or adopters can be classified into innovators (2.5 per cent), early adopters (13.5 per cent), early majority (34 per cent), late majority (34 per cent), and laggards (16 per cent) based on the different timeframes of adopting the innovation (Figure 2 below).
There are major drawbacks of Rogers’ Diffusion of Innovation Model. A theoretical framework for the adoption of new technology should include and consider a wide range of variables to try to gain maximum adoption in the market (MacVaugh and Schiavone, 2010). Some variables may be directly or indirectly influenced by the new technology, whereas others may be external and restrictive to the new technology and better suited for existing technology. Technology adoption needs to be based on a multidisciplinary approach which requires meta-analyses. Rogers’ Diffusion of Innovation Model is more suited to organisational actions for the implementation of an innovation. The innovation diffusion theory helps to explain how a technology can be included in the organisations from the aspect of marketing and how an innovation can be diffused into a social system (Rogers, 1995).
Technology Acceptance Model (TAM)
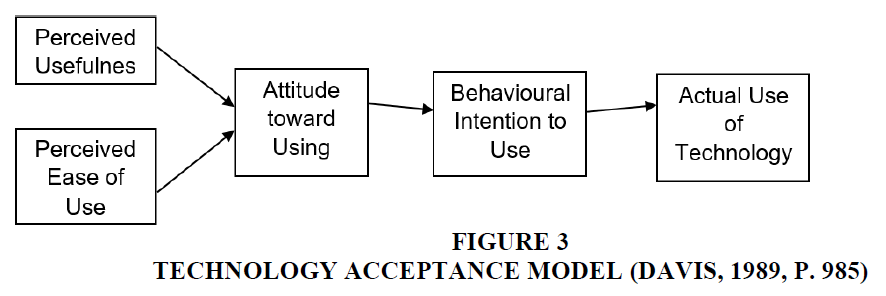
Technology Acceptance Model (TAM) is a widely recognised user acceptance model for new technologies (Park, Son and Kin, 2012). It is viewed more positively by researchers and considered more straightforward (Davis, 1989) (Figure 2) than the Theory of Reasoned Action (TRA) and the Theory of Planned Behaviour (TPB) because it has fewer factors (Yayla and Hu, 2007; Zarmpou, Saprikis, Markos and Vlachopoulou, 2012). Taylor and Todd (1995) have favoured TAM over TPB because it can better predict the usage behaviour of IT. It is also considered cheaper and easier to use than TRA (Davis, Bagozzi and Warshaw, 1989). TAM is superior in usage for compulsory settings to a combined model (TAM and TPB) (Venkatesh, Morris, Davis and Davis, 2003). It is also more suited to technology imperative than TPB, which is more suitable for organisational and social perspectives (Yayla and Hu, 2007).
TAM predicts the users’ attitudes and behaviours based on the perceived usefulness (PU) and the perceived ease of use (PEOU) (Davis, 1989). Perceived usefulness (PU) refers to the degree to which the users believe that using a technology can increase their performance. Inexperienced users gain more from the perceived usefulness for the use of the Internet (Hernandez, Jimenez and Martin, 2009). Perceived ease of use (PEOU) refers to how easy it is to use a technology (Davis, 1989). Past studies have identified that the PEU becomes insignificant when users have gained the technological know-how, (Sun and Zhang, 2006).
Attitude is considered one of the determinants of TAM in its early models (Davis, 1989) (Figure 3 below) and defined as positive or negative beliefs and change behaviour (Ajzen, 1991). The users of new technologies tend to use a new technology because of their functionality rather than their ease of use. Irrespective of how difficult a new technology is to adopt, users are willing to learn it if they find that the benefits of using it are substantial.
TAM has been evolving since it was first developed by Davis (1989). A longitudinal research carried out by Davis, Bagozzi and Warshaw (1989) found that PU has a strong relationship with behavioural intention, whereas PEOU has a limited but significant impact on behavioural intention that diminishes over time. Both PU and PEOU have a direct relationship with behavioural intention, and therefore the attitude component can be removed. However, Davis (1993) states that PU can have a direct influence on system use, while system characteristics have a direct relation to attitude, without the need to develop a belief.
Most of the research using TAM has found a strong statistical relationship between PU and behavioural intention (Chuttur, 2009) as proposed in the final version of TAM by Venkatesh and Davis (1996). However, results were mixed regarding a direct relationship between PEOU and actual use.
Website satisfaction was also found to have a positive influence on the intention to purchase (Belanche, Casalo and Guinaliu, 2012). However, behavioural intentions (BIs) are different from behavioural goals, which refer to continued purchase behaviour in an electronic commerce environment. The success of new technology acceptance should also be based on continuous use rather than a one-time experience (Bhattacherjee, 2001). Amazon.com and other websites are offering users registration to the products they have the intention to purchase in the future. Companies should propose incentives for these prospective customers as the chances of purchase diminish the longer the products are in the waitlist.
Unified Theory of Acceptance and Use of Technology Two (UTAUT2)
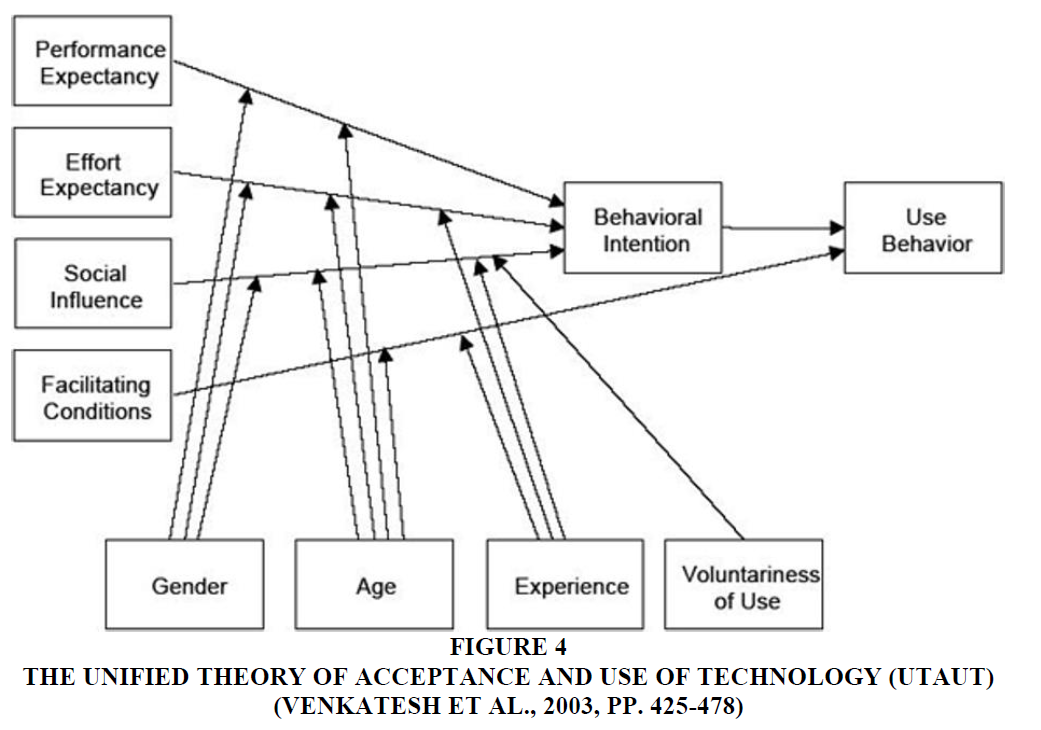
The Unified Theory of Acceptance and Use of Technology (UTAUT) integrates eight theories that include TAM to explain technology acceptance and its use by employees (Venkatesh, Davis, Davis and Morris, 2003) through TAM predictive criticism (Agarwal and Prasad, 1998). UTAUT can explain up to 70 per cent of technology acceptance characteristics (Masrom and Hussein, 2008). The models that have been reviewed are Social Cognitive Theory (SCT), Motivational Model (MM), Model of PC Utilization, Theory of Reasoned Action (TRA), Technology Planned Behaviour (TPB), Diffusion Innovation Theory (DIT), Technology Acceptance Model (TAM), and the TAM/TPB combination (Venkatesh et al., 2003). The main four determinants have been identified as effort expectancy, performance expectancy, social influence, and facilitating conditions. The moderating variables that affect the intention to use and behaviour are age, gender, experience, and voluntariness. TAM has a limited predictive capability compared to UTAUT, which is more integrative but less effective in explaining the intervention factors that promote adoption (Brown, Dennis and Venkatesh, 2010). The UTAUT model is shown below in Figure 4.
Figure 4 The Unified Theory of Acceptance and use of Technology (Utaut) (Venkatesh et al., 2003, PP. 425-478)
UTAUT has been used to study mobile payments in China (Wang and Yi, 2012) and social networking in a developing country. It is also applied to a research on the use of travel content for mobile smartphones (No and Kim, 2014) and interactive whiteboards.
UTAUT2 was established to accommodate the needs of the consumers for the technology acceptance of mobile internet in Hong Kong (Venkatesh, Thong and Xu, 2012). When compared to UTAUT, UTAUT2 has an improved explanation for the variances in BI from 56 per cent to 74 per cent. It also has an improved explanation for variances in usage from 40 per cent to 52 per cent. In UTAUT2, with the inclusion of its moderating variables, the explanation for variances in BI has also increased from 44 per cent to 74 per cent. The inclusion of its moderating variables increased the explanation for variances in usage from 35 per cent to 52 per cent. UTAUT2 is also used in a study on the customer usage of mobile Internet in Latvia (Fuksa, 2013) and the social networking incentives for the participants (Koohikamali, Gerhart and Mousavizadeh, 2015). However, according to Venkatesh, Thong and Xu (2012), future research for UTAUT2 should include different technologies from different age groups from different countries.
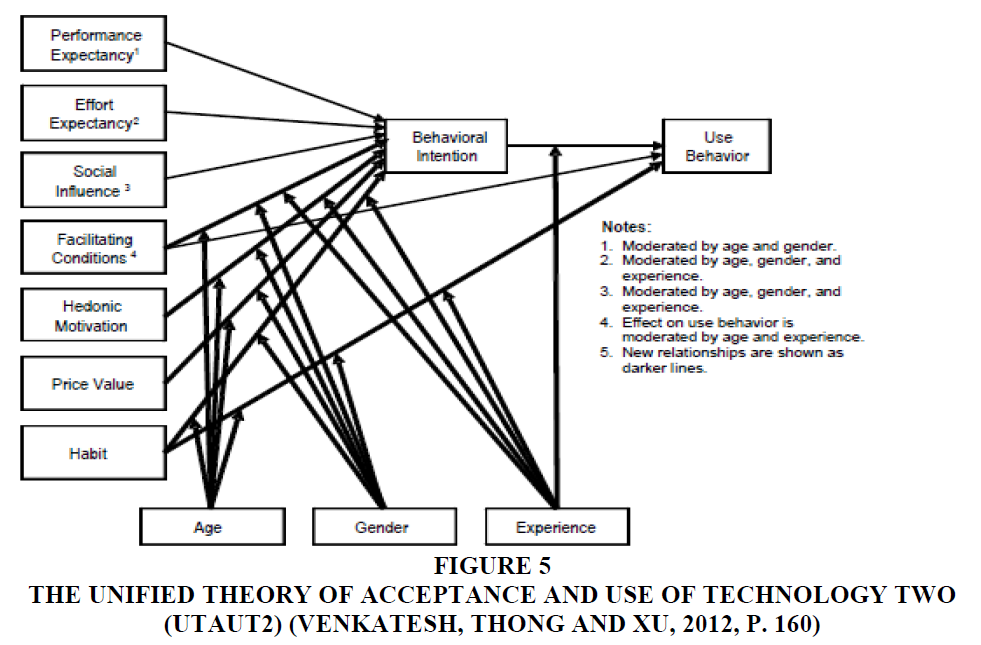
Figure 5 below shows the original Unified Theory of Acceptance and Use of Technology Two (UTAUT2) (Venkatesh, Thong and Xu, 2012, p. 160).
Figure 5 The Unified theory of Acceptance and use of Technology two (Utaut2) (Venkatesh, Thong and Xu, 2012, P. 160)
Unlike UTAUT, which is focused on organisations, the UTAUT2 model is customised to focus on consumer usage of technology (Venkatesh, Thong and Xu, 2012) and therefore more suited for this study that focuses on Canadian Generation Y consumers.
Below are the section-wise factors and moderating variables for UTAUT2. The factors comprise performance expectancy, effort expectancy, social influence, facilitating conditions, hedonic motivation, price value, habit, behavioural intention, and use behaviour. The moderating variables are age, gender, and experience, and the two additional factors included are security and privacy, and trust.
Performance Expectancy
Performance expectancy refers to how a person perceives a technology that can improve his or her competency and is an important construct in UTAUT (Venkatesh et al., 2003). It is similar to PU in TAM (Fuksa, 2013) and relative advantage in the Diffusion Innovation Model. Performance expectancy has a direct positive relationship with BI and is moderated by age and gender (Venkatesh, Thong and Xu, 2012). In a study on the use of innovative Internet intermediary platforms, performance expectancy was found to have a strong positive significant relationship with BI (Chu, 2013).
Effort Expectancy
Effort expectancy refers to the number of efforts required to use a technology (Venkatesh et al., 2003; Venkatesh, Thong and Xu, 2012). It is similar to PEOU in TAM and complexity factors in the Diffusion of Innovation Model. Effort expectancy has a direct positive relationship with BI and is moderated by age, gender, and experience (Venkatesh, Thong and Xu, 2012). Effort expectancy can only be realised when a technology has been tested out by a user, and he or she can change her mind or perception about the difficulty of use of technology based on that experience (Venkatesh and Davis, 1996). Therefore, effort expectancy highly influences technology use, but this influence diminishes once the users are accustomed to it (Agarwal and Prasad, 1998).
Social Influence
Social influence is defined as the extent to which individuals perceive the importance of others’ beliefs in a technology (Venkatesh et al., 2003). It is similar to the subjective norms of Theory of Planned Behaviour (Taylor and Todd, 1995) and the social/cultural infrastructure in the Model of Diffusion Global E-Commerce (Jayalgi and Ramsey, 2001). Social influence has a direct positive relationship with BI and is moderated by age, gender, and experience (Venkatesh, Thong and Xu, 2012). Social influence can be affected by relationships with family members, friends, superiors, colleagues, teachers, and community members. It is similar to the subjective norms of TPB and TRA (Venkatesh et al., 2003). Social influence can also be found in social media whereby consumers share their experiences with others.
Facilitating Conditions
Facilitating conditions are defined as the training and support provided to organisations and consumers for technology use (Venkatesh, Thong and Xu, 2012). It is similar to behavioural control in the Theory of Planned Behaviour (Ajzen, 1991) and technology infrastructure in the Model of Diffusion Global E-Commerce (Jayalgi and Ramsey, 2001). Facilitating conditions have a direct positive relationship with BI and are moderated by age, gender, and experience (Venkatesh, Thong and Xu, 2012). They also have a positive direct relationship with use behaviour, with the moderators being age and experience. Facilitating conditions can also come in the form of superior user interface such as search, navigate, and access (Yang, 2010). Facilitating conditions do have a significant impact on the use behaviour as shown by a research on the use of innovative Internet intermediary platforms (Chu, 2013) and Internet marketing behavioural intentions by Malaysians and South Koreans.
Hedonic Motivation
Hedonic motivation refers to the excitement or fun of using a technology and provides self-satisfaction to the users. Customers can experience positive or negative emotions while using a technology (Cambria, Schuller, Liu, Wang and Havasi, 2013). Positive emotions refer to enjoyment and playfulness, whereas depression and anger are negative emotions (Laros and Steenkamp, 2005). Hedonic motivation has a direct positive relationship with BI and is moderated by age, gender, and experience (Venkatesh, Thong and Xu, 2012).
Price Value
Price value has a positive direct relationship with BI, and the moderators are age and gender. It can bring more benefits and influence the behavioural intention to use a particular technology. This includes the cost of using a mobile internet (Binde and Fuksa, 2013). The cheap cost of using a technology may encourage individuals to use it frequently (Leonardi, 2011) and source cheaper products through the internet (Jensen, 2012). For example, buying textbooks from Amazon.com can save up to 30 per cent of the cost of new textbooks and up to 90 per cent for used ones (Mimouni-Chaabane and Volle, 2010). The main reason that consumers purchase online air tickets from budget airlines is because of cheaper price rates.
Habit
Habit refers to an individual learning that results in the likelihood of performing a behaviour spontaneously (Venkatesh, Thong and Xu, 2012) and can explain a large variance in a user’s continuous use of a website (Gefen, 2003). It has a positive direct relationship with BI, and the moderators are age, gender, and experience (Venkatesh, Thong and Xu, 2012). Habit also has a direct positive relationship with use behaviour, and the moderators are age, gender, and experience. The stronger the habit, the less conscious a person is towards his or her intention to use a specific technology (Limayem, Hirt and Cheung, 2007). A technology is deemed to be in continuous use when it has been accepted by the user (Schoonenboom, 2012). However, in the study by Hsu and Lin (2015), habit did not have any direct impact on users’ intention to purchase in a mobile commerce environment.
Age
Age is the moderator for the positive direct relationship between facilitating conditions, hedonic motivation, price value, habit, and BI for UTAUT2 (Venkatesh, Thong and Xu, 2012). It also acts as a moderator for the direct relationship between habit and use behaviour. Younger people find it easier to adapt to new technology (Chong, 2013); therefore, age has a moderating effect on online shopping (Lian and Yen, 2014) and online banking use. When it comes to technology use, older people’s mental and physical factors have been overlooked (Chen and Chan, 2011). Information technology can improve the quality of life for older people by providing online learning, online shopping, and online socialising (Hough and Kobylanski, 2009). However, the current research is focused on Canadian Generation Y consumers between the age of 18 and 36 (in 2015).
Gender
Gender is the moderator for the positive relationship between facilitating conditions, hedonic motivation, price value, habit, and behavioural intention factors for UTAUT2 (Venkatesh, Thong and Xu, 2012). It also acts as the moderator for the positive relationship between habit and use behaviour. Several previous studies have also identified gender as an important moderating variable for technology usage. Empirical researches have shown that males and females have different interpretations of TAM factors (Gefen and Straub, 1997) and that gender is an important predictor for electronic transactions (Al-Gahtani, 2011). Gender influence decreases as a technology’s use diffuses over time (Zhou, Dai and Zhang, 2007). A research carried out by Hill, Beatty and Walsh (2013) on online users also found that there was no difference among genders with regard to online shopping. However, a research carried out using UTAUT2 by Lian (2015) on e-invoice use found that gender does play a moderating role between facilitating conditions and BI as well as social influence and BI.
Experience
The amount of knowledge a person has through practice is called experience (Venkatesh and Davis, 2000). Experience is the moderator for the positive relationship between facilitating conditions, hedonic motivation, habit, and behavioural intention factors of UTAUT2 (Venkatesh, Thong and Xu, 2012). Previous experience of using a specific technology has a positive impact on its future acceptance and use (Lu, Yu, Liu and Yao, 2003). For example, mobile Internet users that have experience will more easily embrace the use of mobile Internet (Fuksa, 2013). Experienced Internet users are also less worried about security matters (Korgaonkar and Wolin, 1999). However, individuals that have lower use of a technology have less interest in using it in the future (Stanley, 2003).
Summery and Discussion
Perceived risk has not been included in the original UTAUT2 model as it is associated with security and privacy concerns. Security and privacy have been grouped together in many studies (Nasri and Charfeddine, 2012), and they are closely related. The availability of e-commerce has created an awareness of the importance of security and privacy (Azab, 2012). A recent study of Generation Y consumers in India have found that security and privacy are of major concerns in online shopping repurchase (Trivedi and Yadav, 2018). It is similar to the government/legal infrastructure of the Model of Diffusion Global E-Commerce.
The security and privacy factor is originally not included in UTAUT as it is considered a factor that can hinder the adoption of a technology. However, there is a difference between the security and privacy construct and the performance expectancy or facilitating conditions. The security and privacy construct refers to whether a website has sufficient security features and the assurance that the customers’ personal information will not be shared with unauthorised parties (Wen, Prybutok, Blankson and Fang, 2014). Performance expectancy refers to whether a person perceives that a technology can improve his or her competency (Venkatesh et al., 2003). An empirical UTAUT study shows that the security and privacy construct hinders performance expectancy (Xu and Gupta, 2009).
Facilitating conditions refer to the level to which a person perceives organisational and technical support has been given for the use of a technology (Venkatesh et al., 2003). This factor or construct is to identify the variables that promote the use of a technology. The security and privacy concerns refer to a specific aspect of facilitating conditions regarding a user’s interpretative opinions of the service provider’s policy on managing private information. Therefore, enhanced security and privacy do have a positive relationship with BI (Shin, 2010).
As mentioned earlier, Venkatesh, Thong and Xu (2012) have suggested the inclusion of other constructs in the model depending on the research context. Trust is a subjective belief regarding whether an individual will meet his or her commitments, and it is more important in a virtual environment because of the relative lack of social cues and transparency (Zhou, 2012). In the backdrop of this uncertainty of doing business online, an increase in trust can reduce the perception of risk (Gefen, Karahanna and Straub, 2003). For first-time online users, trust is even more critical to try out the service (Lindgren, 2015). A recent study of Generation Y repurchase on online commerce in India found that trust is an important factor (Trivedi and Yadav, 2018).
The trust construct is not included in the original UTAUT2 model although it is an important construct and widely recognised for the diffusion of e-commerce applications. Many studies on TAM have included the trust factor and shown that it has a strong relationship with BI (Valentine and Powers, 2013). Trust is linked with reliability (Miller and Batchelor, 2008) and is similar to the reliability factor of SERVQUAL.
Trust has been applied to numerous UTAUT and UTAUT2 research applications. In a research on Spanish online consumers, risk and trust have been added to UTAUT2 (Pascual-Miguel, Agudo-Peregrina and Chaparo-Pelaez, 2015). A research on online consumer purchase of tickets, perceived trust and consumer innovativeness have been added to better understand the extent of a wide range of influencing factors. It has also been included to explain the online motivators of consumers’ purchase of airline tickets (Escobar-Rodriguez and Carvajal-Trujillo, 2013). Trust is also added as a predictor of UTAUT2 in its application on the study of adopted mobile payment gateways (Slade, Williams and Dwivedi, 2014). The addition of trust as a single construct instead of multiple constructs has been shown to be parsimonious in many studies (Slade, Williams and Dwivedi, 2014) despite its positive association with security and privacy (Costante, Hartog and Petkovic, 2015).
Conclusion
The researcher was able to identify that Generation Y has a strong association with social networking and mobile marketing. As the focus of this research is on Generation Y, the sections on baby boomers, Generation X, and Generation Z were later removed.
In order to identify Internet commerce adoption models, the research questions were based on the researcher’s experience as an educator and a practitioner of Internet marketing. With this experience, the researcher reviewed existing theories that he knows and has gained with experience as a practitioner. Quality research is based on applying previous research theories to establish current research for interpretation. This is carried out by summarising and analysing the theories and identifying the research gaps.
As the main adoption theories have been identified for conventional marketing, further literature review was narrowed down to keywords such as e-commerce, electronic commerce, digital commerce, digital marketing, and internet marketing. By using these keywords, terms such as customer relationship management (CRM), supply chain management (SCM), and enterprise resource planning (ERP) have been associated.
For each diffusion model, each factor was searched against the search engines mentioned above. For example, after an extensive review, the UTAUT2 model was identified as the most robust technology adoption model.
For this research, saturation was reached when the same references were cited in journals and books and no new related information was found. Nevertheless, as the interactions between Canadian Generation Y and Canadian small business retail websites happen in a dynamic environment that continues to change, the researcher continued to update new material every year, especially publications ideally within the last two years to remain current.
There is still a lack of integrated studies on Generation Y’s usage of the retail websites of small businesses in Canada. Current research studies are somewhat fragmented in explaining the factors that contribute to the growth of Internet commerce, not to mention the lack of research studies on small businesses’ usage of retail websites.
References
- Agarwal, R. and Prasad, J. (1998). A conceptual and operational definition of personal innovativeness in the domain of information technology, Information Systems Research, 9(2), pp. 204–215.
- Ajzen, I. (1985). From intentions to actions: A theory of planned behaviour, in Kuhl, J., Beckmann, J. (Eds.), Action Control: From Cognition to Behaviour, Springer-Verlag, New York, NY. pp. 11–39.
- Ajzen, I. (1991). The theory of planned behaviour, Organizational Behaviour and Human Decision Processes, 50(2), pp. 179–211.
- Ajzen, I. and Fishbein, M. (1980). Understanding attitudes and predicting social behaviour, Prentice-Hall, Englewood Cliffs, New Jersey. pp. 59–61.
- Al-Gahtani, S. S. (2011). Modeling the electronic transactions acceptance using an extended technology acceptance model, Applied Computing and Informatics, 9(1), pp. 47–77.
- Amin, M. A. M. and Nayak, R. (2010). Theoretical model of user acceptance: In the view of measuring success in web personalization, International Federation for Information Processing, pp. 255–264.
- Andrade, E.B. (2005). Behavioural consequences of affect: Combining evaluative and regulatory mechanisms, Journal of Consumer Research, 32(3), pp. 355–62.
- Azab, N. A. (2012). The role of the internet in shaping the political process in Egypt, International Journal of E-Politics, 3(2), pp. 31–51.
- Babin, B. and Babin, L. (2001). Seeking something different? A model of schema typicality, consumer affect, purchase intentions and perceived shopping value, Journal of Business Research, 54(2), pp. 89–96.
- Belanche, D., Casalo, L. V. and Guinaliu, M. (2012). Website usability, consumer satisfaction and the intention to use a website: The moderating effect of perceived risk, Journal of Retailing and Consumer Services, 19(1), pp. 124–132.
- Bernadette, S. (1996). Empirical evaluation of the revised technology acceptance model, Management Science, 42(1), pp. 85–93.
- Bhattacherjee, A. (2001). Understanding information systems continuance: An expectation-confirmation model, MIS Quarterly, 25(3), pp. 351–370.
- Binde, J. and Fuksa, M. (2013). Mobile technologies and services development impact on mobile internet usage in Latvia, Organizaciju Vadyba: Sisteminiai Tyrimai, 26, pp. 41–50.
- Bogdan, R. C. and Biklen, S. K. (1982). Qualitative research for education: An introduction to theory and methods, Allyn and Bacon Incorporated, Boston.
- Bonera, M. (2011). The propensity of e-commerce research usage: The influencing variables, Management Research Review, 34(7), pp. 821–837.
- Brown, S. A., Dennis, A. R. and Venkatesh, V. (2010). Predicting collaboration technology use: Integrating technology adoption and collaboration research, Journal of Management Information Systems, 27(2), pp. 9–53.
- Chen, K. and Chan, A. H. S. (2011). A review of technology acceptance by older adults, Gerontechnology, 10(1), pp. 1–12.
- Chong, A. Y. L. (2013). Mobile commerce usage activities: The roles of demographic and motivation variables, Technology Forecasting Social Change, 80(7), pp. 1350–1359.
- Chu, K. M. (2013). Motives for participation in Internet innovation intermediary platforms, Information Processing and Management, 49(4), pp. 945–953.
- Chuttur, M. Y. (2009). Overview of the technology acceptance model: Origins, developments and future directions, Sprouts: Working Papers on Information Systems, 9(37).
- Costante, E., Hartog, J. D. and Petkovic, M. (2015). Understanding perceived trust to reduce regret, Computational Intelligence, 31(2), pp. 328–347.
- Creswell, J. W. (1994). Research design: Qualitative and quantitative approaches, SAGE Publications, Thousand Oaks.
- Creswell, J. W. (2003). Research Design: Quantitative, qualitative and mixed method approaches, SAGE, Newbury Park, California.
- Davis, F. D. (1989). Perceived usefulness, perceived ease of use, and user acceptance of information technology, MIS Quarterly, 13(3), pp. 319–40.
- Davis, F. D. (1993). User acceptance of computer technology: System characteristics, user perceptions, International Journal of Man-Machine Studies, 38(3), pp. 475–487.
- Davis, F. D., Bagozzi, R. P. and Warshaw, P. R. (1989). User acceptance of computer technology: A comparison of two theoretical models, Management Science, 35(8), pp. 982–1003.
- Denzin, N. K. and Lincoln, Y. S. (2011). The SAGE handbook of qualitative research, Fourth Edition, SAGE, Newbury Park, CA.
- Donepudi, P. K., Banu, M. H., Khan, W., Neogy, T. K., Asadullah, ABM., & Ahmed, A. A. A. (2020). Artificial Intelligence and Machine Learning in Treasury Management: A Systematic Literature Review. International Journal of Management, 11(11), 13–22.
- Dunn, H. S. (2009). From voice ubiquity to mobile broadband: Challenges of technology transition among low-income Jamaicans, 11(2), pp. 95–111.
- Easterby-Smith, M., Thorpe, R. and Lowe, A. (1991). The philosophy of research design, Management research: An introduction, SAGE Publications, London, pp. 21–43.
- Escobar-Rodriguez, T. and Carvajal-Trujillo, E. (2013). Online drivers of consumer purchase of website airline tickets, Journal of Air Transport Management, 32(C), pp. 58–64.
- Fishbein, M. and Ajzen, I. (1975). Belief, attitude, intention, and behaviour: An introduction to theory and research, Addison-Wesley, Reading, Massachusetts, pp. 500–578.
- Fuksa, M. (2013). Mobile technologies and services development impact on mobile Internet usage in Latvia, Procedia Computer Science, 26(1), pp. 41–50.
- Ganapathy, A., Ahmed, A. A. A., Siddique, M. NEA., (2021). Easy URLs in the Content Management System with Crawlers for Added Security. Academy of Marketing Studies Journal, 25(4), 1-10.
- Gefen, D. (2003). TAM or just plain habit: A look at experienced online shoppers, Journal of End User Computing, 15(3), pp. 1–13.
- Gefen, D. and Straub, D. (1997). Gender differences in perception and adoption of e-mail: An extension to the technology acceptance model, MIS Quarterly, 21(4), pp. 389–400.
- Gefen, D., Karahanna, E. and Straub, D. (2003). Trust and TAM in online shopping: An integrated model, MIS Quarterly, 27(1), pp. 51–90.
- Hernandez, B., Jimenez, J. and Martin, M. J. (2009). Key web site factors in e-business strategy, International Journal of Information Management, 29(5), pp. 362–371.
- Hill, W. W., Beatty, S. E. and Walsh, G. (2013). A segmentation of adolescent online users and shoppers, Journal of Services Marketing, 27(5) pp. 347–360.
- Hough, M. and Kobylanski, A. (2009). Increasing elder consumer interactions with information technology, Journal of Consumer Marketing, 26(1), pp. 39–48.
- Hsu, C. L. and Lin, J. C. C. (2015). What drives purchase intention for paid mobile apps? – An expectation confirmation model with perceived value, Electronic Commerce Research and Applications, 14(1), pp. 46–57.
- Hu, Q. and Dinev, T. (2005). Is spyware an Internet nuisance or public menace?, Communications of the ACM, 48(8), pp. 61–66.
- Hussain, S., Ahmed, A. A. A., Kurniullah, A. Z., Ramirez-Asis, E., Al-Awawdeh, N., Al-Shamayleh, N. J. M., Julca-Guerrero, F. (2021). Protection against Letters of Credit Fraud. Journal of Legal, Ethical and Regulatory Issues, 24(Special Issue 1), 1-11.
- Jayalgi, R. and Ramsey, R. (2001). Strategic issues of e-commerce as an alternative global distribution system, International Marketing Review, 18(4), pp. 376–391.
- Jensen, J. M. (2012). Shopping orientation and online travel shopping: The role of travel experience, International Journal of Tourism Research, 14(1), pp. 56–70.
- Johnson, B. and Christensen, L. (2008). Educational research: Quantitative, qualitative, and mixed methods approaches, (3rd edition), SAGE, Thousand Oakes, CA.
- Johnson, R. B. and Onwuegbuzie, A. J. (2004). Mixed methods research: A research paradigm whose time has come, Educational Researcher, 33(7), pp. 14–26.
- Karahanna, E., Agarwal, R. and Angst, C. M. (2006). Reconceptualising compatibility beliefs in technology acceptance research, MIS Quarterly, 30(4), pp. 781–804.
- Khan, W., Ahmed, A. A. A., Hossain, M. S., Neogy, T. K. (2020). The Interactive Approach to Working Capital Knowledge: Survey Evidence. International Journal of Nonlinear Analysis and Applications, 11(Special Issue), 379-393.
- Kim, W. C. and Mauborgne, R. (2005). Blue ocean strategy: From theory to practice, California Management Review, 47(3), pp. 105–121.
- Koenig-Lewis, N. and Palmer, A. (2014). The effects of anticipatory emotions on service satisfaction and behavioural intention, Journal of Services Marketing, 28(6), pp. 437–451.
- Koohikamali, M., Gerhart, N. and Mousavizadeh, M. (2015). Location disclosure on LB-SNAs: The role of incentives on sharing behaviour, Decision Support Systems, 17, pp. 78–87.
- Korgaonkar, P. K. and Wolin, L. D. (1999). A multivariate analysis of web usage, Journal of Advertising Research, 39(2), pp. 53–68.
- Laros, F. J. M. and Steenkamp, J. B. E. M. (2005). Emotions in consumer behaviour: A hierarchical approach, Journal of Business Research, 58(10), pp. 1437–1445.
- Leonardi, P. M. (2011). When flexible routines meet flexible technologies: Affordance, constraint, and the imbrication of human and material agencies, MIS Quarterly, 35(1), pp. 147–168.
- Lian, J. W. (2015). Critical factors for cloud-based e-invoice service adoption in Taiwan: An empirical study, International Journal of Information Management, 35(1), pp. 98–109.
- Lian, J. W. and Yen, D. C. (2014). Online shopping drivers and barriers for old adults: Age and gender differences, Computers in Human Behaviour, 37(1), pp. 133–143.
- Limayem, M., Hirt, S. G. and Cheung, C. M. K. (2007). How habit limits the predictive power of intentions: the case of IS continuance, MIS Quarterly, 31(4), pp. 705–737.
- Lindgren, S. (2015). Exploring consumer acceptance of software-as-a-service, Master Thesis, Hanken School of Economics, Helsinki.
- Lu, J., Yu, C. S., Liu, C. and Yao, J. E. (2003). Technology acceptance for wireless internet, Internet Research, 13(3), pp. 206–222.
- MacVaugh, J. and Schiavone, F. (2010). Limits to the diffusion of innovation: A literature review and integrative model, European Journal of Innovation Management, 13(2), pp. 197–221.
- Masrom, M. and Hussein, R. (2008). User acceptance of information technology: understanding theories and model, Kuala Lumpur, Malaysia: Venton Publishing.
- Miller, J. E. and Batchelor, C. (2008). Eliciting expectations to develop trust in systems, Proceedings of Human Factors and Ergonomics Society, 52nd Meeting.
- Mimouni-Chaabane, A. and Volle, P. (2010). Perceived benefits of loyalty programs: scale development and implications for relational strategies, Journal of Business Research, 63(1), pp. 32–37.
- Moon, J. W. and Kim, Y. G. (2001). Extending the TAM for a World-Wide-Web context, Information and Management, 38(4), pp. 217–230.
- Nasri, W. and Charfeddine, L. (2012). Factors affecting the adoption of Internet banking in Tunisia: An integration theory of acceptance model and theory of planned behaviour, Journal of High Technology Management Research, 23(1), pp. 1–14.
- No, E. and Kim, J. K. (2014). Determinants of the adoption for travel information on smartphone, International Journal of Tourism Research, 16(6), pp. 534–545.
- Ozkan, S. and Kanat, I. E. (2011). e-Government adoption model based on theory of planned behaviour: Empirical validation, Government Information Quarterly, 28(4), pp. 503–513.
- Park, Y., Son, H. and Kin, C. (2012). Investigating the determinants of construction professionals’ acceptance of web-based training: An extension of the technology acceptance model, Automation in Construction, 22(1), pp. 377–386.
- Paruchuri, H.; Vadlamudi, S.; Ahmed, A. A. A.; Eid, W.; Donepudi, P. K. (2021). Product Reviews Sentiment Analysis using Machine Learning: A Systematic Literature Review. Turkish Journal of Physiotherapy and Rehabilitation, 23(2), 2362-2368.
- Pascual-Miguel, F. J., Agudo-Peregrina, A. F. and Chaparo-Pelaez, J. (2015). Influences of gender and product type on online purchasing, Journal of Business Research, 68(7), pp. 1550-1556.
- Porter, M. E. (1979). How competitive forces shape strategy. Harvard Business Review, March/April.
- Porter, M. E. (1980). Competitive strategy: Techniques for analyzing industries and competitors, The Free Press, NY, New York.
- Porter, M. E. (1985). From competitive advantage: Creating and sustaining superior performance, The Free Press, New York.
- Rogers, E. M. (1995). Diffusion of innovations, Free Press, New York.
- Rogers, E. M. (2003). Diffusion of innovations, Fifth edition, Free Press.
- Sale, J. E. M., Lohfeld, L. H. and Brazil, K. (2002). Revisiting the quantitative-qualitative debate: Implications for mixed-methods research, Quality & Quantity, 36(1), pp. 43–53.
- Saunders, M. Lewis, P. and Thornhill, A. (2003). Research methods for business students, Third Edition, Financial Times/Prentice Hall, Upper Saddle River, New Jersey.
- Schoonenboom, J. (2012). The use of technology as one of the possible means of performing instructor tasks: Putting technology acceptance in context, Computers and Education, 59(4), pp. 1309–1316.
- Shih, Y. and Fang, K. (2004). The use of decomposed theory of planned behaviour to study Internet banking in Taiwan, Internet Research, 14(3), pp. 213–223.
- Shin, D.H. (2010). Analysis of online social networks: A cross-national study, Online Information Review, 34(3), pp. 473–495.
- Slade, E.L., Williams, M.D. and Dwivedi, Y.K. (2014). Devising a research model to examine adoption of mobile payments: An extension of UTAUT2, The Marketing Review, 14(3), pp. 311–336.
- Stanley, L.D. (2003). Beyond access: Psychosocial barriers to computer literacy, Information Society, 19(5), pp. 407–416.
- Sun, H. and Zhang, P. (2006). The role of moderating factors in user acceptance technology acceptance, International Journal of Human-Computer Studies, 64(2), pp. 53–78.
- Sutherland, E. (2016). The case study in telecommunications policy research, DOI, 18(1), pp. 16–30.
- Taylor, S. and Todd, P.A. (1995). Understanding information technology usage: A test of competing models, Information Systems Research, 6(2), pp. 144–176.
- Trivedi, S.K. and Yadav, M. (2018). Predicting online repurchase intentions with e-satisfaction as mediator: a study on Gen Y, VINE Journal of Information and Knowledge Management Systems, Volume 48, Issue 3, pp. 427-447.
- Vadlamudi, S., Islam, M.A., Hossain, M.S., Ahmed, A.A.A., Asadullah, ABM. (2021b). Watermarking Techniques for Royalty Accounts in Content Management Websites for IoT Image Association. Academy of Marketing Studies Journal, 25(4), 1-9.
- Vadlamudi, S.; Paruchuri, H.; Ahmed, A.A.A.; Hossain, M. S.; & Donepudi, P. K. (2021a). Rethinking Food Sufficiency with Smart Agriculture using Internet of Things. Turkish Journal of Computer and Mathematics Education, 12(9), 2541–2551.
- Valentine, D. and Powers, T. (2013). Online product search and purchase behaviour of Generation Y, Atlantic Marketing Journal, 2(1), pp. 76–91.
- Venkatesh, V. and Davis, F.D. (1996). A model of the antecedents of perceived ease of use: development and test, Decision Sciences, 27(3), pp. 451–481.
- Venkatesh, V. and Davis, F.D. (2000). A theoretical extension of the technology acceptance model: four longitudinal field studies, Management Sciences, 46(2), pp. 186–204.
- Venkatesh, V., Davis, G.B., Davis, F.D. and Morris, M.G. (2003). User acceptance of information technology: Toward a unified view, MIS Quarterly, 27(3), pp. 425–478.
- Venkatesh, V., Morris, M., Davis, G.B. and Davis, F.D. (2003). User acceptance of information technology: Toward a unified view, MIS Quarterly, 27(3), pp. 425–478.
- Venkatesh, V., Thong, J. and Xu, X. (2012). Consumer acceptance and use of information technology: Extending the unified theory of acceptance and use of technology, MIS Quarterly, 36(1), pp. 157–178.
- Wang, L. and Yi, Y. (2012). The impact of use contact on mobile payment acceptance: An empirical study in China, in Xie, A. and Huang, X. (Eds.), Advances in Computer Science and Education, Volume 140, pp. 293–299.
- Webb, T.L. and Sheeran, P. (2006). Does changing behavioural intentions engender behavioural change? A meta-analysis of the experimental evidence, Psychological Bulletin, 132(2), pp. 249–268.
- Wen, C., Prybutok, V.R., Blankson, C. and Fang, J. (2014). The role of e-quality within the consumer decision making process, International Journal of Operations & Production Management, 34(12), pp. 1506–1536.
- Wu, J. and Wang, S. (2005). What drives mobile commerce? An empirical evaluation of the revised technology acceptance model, Information & Management, 42(5), pp. 719–729.
- Xu, H. and Gupta, S. (2009). The effects of privacy concerns and personal innovativeness on potential and experienced customers’ adoption of location-based services, Electronic Markets, 19(2), pp. 137–149.
- Yang, K. (2010). Determinants of US consumer mobile shopping services adoption: implications for designing mobile shopping services, Journal of Consumer Marketing, 27(3), pp. 262–270.
- Yayla, A. and Hu, Q. (2007). User acceptance of e-commerce technology: A meta-analytic comparison of competing models, ECIS Proceedings, pp. 179-190.
- Zarmpou, T., Saprikis, V., Markos, A. and Vlachopoulou, M. (2012). “Modeling users” acceptance of mobile services, Electronic Commerce Research, 12(2), pp. 225–248.
- Zhou, I., Dai, I. and Zhang, D. (2007). Online shopping acceptance model – A critical survey of consumer factors in online shopping, Journal of Electronic Commerce Research, 8(1) pp. 41–62.
- Zhou, T. (2012). Examining mobile banking user adoption from the perspectives of trust and flow experience, Information Technology & Management, 13(1), pp. 27–37.
- Zhu, Y., Kamal, E.M., Gao, G., Ahmed, A.A.A., Asadullah, A., Donepudi, P. K. (2021). Excellence of Financial Reporting Information and Investment Productivity. International Journal of Nonlinear Analysis and Applications, 12(1), 75-86.
- Ziethaml, V.A., Parasuraman, A. and Malhotra, A. (2002). Service quality delivery through web sites: A critical review of extant knowledge, Journal of Academy of Marketing Science, 30(4), pp. 362–375.